Posted by Anne-Marie Avalon
May 21, 2023
The LastPass breach serves as a pivotal moment in cybersecurity, drawing attention to the dangers associated with storing sensitive information in password managers and the increasing need for secrets management. The breach impacts 25 million users, and its consequences are far-reaching. Events like the LastPass breach underscore the urgent necessity for secrets management. Today’s cybersecurity must include a focus on the protection of secrets; keys, credentials and certifications.
Explore the increasingly critical role of secrets management and learn about the events and impact of the LastPass breach in this retrospective. And discover preventive measures to address such incidents, valuable insights for enhancing cybersecurity practices in secrets management and overall password security in this blog.
Preventive Measures and Lessons Learned
When news of a potential data breach at LastPass emerged, CEO Karim Toubba claimed that there was no evidence of any customer data breaches. However, a retrospective analysis later revealed that customer data was actually at risk during the incident. Understanding the details of this breach is crucial for improving defenses and safeguarding digital assets from potential cyber threats in the future.
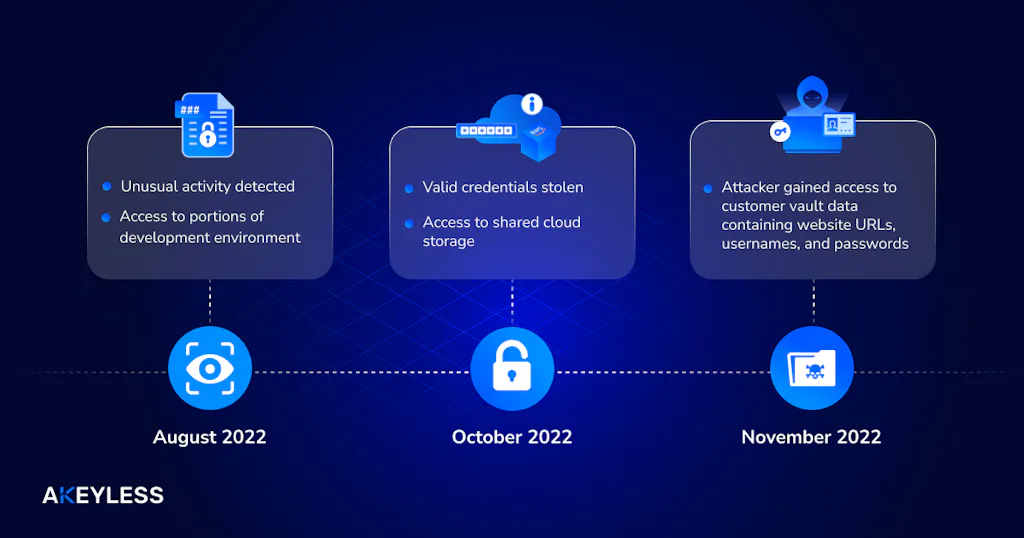
Breach Timeline: Connecting the Dots
According to The Verge, the attacker engaged in reconnaissance, enumeration, and exfiltration activities between August and October. They eventually stole valid credentials from a senior DevOps engineer, granting them access to shared cloud storage containing customer vault backup encryption keys in Amazon S3 buckets.
August Breach: The Beginning
LastPass first reported a security incident in August 2022 when they detected unusual activity within their development environment. They initiated an immediate investigation and found no evidence of the incident involving access to customer data or encrypted password vaults. LastPass discovered that an unauthorized party accessed their development environment through a compromised developer account and stole portions of source code and proprietary LastPass technical information. They concluded that their products and services were operating normally.
November Breach: The Intrusion
In November, LastPass announced detecting another intrusion that relied on information stolen during the August breach. This time, the attacker accessed specific customer information, including a backup of partially encrypted customer vault data containing website URLs, usernames, and passwords.
Targeting the DevOps Engineer: The Keylogger Attack
One of the four DevOps engineers responsible for the decryption keys made a critical mistake—storing those keys on his home computer. Unbeknownst to him, he became a prime target for the hacker stalking LastPass. The stage was set for a keylogger attack.
The hacker exploited a vulnerable third-party media software package to deploy keylogger malware, capturing the engineer’s master password and gaining access to the DevOps engineer’s LastPass corporate vault. Once the encryption key was in the attacker’s hands, they could access the organization’s most sensitive data.
The incident serves as a chilling reminder of the high stakes when security falters and secrets management falls short. As a result, end-users faced the risk of dangerous phishing schemes.
Impact on Users: The Risks of Hacked Encryption Keys and Compromised Vaults
The breach’s most alarming aspect is the unencrypted data accessed, including website URLs accessed with telephone numbers used for the MFA backup option. Cybercriminals could exploit this information to target specific users through phishing or other cyberattacks.
LastPass CEO Karim Toubba confirmed hackers obtained extensive customer data, including names, emails, phone numbers, and some billing info. A compromised vault’s security relies on encryption strength and the protective master password.
LastPass users should change their current master password to a unique one solely for LastPass, ensuring data safety and privacy.
The most critical data stolen were secrets; sensitive data such as encryption keys, credentials, and certificates that allow access to an organization’s secure resources. This was highlighted in their latest summary. Therefore, when attackers compromise secrets, they expose both the organization and its customers to severe risks. Attackers can use these secrets to access confidential information, manipulate systems, or launch further attacks, causing damage to reputations and financial loss.
Lessons Learned: The LastPass Breach and Secrets Management
The LastPass breach underscores the importance of prioritizing robust security measures for DevOps and InfoSec professionals. Implementing strong security practices can minimize risks and protect sensitive data. Proactive secrets management is a vital part of this process. Passwords, keys, and tokens are must be securely stored and managed throughout their lifecycle. Staying vigilant against threats and learning from incidents like the LastPass breach helps protect organizations and customers from severe cyberattacks.
Secrets Management: Strengthen Security and Prevent Future Incidents
Enterprises must adopt robust security practices to safeguard their secrets, including regular rotation of encryption keys, strict access controls, and secure storage solutions. Managing the life cycle of secrets reduces the risk of unauthorized access and minimizes the impact of potential breaches. Employee training and awareness programs are essential for promoting a culture of security. These measures can help strengthen an organization’s defenses and protect the valuable information customers entrust to them.
Akeyless Vault: A Stronger Defense Against Cyberattacks
Akeyless Vault, a SaaS secrets management solution, could have potentially prevented the LastPass hack with its Distributed Fragments Cryptography (DFC™) technology. DFC™ offers an advanced level of security, making it nearly impossible for attackers to gain unauthorized access to sensitive data.
- Eliminating the single point of failure
DFCTM technology maintains encryption keys in multiple fragments, which are distributed across different locations and never combined. Thus, attackers can’t decrypt data without all fragments.
- Enhanced access control
Akeyless Vault enforces strict access policies, allowing only authorized users and applications to access sensitive data. It limits engineers’ access to crucial keys, granting access only to privileged individuals. Standing privileges are eliminated as dynamic secrets expire automatically, making them useless if stolen. - Zero-knowledge encryption
Akeyless Vault uses zero-knowledge encryption with DFC™, ensuring Akeyless can’t access encryption keys or unencrypted data. This extra security layer means attackers can’t access unencrypted data even if they breach the provider’s infrastructure. - Continuous monitoring and alerting
Akeyless Vault continuously monitors and logs activities related to sensitive data access. Real-time alerts keep you aware of suspicious activities. This proactive approach could have helped detect and prevent unauthorized access to customer vault data in the LastPass case.
Akeyless Vault provides a secure solution for managing secrets and sensitive data by employing multiple measures. These measures include eliminating the single point of failure, enforcing strict access control, employing zero-knowledge encryption, and continuously monitoring and alerting. This comprehensive approach gives DevOps and InfoSec professionals greater peace of mind.
Conclusion: Choosing Akeyless Vault for Enhanced Security and Peace of Mind
The LastPass breach highlights the reality that even well-established security solutions can be vulnerable to cyberattacks. DevOps and InfoSec professionals must remain proactive in a world of relentless cyber risk. Staying ahead of the curve by adopting best practices to protect corporate and customer data is paramount.
Face challenges confidently with Akeyless Vault and its advanced DFCTM encryption. Security for peace of mind with robust access control, zero-knowledge encryption and continuous monitoring. Akeyless Vault secures sensitive data against cunning cyber threats.
Make the right choice. Trust Akeyless SaaS Vault. Stay proactive and secure in a world of ever-evolving cyber threats.
To learn more about the Akeyless Vaultless Platform, book a custom tour of the product today!
















