Posted by Miryam Brand
December 23, 2021
The recent KeyConf NYC’21 event featured a very interesting session, presented by none other than former Forrester analyst, Dr. Zero Trust, Dr. Chase Cunningham. He showed the audience how Zero Trust is sometimes overthought and when you apply the most important and fundamental Zero Trust steps, you start winning at security, in big numbers.
Zero Trust is no longer a mythical concept, and is becoming known even in the C-suite and boardroom. When asked why, the majority of security professionals say they see Zero Trust security as an essential model to be more proactive against sophisticated attacks. Implementing Zero Trust may seem like a complicated task, but it doesn’t have to be. As Dr. Cunningham indicated at KeyConf, like any problem, if you start fixing “the big stuff”, you are starting to win. This is also known as the 80/20 rule.
For Zero Trust, the “big stuff” starts with Identity Access Management (IAM). Zero Trust is identity centric, as compared to the old perimeter-based security approach. Perimeter-centric security is not granular enough, and in this era where most workers are remote, and workloads move from cloud to cloud, it is no longer relevant. And to focus again on the big stuff: 80% of security breaches started with compromised privileged credentials. If you take away your adversary’s ability to access your resources in the first place, you start to win, and at a very high percentage rate.
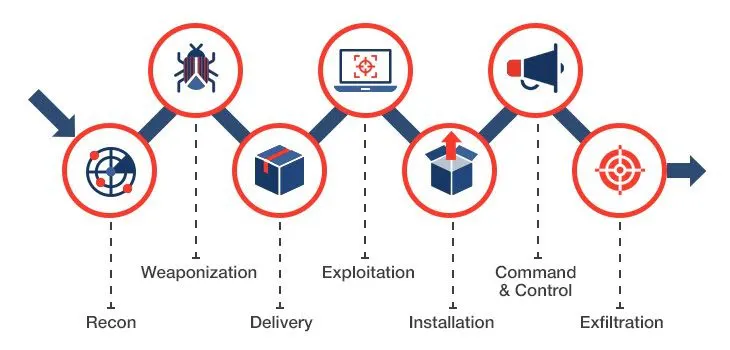
To better understand why this simple approach is so effective, we need to look at the killchain. The killchain is a set of steps an adversary has to go through to be effective at compromising your resources. The attacker’s weakness is that their attack strategy is only as strong as this chain’s weakest link. An attacker must get, and, more importantly, maintain control of the full killchain to be successful.
privileged sections of the network. Within the killchain, there are only certain steps you can actually control. The reconnaissance step, and the weaponization of a vulnerability is something that happens out there on the internet, conspired by hackers in dark web chat rooms. But the rest of it, you can control, and controlling access means you control the level of compromise.
Here are three simple, actionable steps to control access, and to summarize the core of Zero Trust as recommended by Dr. Cunningham:
- Justify access based on identity and role – Both machines and humans must justify who they are, and why they need access. For example, you wouldn’t just let anyone enter your house and let them roam about freely, just because they said their name is Mike. If it’s Mike, and he’s here to fix the plumbing, that’s another story.
- Just-in-time – Access should only be given upon request, and with the least amount of privileges possible. Going back to our example of Mike the plumber, he only needs access to the sinks and showers and such; he has no business in your office.
- Just Once – After a job is finished, or a reasonable set time for the job expires, the secret must be deleted and the whole process starts again, at the beginning. You don’t need Mike to stay overnight, and he doesn’t need to get back inside again when the plumbing is fixed.
Get just these three steps in place and you have achieved Zero Standing Privileges, and you are well on your way to winning.
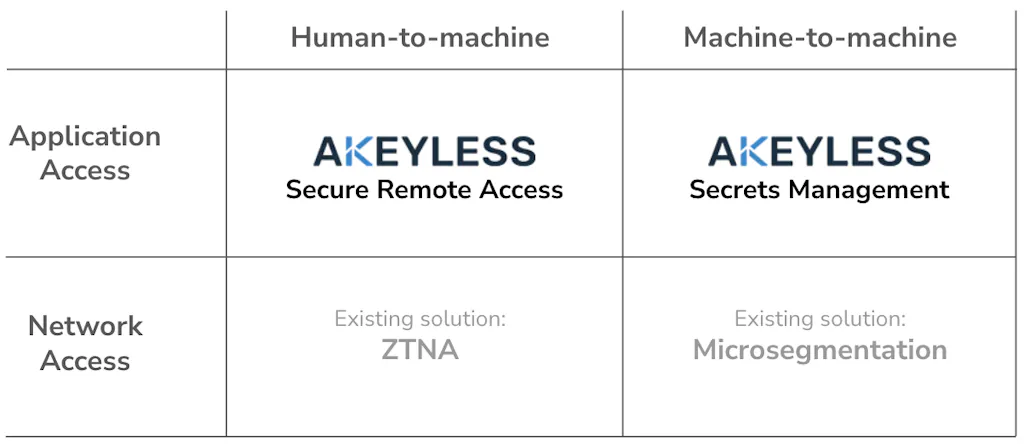
Unfortunately, existing IAM/PAM, and even ZTNA solutions, still focus on controlling the human access element at the network level, and do not cover application-level access control for both humans and machines. This is a real problem, as machine-to-machine communications are proliferating. Recent studies show that 80% of the SSH sessions are machine-to-machine communications. The Akeyless Vaultless Platform provides a unique, unified solution for both secure remote access and secrets management to help you control access for humans and machines, and to help you win.
Do you want to hear more about winning with Zero Trust? You can replay the entire session with Dr. Chase Cunningham here.














