Posted by Miryam Brand
June 1, 2022
Securing secrets requires continuous monitoring. It is essential to monitor access activity to ensure suspicious behavior does not go undetected. That’s why the Akeyless solution includes robust logging capabilities designed to track all secret access by identity, IP, action taken, and other common parameters.
Proactive Monitoring
It is also critical to alert your team proactively regarding suspicious activity. You can add this capability to your Akeyless solution by automatically forwarding Akeyless logs to a cloud monitoring solution. Cloud monitoring solutions allow you to set up ongoing alerts that respond to outlying behaviors tracked in Akeyless, ensuring that you are always informed of suspicious access or unusual activity.
Alerts and Your Workflow
How would this work? Let’s take a look at what you can do with an increasingly popular cloud monitoring solution, Datadog. With Datadog, you can easily choose which team members are alerted when suspicious activity occurs. This is accomplished by automated notifications sent via email, Slack, Jira or more. Screenshots of the actions associated with the suspicious behavior can be attached as needed.
When implementing notifications it is important to plan for how they will fit into your team’s workflow. To do this, ensure that:
- You have identified which outlying behaviors must be tracked.
- You have a plan in place for actions to take in response to outlying behaviors.
- The correct team member has “ownership” of notifications and is able to trigger the actions required to contain any threats.
Behaviors to Track
Use Datadog to set up ongoing alerts for abnormal behavior such as:
- A machine in the CI/CD pipeline asks for access permission at a time outside of business hours
- An entity – human or machine – tries to access an object outside of their permissions
- An entity attempts to implement an unusual privilege elevation
- The system reflects an unusual number of API calls or an unusual peak in resource usage. (Of course, you will need to define what “unusual” means based on your organization’s current usage pattern.)
Enabling Alerts with Datadog and Akeyless
Enabling Datadog notification from Akeyless is easy. All you need are a few simple steps:
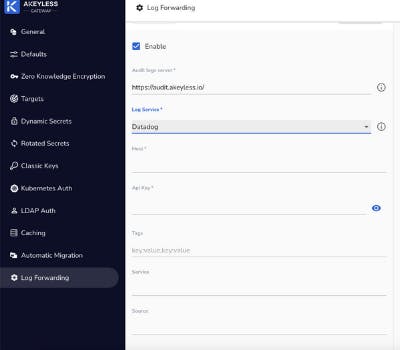
- Log in to the Akeyless Gateway and choose Log Forwarding in the side menu.
- Select the Enable checkbox.
- From the Log Service dropdown list, select Datadog.
- Define the Datadog host server.
- Define the Datadog API Key as received from Datadog.
Optionally:
- Define the Log Source name as it will appear in Datadog. The default name is “akeyless”.
- Define the Log Tags using key:value format. These tags will appear in Datadog.
- Define the Log Service as it will appear in Datadog. The default value is “akeyless-gateway”.
Now your Akeyless logs will automatically be forwarded to Datadog, where you can set up any notifications you prefer. Stay proactive and use the steps outlined in this blog post to ensure that the right member of your security team is always up-to-date.
Want to continue extending your Akeyless platform? Find a wide range of log services you can use with Akeyless here.













