Posted by Jeremy Hess
May 6, 2021
We’re really excited to announce our latest integration – the Akeyless Terraform Provider – to help our customers easily automate your security workload, starting from secrets creation to auth methods to role-based access control and much more.
Before we get into what this means for you, let’s talk a bit more about Terraform Providers.
What is a Terraform Provider?
According to their website “Providers are a logical abstraction of an upstream API. They are responsible for understanding API interactions and exposing resources.”
Basically, that means a Terraform Provider is a way for users of Terraform to easily add Terraform-specific code (HashiCorp Configuration Language) to interact with infrastructure and resources to assist in building replicated and automated infrastructure-as-code (IaC).

Akeyless Terraform Provider
The Akeyless Terraform Provider, therefore, offers Terraform users the ability to interact with our platform in a seamless manner. Some of the examples could be automating static or dynamic secrets, working with the API Gateway, creating authentication methods, and role-based access control.
For example, here is a piece of code for logging into the API Gateway:
provider "akeyless"{
api_gateway_address = "https://api.akeyless.io"
api_key_login {
// access_id = ""
// access_key = ""
}
}But, probably the most appealing feature of this implementation is automating Akeyless tenant creation and multitenant management directly from Terraform. Before we jump to how it’s done, we should discuss a bit about multitenancy.
What is Multitenancy?
The idea of a multitenant architecture is for a company to have their customers’ tenants all running and managed inside of a single instance of that application, and the tenants are segregated.
In this case, Akeyless Vault is the application. This means that our customers run on our SaaS application with segregated tenants. However, there is another layer to multitenancy for a customer using Akeyless.
In the context of this post, a tenant refers to a business unit within your organization. However, this can also be a project or even a single individual.
Managing Multitenancy with the Akeyless Terraform Provider
Trying to manage a global secrets management platform as a single user/team in a large organization doesn’t scale. The idea of multitenancy within Akeyless is to delegate administrative responsibilities to different business units. This is done by defining a sub-admin per tenant who has administrative access to create secrets, keys, auth methods, and access roles for that sub-org.
Multitenancy management of your Akeyless business units is a very powerful use case to apply with the Terraform Provider. So, what is the use case and how does it work?
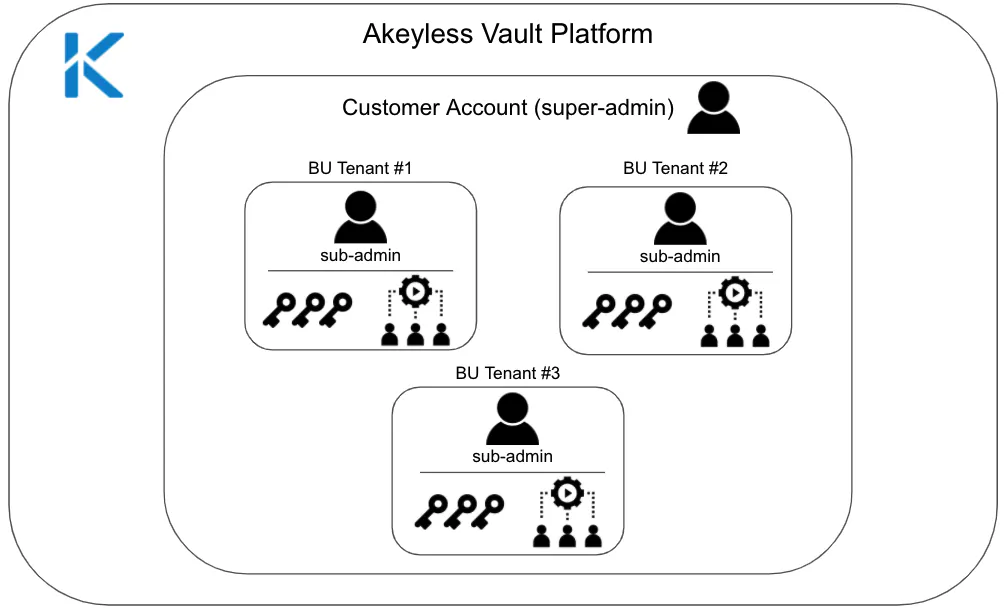
To make things simple, we will describe a generalized structure within an organization which will help visualize what is happening. We start with our super-user. This could be the head of security, DevOps group leader, or some similar role.
Sam is our super-user in the organization who delegates user identities, which are created and maintained through an authentication method of your choice – Akeyless supports Cloud Identities (CSP IAM, like AWS IAM, Azure AD, GCP IAM, etc), SAML, OpenID, and JWT – even LDAP for legacy environments.
Using the organization’s selected identity provider (IDP), Sam gives the VP R&D, Talia, permissions for Akeyless, making her the R&D tenant “sub-admin.” To get this done, all Sam had to do was add a bit of code into Terraform and hit “apply.” We’ll get into this code below.
Talia now has the ability to control her team’s roles within Akeyless through our role-based access controls. Moreover, if she leaves the organization, all Sam has to do is go into the identity provider and remove Talia from the system or switch the associated sub-claim to her replacement. That’s it – no more access.
Simple, but powerful. It’s all managed nicely within your Terraform script.
How to create tenants with roles using Akeyless and Terraform
The basic steps for adding a user with a role to Akeyless using Terraform is as follows:
- Install Akeyless as a provider in your Terraform Registry by adding the following code to your Terraform configuration (Terraform V0.13).
terraform {
required_providers {
akeyless = {
version = ">= 1.0.0"
source = "akeyless-community/akeyless"
}
}
}2. Run:
terraform init3. Select an Akeyless Authentication Method to use with the Terraform Provider, such as an API Key or Cloud Identity (CSP IAM) like AWS IAM, Azure AD, and so on. You may even use Akeyless Universal Identity if you’re using an on-prem machine, in order to avoid the inherit secret zero problem when using API Keys or locally stored tokens.
4. The following example creates an API Key authentication method called auth-method-saml-rnd in the rnd (/rnd/*) folder, a rnd-tenant-role role, and a user called “talia.” It uses AWS IAM for authentication.
terraform {
required_providers {
akeyless = {
version = ">= 1.0.0"
source = "akeyless-community/akeyless"
}
}
}
provider "akeyless" {
api_gateway_address = "https://api.akeyless.io"
aws_iam_login {
access_id = "YOUR AWS IAM access ID"
}
}
resource "akeyless_auth_method" "saml" {
path = "auth-method-saml-rnd"
saml {
idp_metadata_url = "https://Organization.okta.com/app/12345/sso/saml/metadata"
unique_identifier = "email"
}
}
resource "akeyless_role" "rnd-tenant" {
depends_on = [
akeyless_auth_method.saml
]
name = "rnd-tenant-role"
assoc_auth_method {
am_name = akeyless_auth_method.saml.id
sub_claims = {
"username" = "talia"
}
}
rules {
capability = ["read", "create", "update", "delete", "list"]
path = "/rnd/*"
rule_type = "item-rule" //secrets & keys
}
rules {
capability = ["read", "create", "update", "delete", "list"]
path = "/rnd/*"
rule_type = "role-rule" //access rules
}
rules {
capability = ["read", "create", "update", "delete", "list"]
path = "/rnd/*"
rule_type = "auth-method-rule" //auth methods
}
}
output "auth_method" {
value = akeyless_auth_method.saml
}5. Run:
terraform applyPutting it all together
In terms of secrets management for large enterprises, it is easy to see the inherent value in using a Terraform Provider to manage your Akeyless Vault tenants. Simply add a few pieces of code for the actions you would like to take and click “apply.”
Using Terraform and Akeyless together is a really fantastic way to create tenants, keep your users and secrets in order, ensure that no sensitive data is leaked, and always have your users up to date.
If you are interested in learning more about Akeyless Vault, contact us or get a demo today.
















