Posted by George Wainblat
October 26, 2020
Intro to tags
In information systems, a tag is a keyword or term assigned to a piece of information, like a digital record. This kind of metadata helps describe an item and allows it to be found again by browsing or searching. People use tags to aid classification, mark ownership, note boundaries, and indicate identity. Tagging gained popularity due to the growth of social bookmarking, image sharing, and social networking websites.
Akeyless Vault tags
We’ve recently added the ability to assign tags to any type of secret, such as encryption keys, static and dynamic secrets, and PKI & SSH certificates issuers. Each tag consists of a user defined case-sensitive string of an unlimited length. You can add the same tag to multiple Akeyless resources, or you can add the same item to a number of tags.
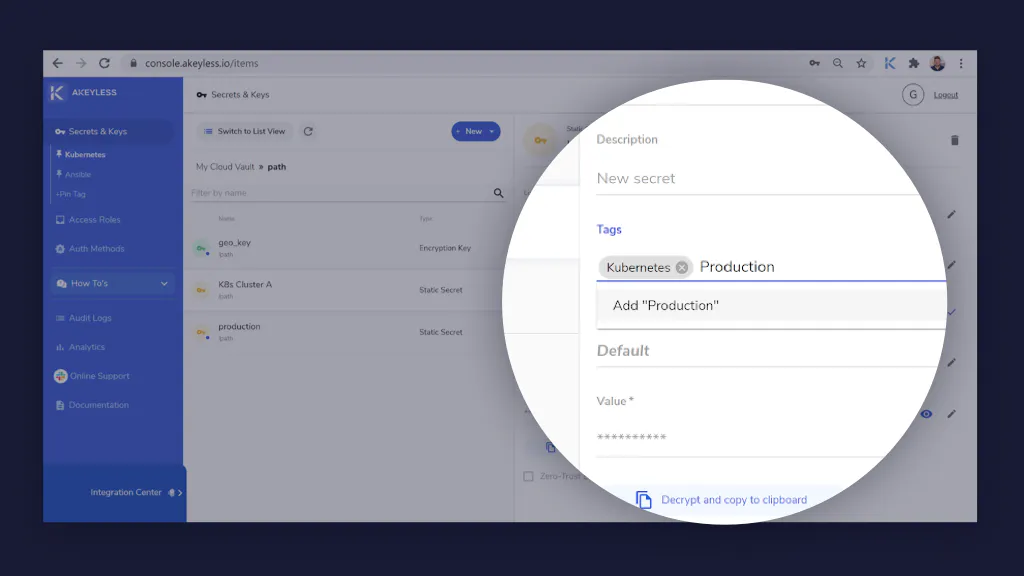
There are no limitations on the number of user-created tags each item can have. With Akeyless Vault secrets management, you can add tags to an item when you create it, or edit an existing item. Tags are shared per Akeyless Vault account, but the favorites (pin tags) are local per user.
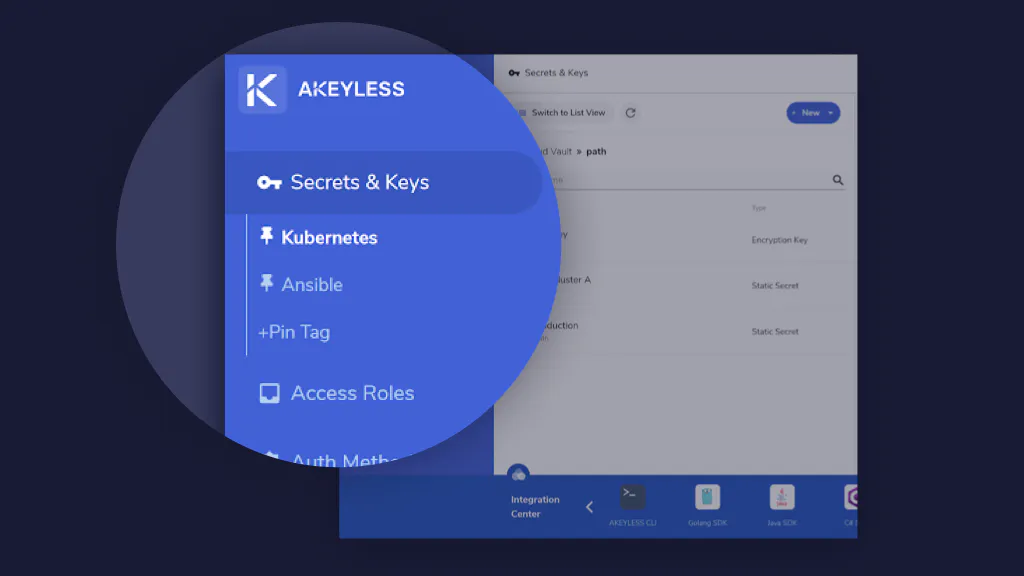
Tags help you do the following
Identify and organize your Akeyless Vault items. You can assign the same tag to resources from different folders to indicate that these items are related. You can also use tags via API to enhance automation.
Akeyless customers with an extensive number of secrets can use tags to designate certain items within Akeyless Vault, as personal favorites across multiple folders, sharing commonly used secrets between different team members, for projects currently in works.

















