Posted by George Wainblat
August 16, 2020
A growing number of organizations are counting on Ansible for their configuration management. In order to operate Ansible, you need a multitude of permissions on target machines, such as SSH keys and passwords – highly sensitive information that needs trustworthy protection.
Winner Takes All
For this exact reason, configuration management tools, such as Ansible, have become an attack vector as gatekeepers and aggregators of access and permissions to your workload environments; an especially lucrative target presenting a winner-takes-it-all prize.
Two Examples of Ansible Vulnerabilities
- The privileged Ansible admin access is vulnerable since it is not managed in a centralized way – a risky, error-prone management methodology that lacks permissions’ audit, monitoring and control – when someone leaves the organization their privileged access remains intact and vulnerable.
- Ansible, by default, keeps its encryption keys on its servers – already exposed. But there’s more. When a Secret is needed by the Clients it is sent by the Server encrypted. But, once the Secret reaches the Client it is saved in plaintext, leaving it completely vulnerable.
Use Akeyless to Better Protect Your Ansible Secrets, Identities, and Access
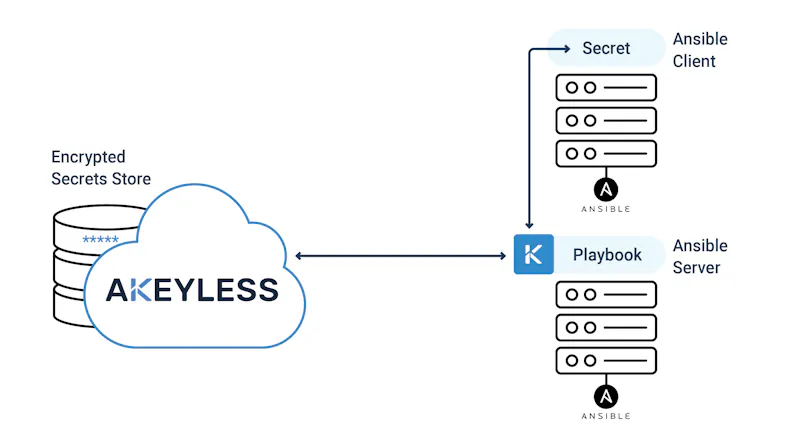
Akeyless’ secrets management platform adds complete protection to your Ansible Secrets by providing two extra layers of security:
1. Secrets Management
- Encrypting Secrets using decentralized encryption key fragments (Akeyless DFC technology)
- Segregation of Clients between different Ansible Playbooks and their Secrets
2. Privileged Access Management
- Using short-lived temporary access
- Easy to use and manage access with SSO
Benefits of Secrets Management with Akeyless Vault
- Seamless onboarding
- Unified, automated Secrets provisioning to all your DevOps platforms
- Zero-Trust encryption for all your Secrets
- Simplified compliance with industry regulations as ISO 2700X, HIPAA, FIPS, SOC2 and more
Akeyless automated, centralized secrets management relieves you of the hassle associated with secrets management while protecting your secrets with zero-trust encryption.
















