
A DevOps-First Guide to Securing Machine Identities in a High-Risk, Regulated World

A DevOps-First Guide to Securing Machine Identities in a High-Risk, Regulated World

Discover how to secure AI agents across environments with identity-first secrets management from Akeyless.

Secure secrets & NHIs at scale. Get practical strategies to reduce risk & protect sensitive data in cloud/hybrid environments.

Discover the 4 essential pillars of secrets management that help financial institutions meet compliance standards.

This checklist outlines those stages so you can see where you stand and what the next steps look like.
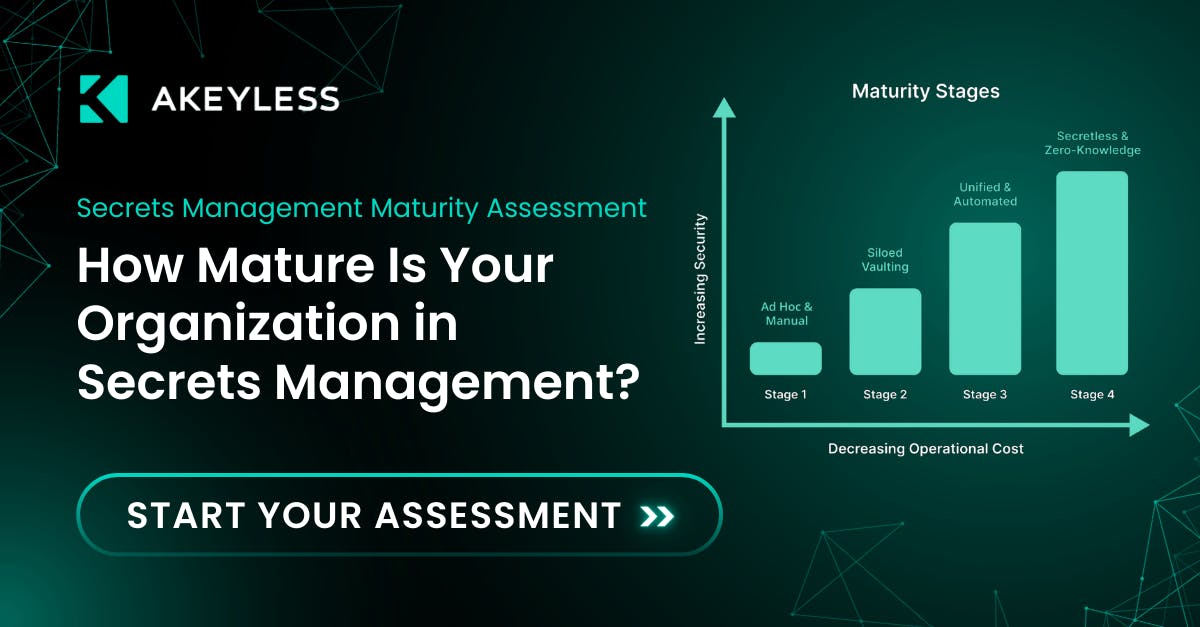
See how your team ranks and what it takes to reach secretless maturity.

Is your secrets management keeping up with modern security needs? Legacy tools may be holding you back.

Most organizations unknowingly leave gaps in their defenses, making them vulnerable to credential theft, privilege escalation, and lateral movement.

Close the gaps in your secrets management—before they’re exploited
Explore Akeyless secrets management on a self-guided product tour.

Learn why the Akeyless Vaultless® Platform is the leading alternative to CyberArk Conjur

Learn why the Akeyless Vaultless® Platform is the leading alternative to AWS Secrets Manager