Posted by Sam Gabrail
December 2, 2025
Akeyless vs Cyberark, that’s the topic of this post! Most teams do not plan to manage several tools for secrets, access, and certificates. It often starts with one need. A team brings in a secrets vault to store sensitive data. Then a second tool is added for privileged access. Later a certificate product is introduced for machine identity. Over time, the stack grows layer by layer.
Each new product brings a new workflow and its own policy model. Security becomes less about protecting credentials and more about handling the glue between tools. The more consoles and connectors that must be maintained, the more friction teams feel in daily operations.
Both Akeyless and CyberArk aim to reduce risk, but they do it in different ways. CyberArk spreads the solution across multiple products while Akeyless delivers one platform. When everything lives under a single control plane, security teams do not waste time stitching capabilities together.
Video Demo
Code Repo
https://github.com/samgabrail/akeyless-cyberark
Why This Comparison Matters
The main difference between the two platforms is not a single feature. It is the architecture. CyberArk requires separate products for secrets, privileged access, and certificate lifecycle. Each has its own admin layer and rollout path.
| Problem | CyberArk Product |
|---|---|
| Secrets for applications and workloads | Conjur |
| Privileged access for humans | CyberArk PAM |
| Certificate lifecycle | Venafi |
Using these together means running three different security stacks. Secrets stored in one place are disconnected from access management in another. Certificates live in yet another system. Teams must line up policies across tools to get a full audit trail.
Akeyless brings these under one control plane. Secrets, access, and certificates share the same UI, policy engine, and audit model. This removes time spent translating across products.
How CyberArk Got Here: Acquisitions and Silos
CyberArk expanded by acquiring separate products rather than building a unified platform.
| Year | Acquisition | Domain |
|---|---|---|
| 2017 | Conjur | Secrets |
| 2020 | Idaptive | Access |
| 2024 | Venafi | Certificates |
Each tool kept its own technology base. They are bundled together commercially, but not merged technically. This creates operational silos and slows deeper integration. When customers adopt one product, they still need to onboard teams again for the next.
Akeyless avoids this split because it began as a single architecture. There is no stitching step. This is why it can scale into more capabilities without multiplying overhead.
The Akeyless Platform at a Glance
Akeyless combines secrets management, Secure Remote Access, certificate lifecycle, and key management in one place. Everything runs behind the same trust boundary and the same policy layer. There is no separate onboarding cost when teams add more use cases.
The platform is built on Distributed Fragments Cryptography, which implements a zero knowledge design so even the provider cannot view encryption keys or other secrets. This is a strong security posture without extra infrastructure. Robust secrets management and securing secrets are critical for preventing unauthorized access and data breaches, and Akeyless enables effective secrets management practices to safeguard sensitive information.
Because all three pillars are unified, the platform works the same way across cloud environments, Kubernetes, and virtual machines. Teams avoid the jump between tools and do not need to maintain separate operations runbooks.
Secrets Management: Where Most Teams First Notice the Difference
When teams start using a secrets vault, the first big test is how well it works with real applications and Kubernetes. This is where the differences between the two platforms become very clear. What should be a simple and fast onboarding step often turns into extra work with multiple tools. Akeyless takes a cleaner approach by making this part easy from day one.
Kubernetes onboarding and secret delivery
Most teams first notice the difference when they begin onboarding applications and Kubernetes workloads into a secrets vault. With CyberArk Conjur, this step becomes harder because Conjur Cloud does not ship with a native Kubernetes Secrets Injector. Teams must bolt on extra integration steps to inject secrets into workloads, which slows adoption and increases the amount of operational plumbing required to keep secrets available across environments. What was meant to be a simple way to store sensitive data often turns into more setup work than expected.
Akeyless includes a native Kubernetes Secrets Injector by default, so secrets can be delivered to workloads without extra integration steps. This speeds adoption and reduces friction between security and platform teams. Onboarding also covers new credentials and service accounts, emphasizing secure secret creation and the need to control access to sensitive information.
Once the onboarding is smooth, the next major difference shows up in how secrets behave over time.
Dynamic secrets and secure migration paths
Dynamic secrets are another key gap. Akeyless supports a wide range of databases and cloud providers, while Conjur often falls back to static secrets for common services. When teams cannot automate secret rotation for a target, manual work or scripting fills the gap. Key rotation and the use of short lived secrets are essential for reducing the risk of compromised or stolen credentials.
Akeyless also helps teams migrate from AWS Secrets Manager or other secrets management tools without starting over. This is important when consolidating systems or stepping away from vendor lock in. AWS services, Google Cloud Platform, and other cloud providers are common sources for migration. Secrets can be improved while they are being moved, not after. Migration may also involve moving from HashiCorp Vault, other tools, and on premises environments, requiring comprehensive documentation and support for multiple programming languages.
For more detail, you can explore the Akeyless secrets management capability.
In Akeyless, secrets are not a standalone point solution. They are the first step into a unified platform that later adds access and certificate lifecycle without changing tools. A key feature of robust enterprise security is the ability to use secrets managers and a centralized secrets management platform to store secrets, manage access, and ensure compliance with industry standards.
The next gap: static vs dynamic credentials
Once onboarding is well underway, the next major limitation shows up in how secrets behave over time. With Conjur, coverage for dynamic secrets is limited across many common databases and cloud providers. This leads teams back to static credentials and manual rotation, which increases risk and adds maintenance overhead.
Dynamic secrets and automated rotation
Dynamic secrets are transforming the way organizations approach secrets management by enabling the creation of short lived, purpose specific credentials that are generated on demand. Unlike static secrets, which can linger in systems and become a target for attackers, dynamic secrets are issued only when needed and expire automatically, significantly reducing the risk of compromised credentials. This approach limits the attack surface and protects sensitive data even if a credential is intercepted.
Akeyless includes automated rotation for secrets such as database credentials, API keys, and encryption keys, which ensures that credentials are refreshed regularly without manual intervention. This helps organizations manage secrets more effectively and reduces the chance of expired secrets or forgotten credentials lingering in a production environment.
By leveraging dynamic secrets and built in automation, teams reduce operational overhead and shrink blast radius while improving the overall security posture of their CI/CD pipelines and application environments.
Access Management and Machine Identities
Once secrets are secured and rotated, the next question becomes who or what is allowed to use them. This is where most legacy approaches split identity into two different paths: one system for people and another system for workloads. That divide creates more policy surfaces to maintain and more review points during audits.
Modern infrastructure relies heavily on machine identities, not just user accounts. Workloads, CI pipelines, and services often require access without human presence, but traditional PAM tools focus almost entirely on privileged users. This leaves a coverage gap where automated systems rely on static credentials or separate tooling.
Akeyless treats access management for both humans and machines as part of the same platform. The same policy boundary that governs secret creation also governs who or what can use them. You can see how this extends to non-human identity in the Akeyless blog on
non-human identity management and universal identity.
This removes the need for separate trust systems and keeps machine identity and human identity aligned under one control plane, making just in time access a natural extension of secrets rather than a separate product.
Secure Remote Access: Modern PAM Without the Heavy Footprint
Once secrets are under control, the next gap usually appears in human access to sensitive systems. This is where traditional PAM solutions start to feel heavy. Older PAM models rely on shared admin accounts, long lived credentials, and jump servers. These patterns slow engineers down and increase risk by creating a single place where attackers can gain a foothold.
Jump hosts become high value targets because once they are compromised, everything behind them is exposed. These systems also add more moving parts for teams who already manage complex infrastructure. Instead of reducing the attack surface, they shift it into a bottleneck.
Akeyless Secure Remote Access removes this layer. Access is short lived by default, so there are no stored ssh keys or standing credentials. Sessions are recorded automatically and tied to identity. Users connect with native tools without going through a separate portal. This brings least privilege into daily workflow without extra friction.
For teams that want to understand how the approach works in more detail, check out the remote access overview.
This design treats access as part of secrets management rather than a separate system. Because everything lives in the same platform, there is no second policy engine and no second audit system to maintain. What used to require two products is now one.
Certificate Lifecycle Management in the Same Platform
The next part of the identity story is certificates. In the CyberArk world, certificates are handled by Venafi, which remains a standalone product with its own admin workflow. This means the lifecycle of certificates is disconnected from the lifecycle of secrets and access. When identity is split across tools, it becomes harder to track which system issued what and who owns the policy for it.
Akeyless keeps certificate lifecycle management inside the same platform that handles secrets and just in time access. This removes the overhead of wiring trust between tools. Issuing, renewing, and revoking certificates happens from the same console and the same API that teams already use for other identity functions.
ACME support lets workloads renew certificates automatically without manual touchpoints. Instead of wiring a separate service just for certificates, the same trust boundary that protects secrets also protects cryptographic keys used for TLS. This reduces the number of drifting components that can fall out of sync.
Because CLM is not separated from the rest of the platform, expiry risk goes down. Old or expired certificates are caught sooner because operators are already in the console for other daily tasks. This turns lifecycle management into part of normal platform operations instead of an extra module.
Compliance and Trust
Once secret rotation, remote access, and certificates share the same trust boundary, compliance improves as a natural outcome. Instead of pulling logs and audit data from multiple systems, everything lives in one place. Security teams do not have to reconcile reports or prove linkage between external vaults and access tools.
Short lived credentials reduce audit scope and show that the system limits exposure windows. Session logs for remote access are captured next to secret usage, so reviewers do not need to cross check two platforms. Certificates are also tied to the same identity model, so their lifecycle can be traced without a separate evidence trail.
The result is faster preparation for assessments and lower time spent collecting proof. This is not because of a single feature, but because the system stays unified end to end.
Hidden Costs and Day 2 Operations
When coverage is split across products, operational cost rises. Each upgrade is separate. Each support path is separate. Each onboarding requires its own process. Security teams handle policy drift. Platform teams handle integration drift. The weight accumulates over time.
When these functions move under one control plane, there is only one lifecycle to manage. This lowers the time spent maintaining glue code and reduces the number of touchpoints during incidents or audits. The platform becomes easier to run because it does not multiply itself as it grows.
This is why teams who start with secrets often end up consolidating PAM and certificate workflows into Akeyless as well. The unified footprint becomes easier to operate than stitching two or three separate solutions together.
Demo Walkthrough: Securing PostgreSQL End to End
This walkthrough shows how one platform manages everything around a PostgreSQL database. Instead of switching between different tools for secrets, certificates, and access, everything is controlled from the same console and the same policy boundary.
Step 1: On-Demand Dynamic Secret.
The demo begins in the Akeyless console under Secrets.
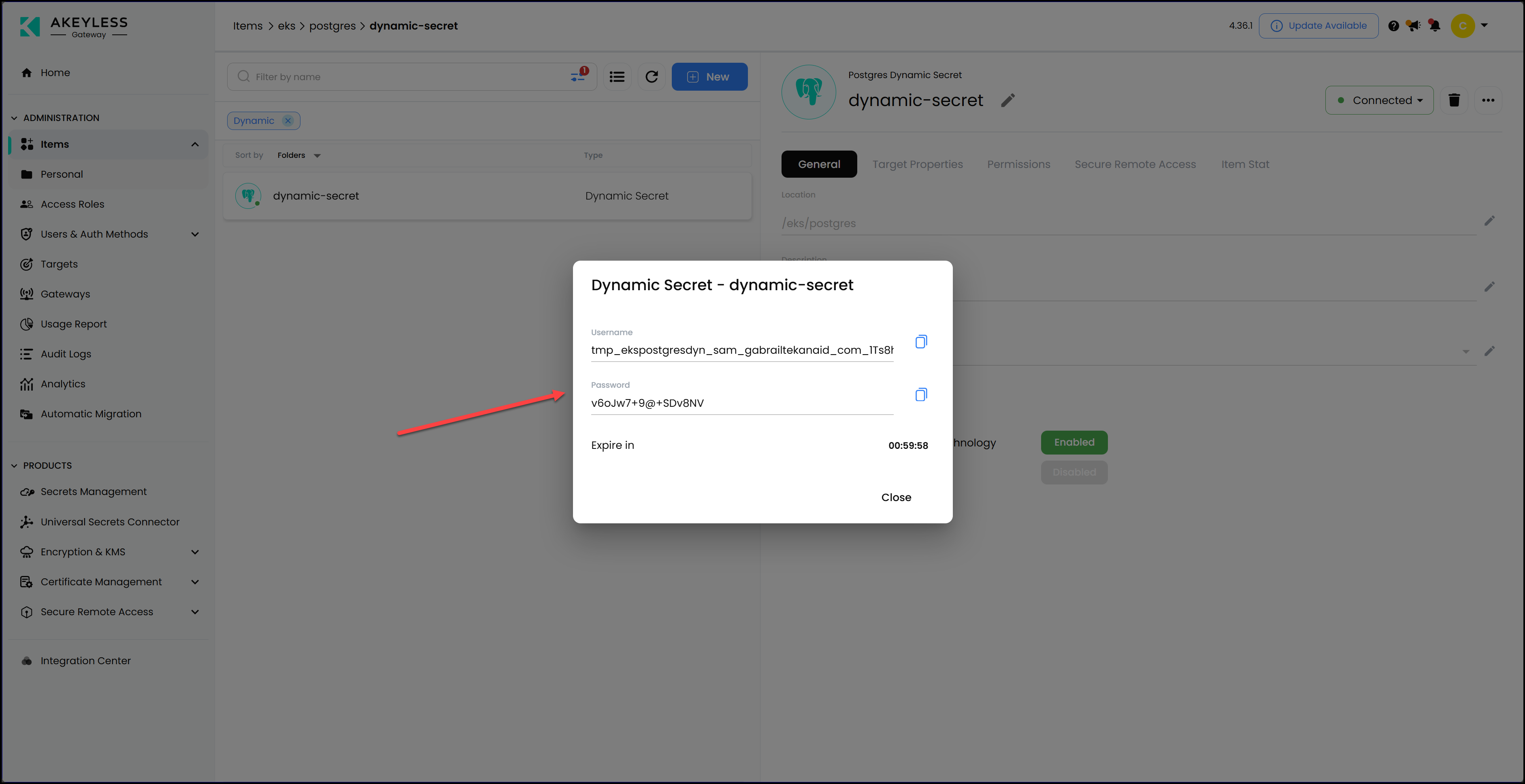
A dynamic Postgres credential is created on demand instead of being stored as a static password. This is the kind of credential an application or microservice would request at runtime to connect to the database, rather than loading a password from a secrets file or environment variable. The UI shows the short lease attached to it, along with the policy that governs its usage.
When the lease expires, the credential is revoked automatically. There is no manual cleanup and no leftover password that can be reused or stolen later. This pattern limits exposure and reduces the risk of compromised credentials lingering in a system. Below is a screenshot showing a newly created just in time dynamic secret with It’s time to live.
Step 2: Certificate Issuance from the Same Control Plane
Next, we stay inside the same console and navigate to the certificate section. The database is issued a TLS certificate through the same platform policy that governs secrets. There is no separate CA system to configure and no second product like Venafi to manage lifecycle tasks.
The workflow is consistent: request, issue, and govern from one place. Because certificates are part of the same trust model, renewal and revocation happen without extra infrastructure or parallel policy engines. Below is a screenshot showing how easily we can generate a PKI leaf certificate from an intermediate CA with a full chain of trust.
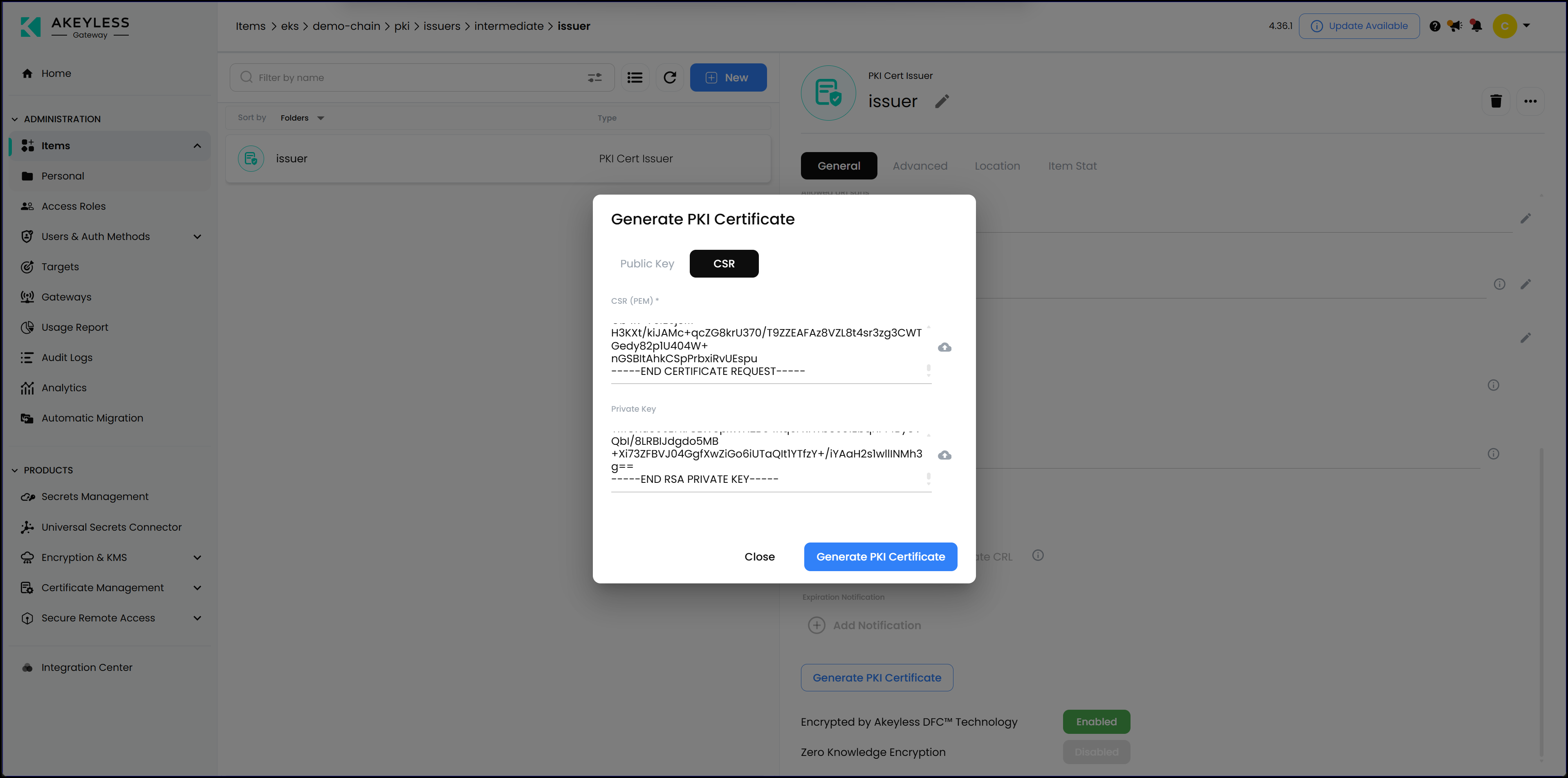
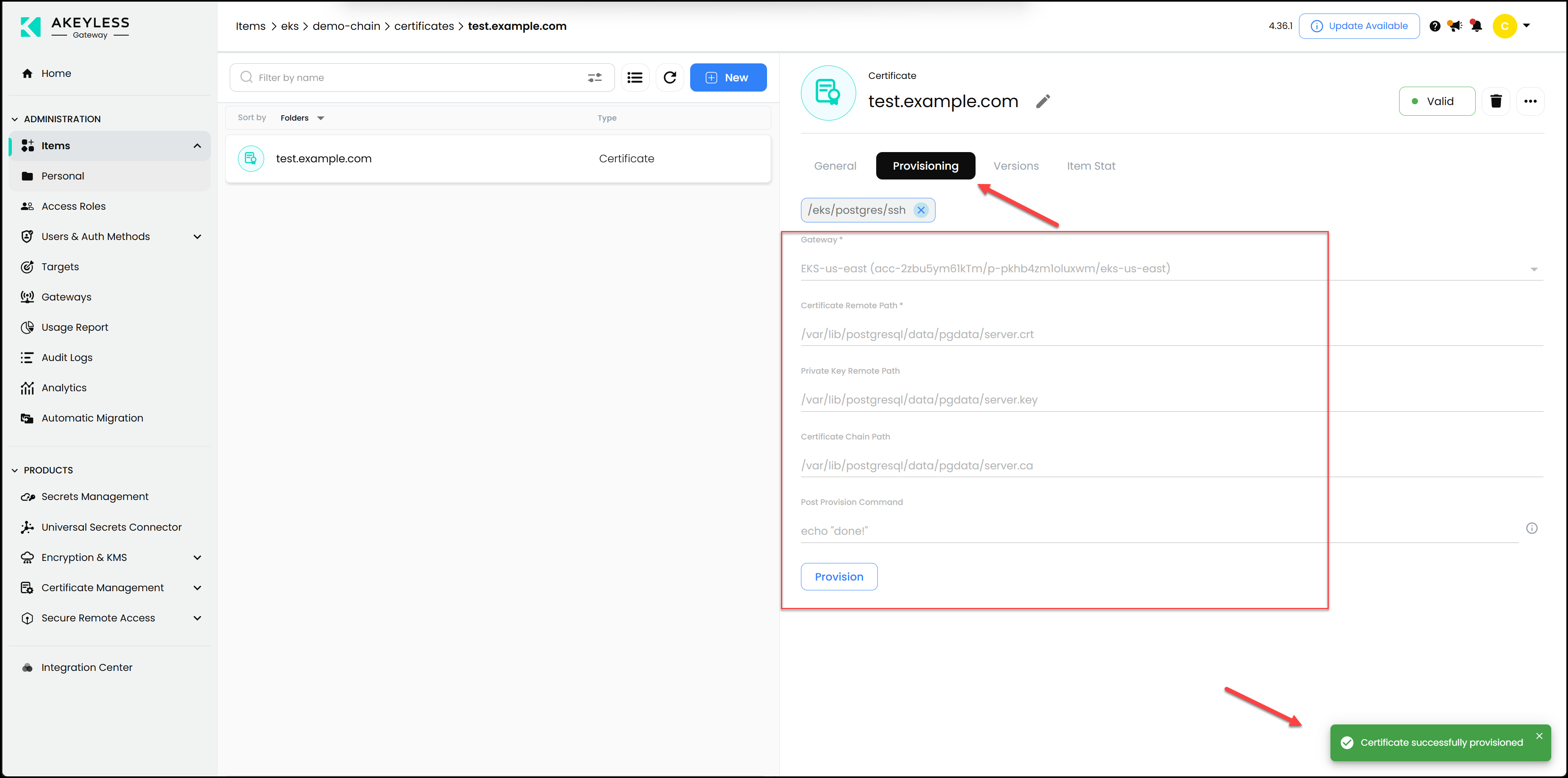
Not only that, but we can also go ahead and provision the certificate with the private key and CA directly on the PostgreSQL machine using secure remote access, which takes us to the next step: accessing the database securely.
Step 3: Just-in-Time Secure Remote Access
The third step is human access.
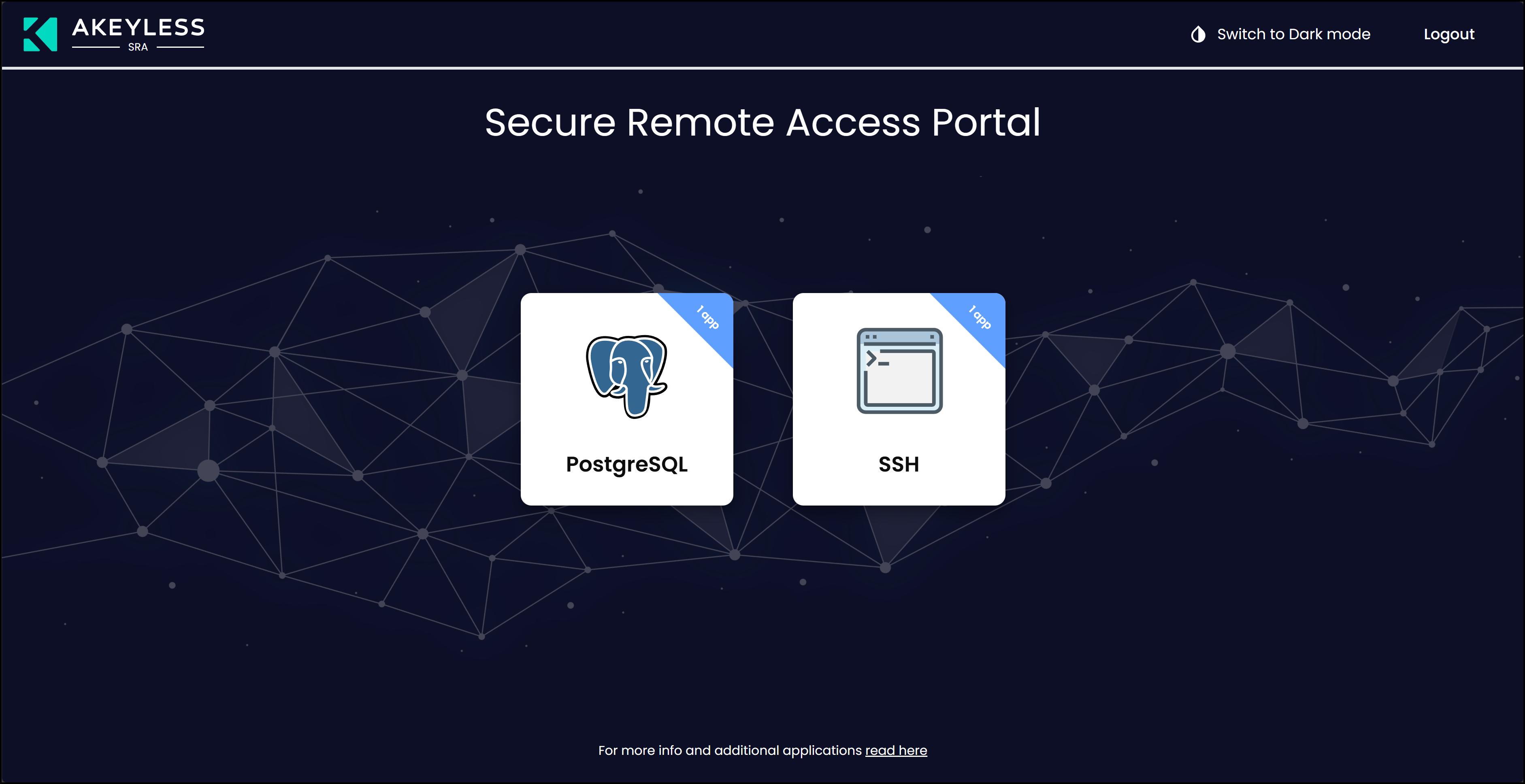
Instead of connecting by VPN or with a shared SSH key, the engineer launches a just-in-time session using Secure Remote Access. The platform issues a short-lived credential just for this connection and records the entire session in real time. When the engineer disconnects, the credential expires immediately.
This avoids standing privileges and makes privileged access auditable without a separate PAM product. Human access follows the same control plane used for application secrets and certificates. Below we see a screenshot of the Secure Remote Access Portal exposing two apps. One is to to our PostgreSQL database via a web interface and the other gives us access to that same database via SSH. When we login via SSH we get to see the certificates and private key we provisioned in the previous step.
Step 4: One Unified Audit Trail
The walkthrough ends in the Audit and Reporting view. The secret request, the certificate issuance, and the remote session all appear in the same log stream. They are covered by the same policy and tied to the same identity context. There is no need to reconcile logs across three different systems.
This unified audit makes it easier to prove policy enforcement and detect anomalies early. It also reduces operational overhead because the team manages one system instead of stitching together separate tools.
For session recording, we have the ability to view video recordings during an Remote Desktop Protocol (RDP )session. These recordings would be sent to an external storage system such as an AWS S3 bucket or an Azure Blob storage for long-term retention and review.
As for terminal based sessions such as SSH or database, a full transcript of commands entered are available. You can learn more about RDP and SSH Session Management in the docs.
Demo Conclusion
With one PostgreSQL database, the demo shows how secrets, certificates, and secure remote access can be managed in a single platform. The same control plane governs app-to-database authentication, machine identity, and human access. Nothing is bolted on or integrated after the fact. This is one lifecycle, one audit path, and one trust boundary.
Mini Comparison Table
| Need | Akeyless | CyberArk Stack |
|---|---|---|
| One UI and API | Single platform for secrets, access, and certificates | Separate consoles for Conjur and Venafi |
| Kubernetes onboarding | Includes a Kubernetes Secrets Injector | Conjur Cloud does not ship with an injector |
| Dynamic DB secrets | Broad coverage across major databases | Requires static secrets for many targets |
| CLM footprint | Built in with one policy model | Venafi is a separate product with its own admin path |
Summary
Most teams do not want several tools to handle secrets, access, and certificates. CyberArk brings these as separate products, each with its own setup and policy model. That gives teams more moving parts to run and more places where things can break or drift.
Akeyless puts secrets, short lived access, and certificate lifecycle in one platform. One control plane, one audit trail, and one policy layer. This simplifies operations, cuts onboarding time, and removes the glue work between systems.
The result is a security platform that grows with the team instead of weighing it down.
FAQ
What is the difference between CyberArk and Akeyless?
CyberArk splits capabilities across different products like Conjur and Venafi. Akeyless is one SaaS platform for secrets management, secure remote access, and certificate lifecycle management under one policy and one audit log.
What is CyberArk Conjur used for?
Conjur manages application secrets, but teams often need other tools for PAM and certificates. This means more consoles and more policy surfaces to manage.
What is a PAM solution?
Privileged Access Management controls privileged users and how they reach sensitive systems. Modern PAM removes standing access, issues short lived secrets for each session, and records activity for audit logs.
What is modern PAM with Akeyless?
Akeyless Secure Remote Access gives just in time access without VPNs or shared ssh keys. Sessions are recorded, access policies are unified with secrets, and everything runs in the same platform. Learn more:
What is a dynamic secret?
A dynamic secret is created on demand for a short time and then expires. It replaces static secrets and lowers risk for database credentials, API keys, and other sensitive data in production environments.
What does rotating secrets mean?
Secret rotation replaces credentials on a schedule or after use. Automated rotation with short lived secrets reduces the chance of compromised credentials and removes manual work.
What is certificate lifecycle management?
CLM issues, renews, and revokes certificates for secure communication and machine identities. With Akeyless, CLM runs in the same UI and API as secrets and access. Here are some details.




