Posted by Joyce Ling
March 2, 2024
In the rapidly evolving digital landscape of 2024, managing and securing secrets like API keys, database credentials, and other sensitive information has become paramount for businesses worldwide. Two leading solutions in this arena are Akeyless and AWS Secrets Manager. This post compares both, with a focus on how they cater to the needs of modern enterprises.
What is AWS Secrets Manager?
Akeyless Security is the company behind the Akeyless Platform, a SaaS-based Vaultless Secrets Management platform that simplifies protection of credentials, certificates and keys. It pioneered the Vaultless™ approach to secrets management that combines benefits of cloud-native SaaS with patented Distributed Fragment Cryptography™ (DFC) delivering ease of use, maintenance, scalability and deployment while enhancing security. Akeyless is trusted by leading Fortune 500 companies and global technology partners to deliver secrets management, encryption & KMS, password management, and secure remote access in multi-cloud environments.
What is Akeyless?
Akeyless Security introduces a SaaS-based Vaultless Secrets Management™ solution using proprietary technology. This platform addresses the management of secrets like credentials and certificates without traditional vaults, offering up to 70% cost reduction. It is designed for scalability in hybrid and multi-cloud environments, automating secrets management across the CI/CD pipeline. Akeyless emphasizes security with its patented Distributed Fragments Cryptography (DFC™), ensuring a Zero Knowledge approach. This makes Akeyless a trusted solution for companies, providing complete control over their secrets management needs.
Akeyless vs AWS Secrets Manager
Akeyless and AWS Secrets Manager both provide crucial secrets management services, such as secure storage and automated secret rotation. They enable versioning for keys and secrets, offer API integration for diverse applications, and ensure secure storage for sensitive data, underscoring a commitment to operational efficiency and security.
However, Akeyless differentiates itself with Vaultless™ technology, providing a centralized service for managing secrets across multiple clouds and on-premises environments. Its patented Distributed Fragments Cryptography (DFC™) ensures that organizations have exclusive ownership and access to their secrets, aligning with the highest security standards. Akeyless Zero-Knowledge mode further bolsters this by ensuring that only the customer can access their secrets.
Akeyless is engineered to support the dynamic nature of modern IT environments, offering extensive multi-cloud and hybrid support. It stands out in its ability to manage dynamic secrets and facilitate Just-in-Time access, providing temporary, time-sensitive credentials to reduce risks. With a broader range of authentication methods, Akeyless enhances connectivity options, fostering seamless integration with third-party tools and DevOps processes. This approach, coupled with its performance features like on-prem secrets caching and elastic processing, positions Akeyless as a more adaptable and efficient solution for contemporary secrets management needs.
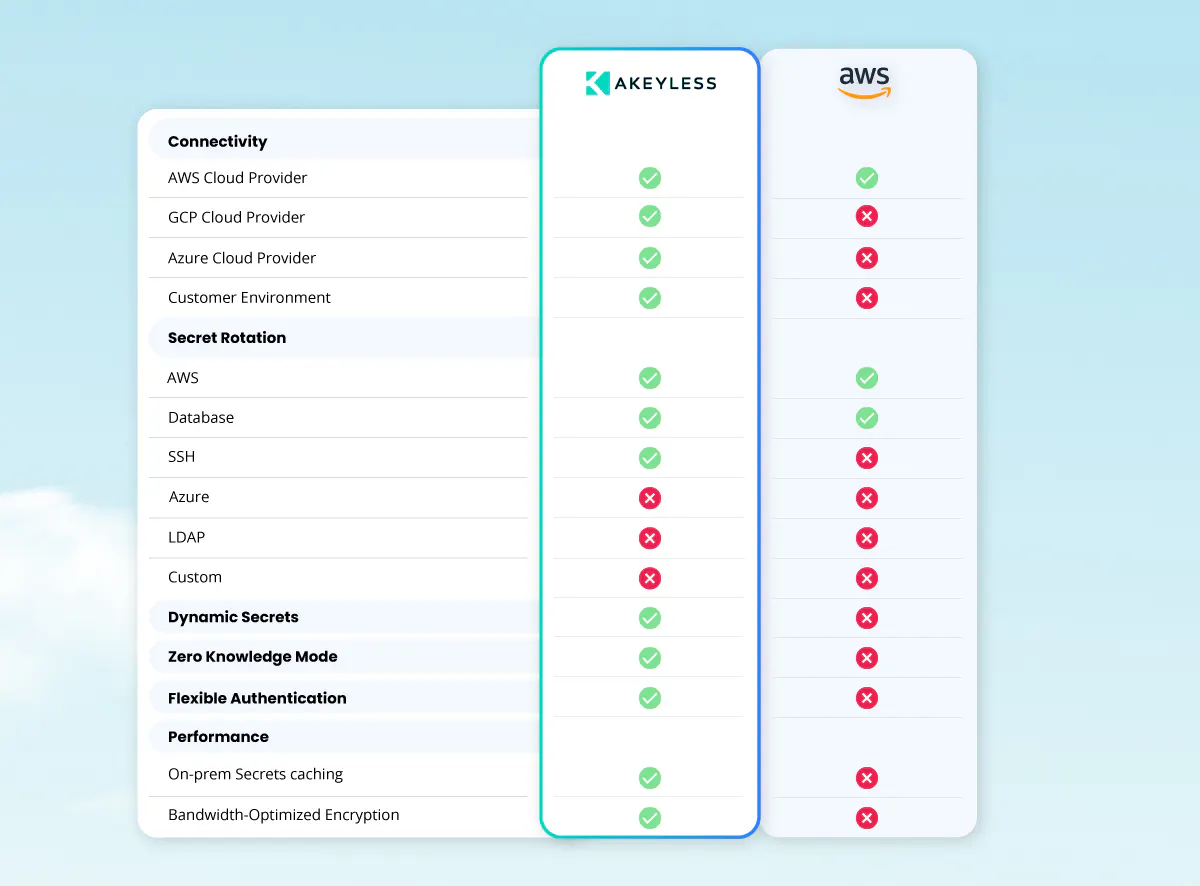
Let’s double-click into the major differences between Akeyless and AWS Secrets Manager.
Zero-Knowledge Mode
The patented Distributed Fragments Cryptography (DFC)™ of Akeyless underpins its Zero-Knowledge Mode, assuring that, unlike cloud service providers like AWS, only customers have full knowledge and control over their secrets. This patented technology sets Akeyless apart, providing an additional layer of security by preventing any third-party access, including from Akeyless itself. In contrast, users of services like AWS Secrets Manager may not have the same level of privacy, as AWS has the capability to access user secrets. Furthermore, under laws such as the CLOUD Act, AWS could be compelled to provide government agencies with access to this data without the user’s consent or prior notice. This potential vulnerability highlights the importance of Akeyless Zero-Knowledge Mode for businesses seeking to maximize the confidentiality and sovereignty of their sensitive information.
RESOURCE: Key Ownership in the Cloud: Using Zero Knowledge to Protect Your Data
Multi-Cloud, Hybrid, and Flexible Integration
Although cloud platforms like AWS have a comprehensive secrets solution, they are intended for secrets processes to run within that cloud platform. These solutions have poor connectivity to third-party platforms, such as other cloud platforms, self-deployed CI/CD tools, non-managed Kubernetes clusters and similar workload elements. This can create tremendous problems for DevOps teams who need to quickly develop applications that use multiple secrets on a minute-to-minute basis, with the ability to quickly inject secrets as needed.
In addition, 90% of large enterprises have adopted a multi-cloud infrastructure using an average of 2.6 public clouds, which shows the need for a secrets management platform that supports multiple cloud platforms. Akeyless has extensive support for all major cloud platforms and numerous integrations as well as connectivity to on-premise systems. This support ensures that Akeyless can serve as an effective DevOps-centric tool that serves as a single secrets management solution across an organization’s entire IT infrastructure, whether it’s cloud-native, hybrid, or multi-cloud.
Dynamic Secrets and Just-in-Time Access
Dynamic secrets play an essential role in strengthening security protocols. While AWS Secrets Manager provides dynamic secrets capabilities, its scope is mostly limited to AWS dynamic secrets. This could be a constraint for organizations that require a broader range of dynamic secrets across different platforms. Akeyless extends these capabilities significantly, offering Just-in-Time access to generate temporary, time-bound credentials. This approach ensures that credentials for databases, cloud services, and infrastructure automation tools are only available when necessary, greatly reducing the potential for credential theft or misuse and reinforcing the organization’s security posture.
Authentication Options
Authentication options are pivotal in secrets management, offering flexibility and user-friendliness. While AWS Secrets Manager provides conventional methods like SAML 2.0 and OAuth 2.0, Akeyless goes further by offering an extensive suite of authentication methods, including Kubernetes Auth, SSH Auth, Certificate-based authentication, LDAP/S Credentials, and the proprietary Akeyless Universal Identity.
This wide range of authentication options is particularly beneficial in scenarios where a DevOps team manages a hybrid cloud environment. For example, a container in AWS might need access to secrets stored in Akeyless using AWS IAM for machine identities. On the other hand, developers may need to access the same secrets through SAML or OIDC for human identities. Common use cases like this show the need for seamless integration and adaptability of secrets management platforms. Not only this, but the importance of having community plug-ins that ensure compatibility with third-party tools and services.
Secret Rotation
Akeyless offers comprehensive secret rotation services for a broad spectrum of technologies, including SSH, Azure, LDAP, and custom secrets. This capability allows for the automated rotation of all types of secrets, aligning with security best practices, compliance requirements, and minimizing the risk of unauthorized access.
Unlike Akeyless, AWS Secrets Manager’s secret rotation capabilities are more constrained, primarily focusing on AWS-based resources. AWS provides a managed lambda function for rotating secrets for RDS databases. For other types of secrets or custom applications, users must implement custom lambda functions to handle the rotation. This difference underscores Akeyless advantage in offering built-in, extensive support for secret rotation across a wider variety of technologies. You can do this without custom coding, ensuring a seamless and secure management of secrets across any environment.
Performance
Akeyless and AWS both offer scalable secrets management solutions designed for a broad range of performance needs. However, Akeyless takes a unique step further with its on-premise secrets caching. This feature significantly enhances access speed to secrets by leveraging local infrastructure, which is critical in high-load scenarios. While AWS provides robust and elastic services, Akeyless on-premise caching option presents an advantage if you are looking for immediate access to secrets with minimal latency. This makes it an appealing choice for enterprise-grade environments seeking optimized performance and security.
Screenshots and Videos
Akeyless is designed with users in mind. It’s built to support the dynamic needs of DevOps, highlighting an approach that balances feature-rich capabilities with straightforward usability. This focus ensures that every interaction is not just about managing secrets efficiently but also about enhancing the DevOps workflow. Akeyless streamlines complex tasks, making them more accessible and less time-consuming.
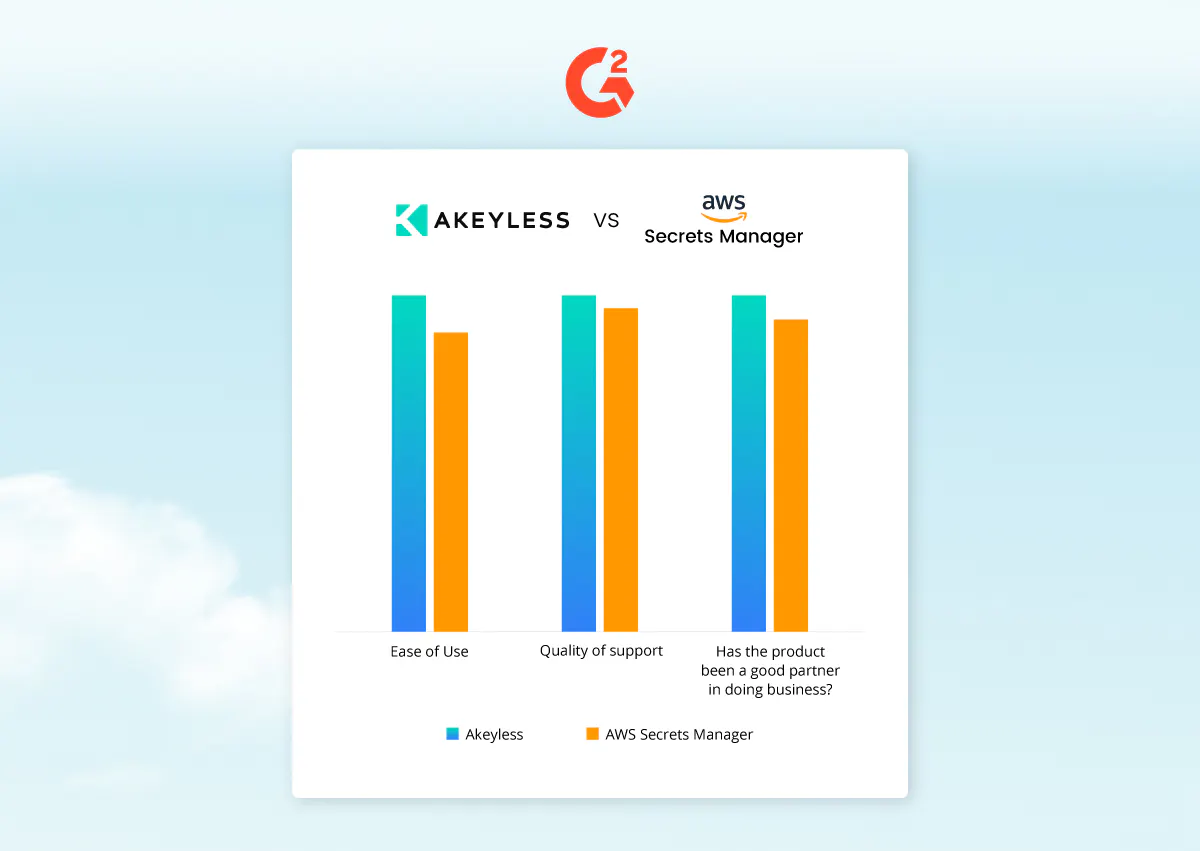
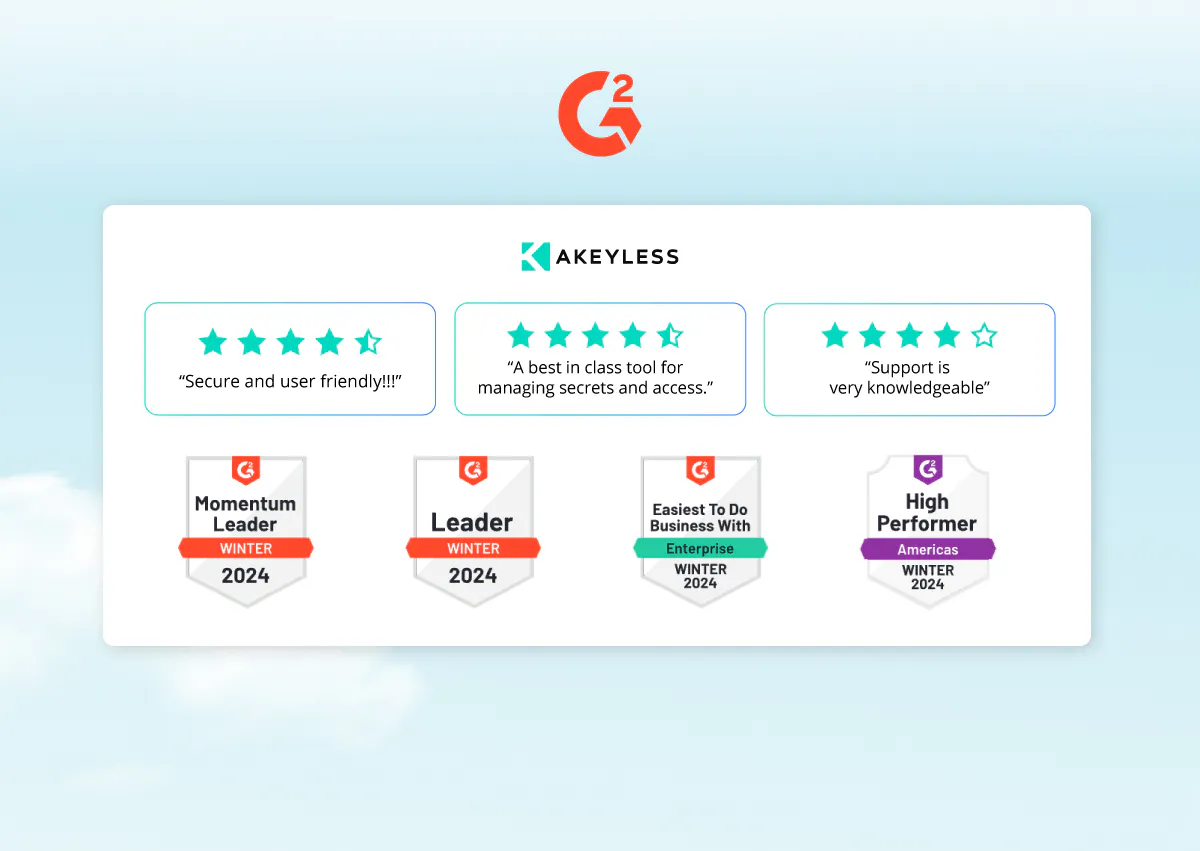
G2 Ratings Snapshot
G2 highlights Akeyless as a user-approved choice for effective secrets management. It showcases Akeyless Ease of Use, suggesting that users find the platform straightforward and simple to manage. Its Quality of Support stands out for being particularly helpful and accessible. One customer notes Akeyless as an “…extremely supportive and very engaging team. [They take] a detailed approach towards understanding the most important need of the customer.” The product’s future-focused direction also receives a nod, hinting at a strong roadmap that resonates well with user expectations.
Making the Choice: Akeyless or AWS Secrets Manager?
As you compare Akeyless and AWS Secrets Manager, it’s clear both can offer you strong secrets management solutions tailored to modern enterprise needs. AWS Secrets Manager excels within its ecosystem, perfect for those deeply integrated with AWS services. Akeyless, however, shines with its innovative Vaultless Secrets Management™. It offers significant cost savings, flexibility across cloud environments, and a secure, zero-knowledge approach.
The key lies in matching your organization’s requirements with the features each platform offers. For versatility and cutting-edge security, Akeyless presents a compelling option. For those embedded in the AWS ecosystem, its Secrets Manager provides robust, seamless integration.
Ultimately, the choice hinges on your specific needs. Are you prioritizing the advanced security and flexibility of Akeyless or the AWS-centric convenience of AWS Secrets Manager? This decision will be crucial in securing your digital assets effectively as we move forward in 2024.
About Akeyless
Leveraging proprietary Vaultless™ technology, Akeyless Security stands at the forefront of Secrets Management innovation with its state-of-the-art SaaS-based Vaultless Secrets Management™. The Akeyless platform takes on the demanding task of managing secrets—credentials, tokens, certificates, and passwords— while effectively phasing out conventional vaults and slashing associated costs by up to 70%. Designed for boundless scalability in hybrid and multi-cloud environments, the Akeyless platform efficiently controls secrets sprawl and automates secrets management for the entire CI/CD pipeline. The platform’s extensions also handle secure remote access, password management, and data protection. Leveraging patented Distributed Fragments Cryptography (DFC™), Akeyless champions a Zero Knowledge approach and is a trusted partner of many Fortune 500 companies. The Akeyless platform gives customers complete control over their secrets.
Get started with Akeyless
With Akeyless, you can easily get started. Check out our tutorial series, where you’ll set up your free account, get familiar with the web application and CLI, create and share your first secret, then create and rotate some encryption keys.
















