June 19, 2025
Posted by Sam Gabrail
How dynamic UID tokens and hierarchical management enable secretless non-human identity authentication for automated systems
Introduction
Non-human identity management has become one of the most critical security challenges facing security teams. While digital identity verification for humans is a much discussed security topic, non-human entities, from CI/CD pipeline runners to microservice containers, need to authenticate to digital systems just as much as human users do, often more frequently. Yet traditional approaches to managing these machine identities remain problematic: static API keys that never rotate, shared credentials across multiple systems, and manual secret distribution that doesn’t scale.
Unlike human identities, machine identities operate without direct human oversight, creating unique security challenges for access management. These digital identities require automated processes to perform tasks, access sensitive data, and interact with cloud services while maintaining robust security measures to prevent cyber threats and data breaches.
Enter Akeyless Universal Identity, an elegant solution for non-human identity security built around dynamic Universal Identity (UID) tokens. Unlike traditional approaches that rely on static credentials, Universal Identity provides a secretless token-based system with automatic rotation, hierarchical management, and enterprise-grade lifecycle controls that enhance security while eliminating security gaps.
This isn’t just another authentication method: it’s a fundamental reimagining of how non-human identity management should work in modern, secretless infrastructure to strengthen security posture and protect critical systems. Let’s dig in.
Demo Video
The Secret Zero Problem: Understanding Non-Human Identity Challenges
Before diving into solutions, we must address the fundamental challenge that has plagued non-human identity security for years: what security professionals call the “secret zero problem.”
What is Secret Zero?
Secret zero is the paradox of needing initial credentials to securely retrieve credentials. It’s the fundamental dilemma that every automated process faces: How do you provide the first secret without creating security vulnerabilities?
Consider this common scenario that illustrates the challenge. Your application needs database credentials from a secrets management system, but how does your application authenticate to the secrets management system? You need some initial credential (secret zero) to get other secrets, which creates a circular dependency for managing service accounts.
The Environment Divide
The secret zero problem manifests differently depending on your infrastructure environment, creating a significant divide in available solutions.
Cloud-Native Environments:
Modern cloud services provide elegant solutions to secret zero through built-in identity mechanisms. AWS offers IAM roles with instance profiles, Azure provides managed identities for compute resources, GCP delivers service accounts with metadata service integration, and Kubernetes implements service account tokens.
These platforms can verify machine identities without requiring pre-shared secrets, effectively solving the secret zero problem for cloud-native workloads.
Non Cloud-Native Environments:
Traditional environments present a much more challenging landscape because they lack native identity mechanisms. VMware VMs have no built-in identity service, physical servers lack cryptographic identity foundations, legacy systems require manual credential distribution, and on-premises infrastructure provides no metadata services.
The scale of this challenge is significant: an estimated 70% of enterprise workloads still run in these environments that lack native identity capabilities, making them prime targets for cyber threats.
Current Approaches Fall Short
Most organizations attempt to solve secret zero through traditional methods, but these approaches simply move the problem rather than solving it.
Traditional Solutions Still Require Shared Secrets:
The most common approaches include storing configuration files with hardcoded credentials on disk, using environment variables to pass static secrets in container or VM configuration, and relying on manual distribution where human users copy credentials between systems.
The fundamental problem with all these approaches is that they just move the secret zero challenge—they don’t solve it. You still need to securely provide that initial shared secret, creating security gaps and access management challenges that persist throughout the system lifecycle.
Introducing Akeyless Universal Identity
Let’s now see how Akeyless Universal Identity deals with the secret zero problem, especially for non cloud-native environments.
How Universal Identity Solves Secret Zero
The solution works through four key principles:
- Dynamic Credential Management: Replaces static, long-lived secrets with self-rotating UID tokens that minimize exposure windows
- Universal Application: Works across ALL environments—cloud, VMware, physical servers, and legacy systems (although Universal Identity should be used as a last resort if the application runs in an environment outside of Cloud and Kubernetes, where it’s much better to use the cloud-native authentication methods in Akeyless)
- Simplified Process: Reduces secret zero to a single, manageable credential that auto-rotates every 60 minutes by default
- Automated Lifecycle Management: Eliminates manual credential distribution and rotation processes entirely
The key insight driving this approach is a fundamental reframe of the problem: instead of trying to solve “how to securely distribute secret zero,” Universal Identity asks “how can we minimize secret zero to a single, self-managing credential?”
The Secretless Token-Based System
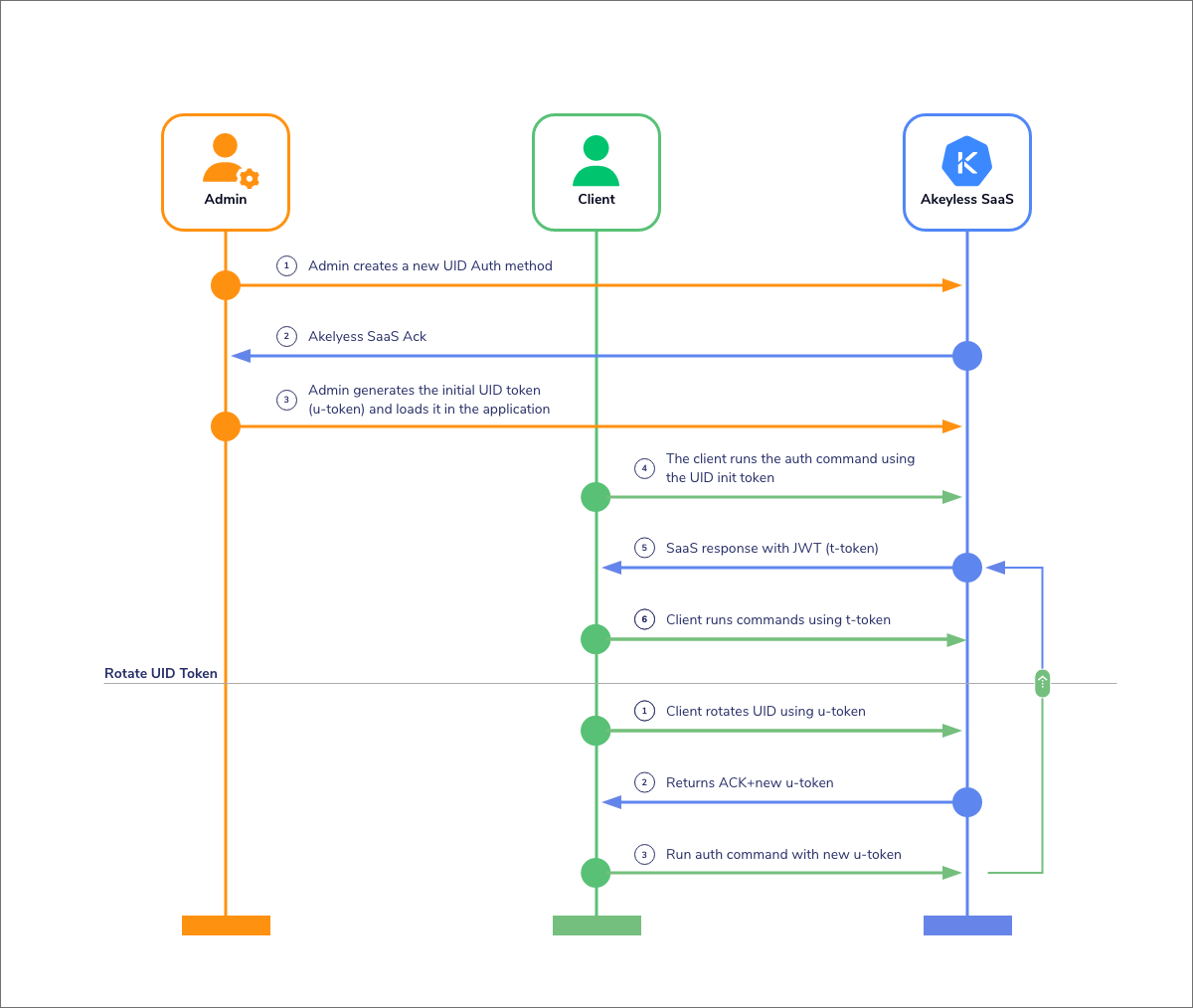
The diagram above illustrates the complete Universal Identity workflow, showing how the two-token system eliminates static credentials while maintaining robust security. Let’s walk through each step:
Step-by-Step Workflow Explanation
1. Initial Setup (Admin/Platform Engineer)
- An administrator creates a Universal Identity authentication method in Akeyless
- A UID token is generated and securely provisioned to the non-human entity (application, service, etc.)
- This is the only manual credential distribution step in the entire lifecycle
2. UID Token Storage
- The non-human entity stores its UID token securely (file permissions 600, encrypted storage, etc.)
- This UID token serves as the entity’s “identity card” – it can rotate without changing the underlying identity
- Default TTL is 60 minutes, but the token auto-rotates before expiration
3. Authentication Exchange (UID → T-Token)
- When the entity needs to access secrets, it presents its UID token to Akeyless
- Akeyless validates the UID token and issues a short-lived T-token (JWT format)
- This exchange separates identity verification from operational access
4. Secret Operations (T-Token Usage)
- The entity uses the T-token for actual API operations: retrieving database credentials, API keys, certificates, etc.
- T-tokens are optimized for high-frequency operations and have even shorter lifespans than UID tokens
- Multiple secret retrievals can use the same T-token during its validity period
5. Automatic Rotation Cycle
- Before the UID token expires, the entity automatically rotates it using the current token
- The old UID token is immediately invalidated, and a new one is issued with a fresh TTL
- This cycle continues indefinitely without human intervention
6. Hierarchical Management (Optional)
- Parent UID tokens can create child tokens for microservice isolation
- Different services get different TTLs based on their security requirements
- Revocation can be targeted (individual service) or cascading (entire application tree)
Key Security Benefits of This Workflow
The diagram demonstrates several critical security advantages:
- No Static Credentials: Unlike traditional API keys, nothing remains static in the system
- Time-Limited Exposure: Even if tokens are compromised, they expire quickly (60 minutes max)
- Separation of Concerns: Identity (UID) is separate from operations (T-token)
- Automated Lifecycle: The entire credential lifecycle is self-managing
- Audit Trail: Every token exchange and operation is logged for compliance
The key insight driving Universal Identity is this separation of concerns: UID tokens represent identity, while t-tokens represent sessions. This separation enables powerful secretless management capabilities while maintaining robust security measures and preventing unauthorized access.
Concept Clarification
Let’s now revisit some of the concepts we discussed but dig a bit deeper.
What “Secretless” Really Means
Now that we’ve introduced Universal Identity and UID tokens, let’s address a common question: “Secretless architecture still uses tokens. Aren’t those secrets?”
You’re absolutely right—UID tokens ARE secrets. But “secretless” doesn’t mean “no credentials at all.” It means eliminating static, long-lived, manually-managed secrets in favor of dynamic, short-lived, self-managing credentials that reduce security risks and security vulnerabilities.
Traditional Secrets vs. Secretless Architecture
To understand the difference between traditional secrets and a secretless architecture, let’s look at the examples below.
Traditional Approach (Static Secrets):
The traditional model relies on hardcoded credentials that remain unchanged for extended periods:
API_KEY="ak-12345678-static-forever"
DATABASE_PASSWORD="password123-for-6-months"
SERVICE_TOKEN="manual-rotation-maybe-never"This approach creates several critical security problems. Static credentials never change, meaning they’re stored permanently in configuration files. When rotation does happen, it requires manual intervention and coordinated updates across systems.
Most problematically, if these credentials are compromised, they provide long-term access to sensitive information until someone manually updates them.
Secretless Approach (Universal Identity):
Universal Identity transforms this model by using dynamic credentials that manage themselves:
# Dynamic, auto-rotating credentials
UID_TOKEN="u-AQAAADwAAAA..." # Rotates every 60 minutes automatically
T_TOKEN="t-874c497cbe4c..." # Short-lived session token (hours)This secretless pattern delivers significant security advantages. Dynamic credentials auto-rotate without human intervention, providing time-limited exposure with only 60-minute windows. There are no static secrets stored in application code, and the entire credential lifecycle is managed automatically.
Most importantly, even if credentials are compromised, the exposure window is minimal since tokens expire and rotate frequently.
The Hotel Key Card Analogy
Think of traditional secrets like master keys that work forever. If lost or stolen, they pose enormous security risks and require changing all the locks.
Secretless architecture is like hotel key cards that expire automatically, are replaced without human intervention, have limited access permissions scope, and minimize exposure if compromised.
The Initial Credential Challenge
Universal Identity doesn’t eliminate the need for an initial credential (you can’t). You need ONE initial UID token to start the process. However, it transforms this challenge by minimizing the security risks through intelligent design.
Here’s how Universal Identity handles the initial credential requirement. The initial setup requires one UID token to solve secret zero, but then the system becomes self-managing. The token rotates itself automatically every hour, eliminating the need for ongoing manual secret management.
Most importantly, even if this initial token is compromised, the blast radius is limited because it expires in just 60 minutes.
This approach represents a fundamental shift: instead of trying to eliminate initial credentials entirely, Universal Identity minimizes them to a single, self-managing credential that reduces long-term security exposure.
Core Components
Now let’s get technical and look at the core components of UID followed by access management for non-human identities, and some implementation patterns.
The Universal Identity Authentication Method
Universal Identity authentication method is one of multiple authentication methods that Akeyless offers. As I mentioned before, it should be used in cases where the application is running in a non-cloud-native environment. Below is how to create a Universal Identity authentication method via the CLI:
akeyless auth-method create universal-identity \
--name "/production/microservices" \
--ttl 60 \
--jwt-ttl 720UID Token Generation and Management
UID tokens serve as the non-human entities’ “identity card”—they can be rotated without changing the underlying identity, enabling true secretless architecture. The token management system provides several key capabilities for maintaining secure, automated operations.
Generating and managing these tokens follows a straightforward pattern:
# Generate initial UID token
akeyless uid-generate-token --auth-method-name "/production/microservices"
# Rotate token (resets TTL, invalidates old token)
akeyless uid-rotate-token --uid-token "u-XXXXXXXX"
# Create child tokens for specific services
akeyless uid-create-child-token --uid-token "u-XXXXXXXX" --child-ttl 30Each operation serves a specific purpose in the secretless architecture: initial generation establishes the identity, rotation maintains security through automatic refresh, and child token creation enables hierarchical access control.
Best Practice: Secretless UID → T-Token Workflow
The recommended secretless pattern implements a two-stage authentication process that separates identity from operations. This approach exchanges UID tokens for t-tokens for actual operations, implementing least privilege access principles.
Here’s how the workflow operates in practice:
# Non-human entity authenticates with UID token to get t-token
akeyless auth --access-id "p-xxxx" \
--access-type universal_identity \
--uid_token "u-XXXXXXXX"
# Use t-token for secret retrieval
akeyless get-secret-value --name "/production/database-creds" --token "t-XXXXXXXX"This secretless pattern provides several critical benefits for enterprise security. T-tokens are optimized for high-frequency operations, providing better performance than repeatedly using UID tokens. The security model uses short-lived t-tokens to minimize exposure windows, even if a session token is compromised.
Clear separation between identity and session operations enables comprehensive auditability and access tracking. Most importantly, all credentials remain dynamic and rotating, with no static secrets stored anywhere in the system.
Access Management for Non-Human Identities
Now that we’ve covered the key components and token workflows, let’s dig into how role-based access control can further simplify and secure non-human identities and give a couple of examples.
Role-Based Access Control for Machine Identities
Effective access management for machine identities requires implementing role-based access control (RBAC) and least privilege principles, but applied to the unique requirements of automated systems. Universal Identity provides hierarchical token management that enables organized access controls reflecting your actual organizational and operational structure.
The hierarchical approach allows you to model complex organizational relationships through token inheritance:
Parent UID Token (Application)
├── Child Token (Database Service)
├── Child Token (Cache Service)
└── Child Token (Notification Service)
├── Grandchild Token (Email Provider)
└── Grandchild Token (SMS Provider)This structure enables granular control while maintaining operational simplicity, allowing you to manage access at the appropriate level of abstraction for your organization.
Practical Hierarchy Examples
Real-world implementations of hierarchical token management typically follow either environment-based or service-based patterns, depending on your organizational needs and operational requirements.
Environment-Based Hierarchy
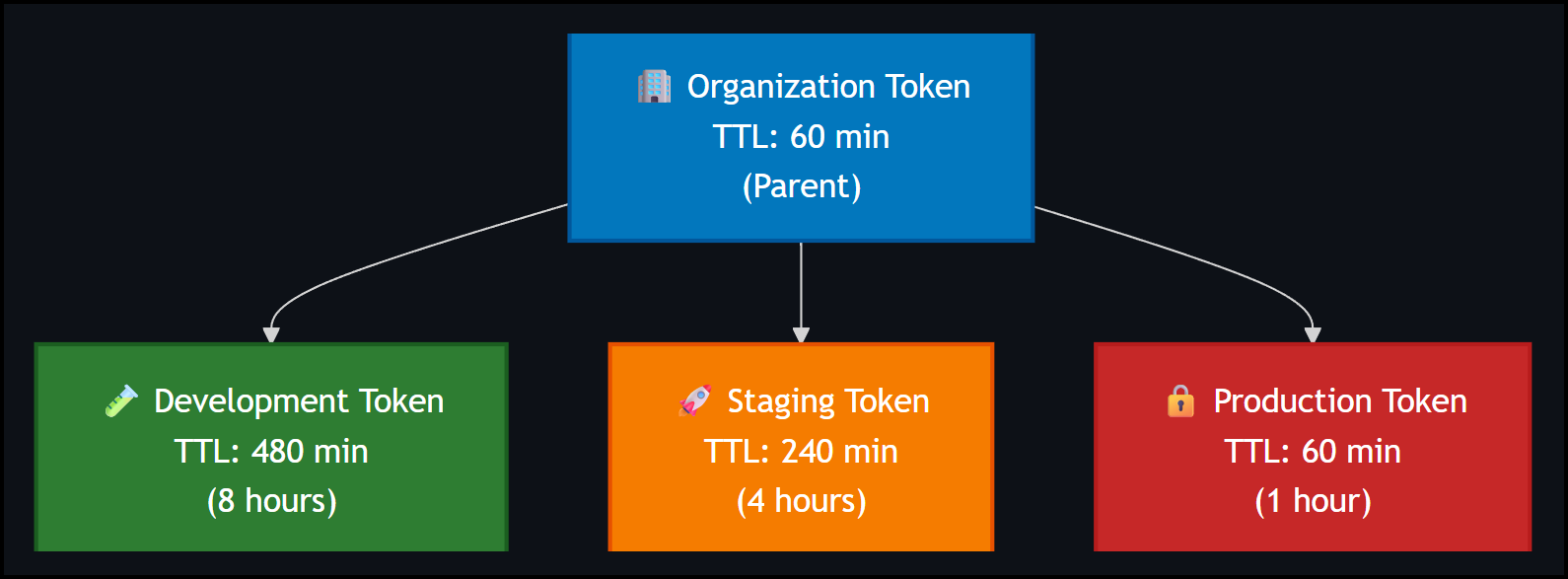
Many organizations find that structuring tokens by environment provides the clearest security boundaries and operational control:
# Organization-level parent token
ORG_TOKEN="u-org-level-token"
# Environment-specific child tokens with least privilege
DEV_TOKEN=$(akeyless uid-create-child-token --uid-token "$ORG_TOKEN" --child-ttl 480)
STAGING_TOKEN=$(akeyless uid-create-child-token --uid-token "$ORG_TOKEN" --child-ttl 240)
PROD_TOKEN=$(akeyless uid-create-child-token --uid-token "$ORG_TOKEN" --child-ttl 60)This pattern provides natural security boundaries where development environments receive longer-lived tokens for convenience, while production environments use shorter TTLs for maximum security. The hierarchy reflects the risk profile of each environment.
Service-Based Hierarchy
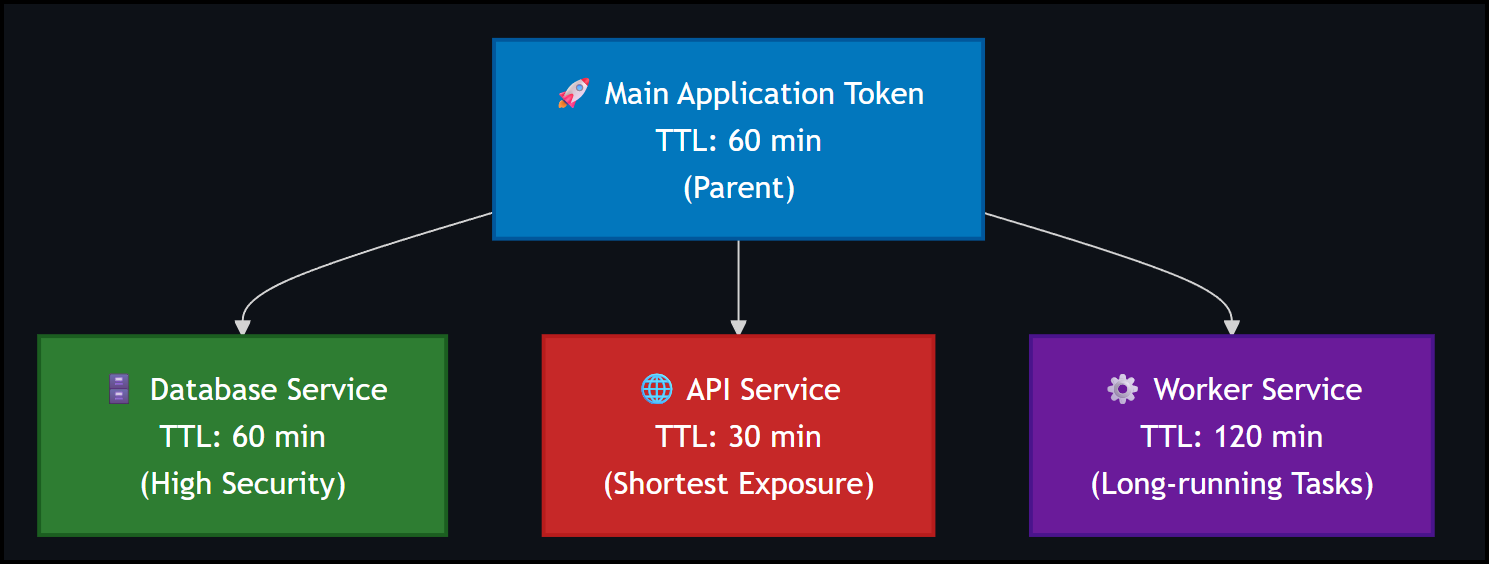
Alternatively, many microservice architectures benefit from service-based token hierarchies that reflect the application architecture:
# Main application token
APP_TOKEN="u-main-app-token"
# Service-specific child tokens implementing only the permissions needed
DB_TOKEN=$(akeyless uid-create-child-token --uid-token "$APP_TOKEN" --child-ttl 60)
API_TOKEN=$(akeyless uid-create-child-token --uid-token "$APP_TOKEN" --child-ttl 30)
WORKER_TOKEN=$(akeyless uid-create-child-token --uid-token "$APP_TOKEN" --child-ttl 120)This approach enables service isolation where each microservice receives only the access it needs, with TTLs reflecting the security requirements and operational patterns of each service type.
Access Controls and Revocation Scenarios
The hierarchical structure enables sophisticated revocation scenarios for secretless architecture and risk management. Understanding these capabilities is crucial for incident response and security management.
Universal Identity provides granular control over token revocation, allowing you to respond to security incidents with precision:
# Revoke only a specific service
akeyless uid-revoke-token --revoke-token "$DB_TOKEN" \
--revoke-type revokeSelf \
--auth-method-name "/production/microservices"
# Revoke service and all its child tokens
akeyless uid-revoke-token --revoke-token "$API_TOKEN" \
--revoke-type revokeAll \
--auth-method-name "/production/microservices"
# Emergency revocation of entire application tree
akeyless uid-revoke-token --revoke-token "$APP_TOKEN" \
--revoke-type revokeAll \
--auth-method-name "/production/microservices"These revocation capabilities enable targeted incident response: you can revoke individual service access when specific components are compromised, cascade revocation when broader issues are detected, or implement emergency shutdown procedures for entire application stacks when necessary.
Implementation Patterns
Microservices Architecture
Implementing Universal Identity in microservices environments enables sophisticated access control where each service can have its own child token for secretless authentication. This approach ensures only authorized services can access sensitive data while maintaining the operational simplicity that development teams need.
The following example demonstrates how to integrate Universal Identity into a Python microservice, showing the complete pattern from token management through secret retrieval:
# Example Python microservice integration
import os
import subprocess
import json
from datetime import datetime, timedelta
class AkeylessClient:
def __init__(self, auth_method, uid_token_file):
self.auth_method = auth_method
self.uid_token_file = uid_token_file
self._cached_t_token = None
self._token_expiry = None
def get_t_token(self):
# Check if cached token is still valid
if (self._cached_t_token and self._token_expiry and
datetime.now() < self._token_expiry - timedelta(minutes=5)):
return self._cached_t_token
# Read UID token from secure storage
with open(self.uid_token_file, 'r') as f:
content = f.read().strip()
# Handle demo-tokens format (key=value pairs)
if '=' in content:
for line in content.split('\n'):
if line.startswith('UID_TOKEN='):
uid_token = line.split('=', 1)[1]
break
else:
uid_token = content
# Exchange UID token for t-token (secretless pattern)
result = subprocess.run([
'akeyless', 'auth',
'--access-id', self.auth_method,
'--access-type', 'universal_identity',
'--uid_token', uid_token
], capture_output=True, text=True, check=True)
# Parse t-token from CLI output
lines = result.stdout.split('\n')
for line in lines:
if 'token' in line.lower() and 't-' in line:
import re
match = re.search(r't-[a-zA-Z0-9]+', line)
if match:
self._cached_t_token = match.group(0)
self._token_expiry = datetime.now() + timedelta(hours=1)
break
return self._cached_t_token
def get_secret(self, secret_name):
t_token = self.get_t_token()
result = subprocess.run([
'akeyless', 'get-secret-value',
'--name', secret_name,
'--token', t_token
], capture_output=True, text=True, check=True)
return result.stdout.strip()
# Usage in microservice (secretless authentication)
client = AkeylessClient("p-xxxx", "./tokens/demo-tokens")
db_password = client.get_secret("/demo/database-config")This implementation pattern demonstrates several key principles: the UID token is stored securely on disk rather than hardcoded, the t-token is cached to improve performance while respecting security boundaries, and the entire authentication flow is transparent to the application logic that needs secrets.
Automated Token Rotation
Production systems require robust automated token rotation to maintain secretless operations and proper lifecycle management without human intervention. The following script template provides a foundation for implementing automated rotation in production environments:
#!/bin/bash
# Production token rotation script
TOKEN_FILE="/secure/akeyless-token"
LOG_FILE="/var/log/akeyless-rotation.log"
# Read current token
CURRENT_TOKEN=$(cat "$TOKEN_FILE")
# Rotate token (secretless self-rotation)
NEW_TOKEN_OUTPUT=$(akeyless uid-rotate-token --uid-token "$CURRENT_TOKEN")
NEW_TOKEN=$(echo "$NEW_TOKEN_OUTPUT" | grep -E "(ROTATED TOKEN|Token):" | sed 's/.*\[//' | sed 's/\].*//')
if [[ -n "$NEW_TOKEN" && "$NEW_TOKEN" != "null" ]]; then
# Save new token securely
echo "$NEW_TOKEN" > "$TOKEN_FILE"
chmod 600 "$TOKEN_FILE"
echo "$(date): Secretless token rotation successful" >> "$LOG_FILE"
else
echo "$(date): Token rotation failed!" >> "$LOG_FILE"
exit 1
fiThis rotation script implements several production-ready features: secure token storage with proper file permissions, comprehensive logging for audit trails, error handling with appropriate exit codes, and validation of rotation success before updating stored credentials.
To ensure continuous operation, add the rotation script to your system’s crontab for hourly execution:
0 * * * * /path/to/rotate-token.shThe automated rotation ensures that even if a token is compromised, the exposure window is limited to a maximum of one hour, significantly reducing the potential impact of security incidents.
Universal Identity vs Traditional Approaches Summary
Below is a summary comparison between Universal Identity offered by Akeyless and traditional approaches.
| Feature | Universal Identity | Traditional Approaches |
|---|---|---|
| Rotation | ✅ Automatic with TTL reset | ❌ Manual process |
| Hierarchical Access | ✅ Parent-child relationships | ❌ Flat structure |
| Auditability | ✅ Complete token lifecycle logs | ❌ Limited visibility |
| Revocation | ✅ Immediate, granular control | ❌ System-wide impact |
| TTL Management | ✅ Built-in expiration | ❌ No expiration |
| Child Tokens | ✅ Service isolation | ❌ Shared credentials |
| Secretless Operations | ✅ No static secrets | ❌ Static credentials required |
Live Demo: Universal Identity in Action
The best way to understand how Universal Identity solves the secret zero problem is to see it in action. Our comprehensive interactive demo showcases how non-human identity management transforms from a security vulnerability into a competitive advantage through realistic persona separation.
You can watch the video at the top of this blog post.
Interactive Demo Experience
Run our interactive demo to experience the complete workflow from the GitHub repo mentioned above:
./start.shInteractive Demo Experience: Run ./start.sh and choose from 7 options:
- Admin Setup: Initial environment and token generation
- Platform Engineer Deployment: Deploy tokens to application services
- Application Service Operations: Autonomous operations with rotation
- Hierarchical Token Management: Parent-child token relationships
- Python Integration: Real-world secretless authentication
- Show Workflow Status: Monitor current workflow state
- Exit: Complete demo session
Demo Environment Setup
Our demo simulates a real-world non-human identity security environment where:
- Application services need to authenticate without pre-shared secrets
- Applications require database credentials and API access
- Token lifecycle management must be automated
- Hierarchical access controls reflect microservice architecture
Three-Persona Workflow Architecture
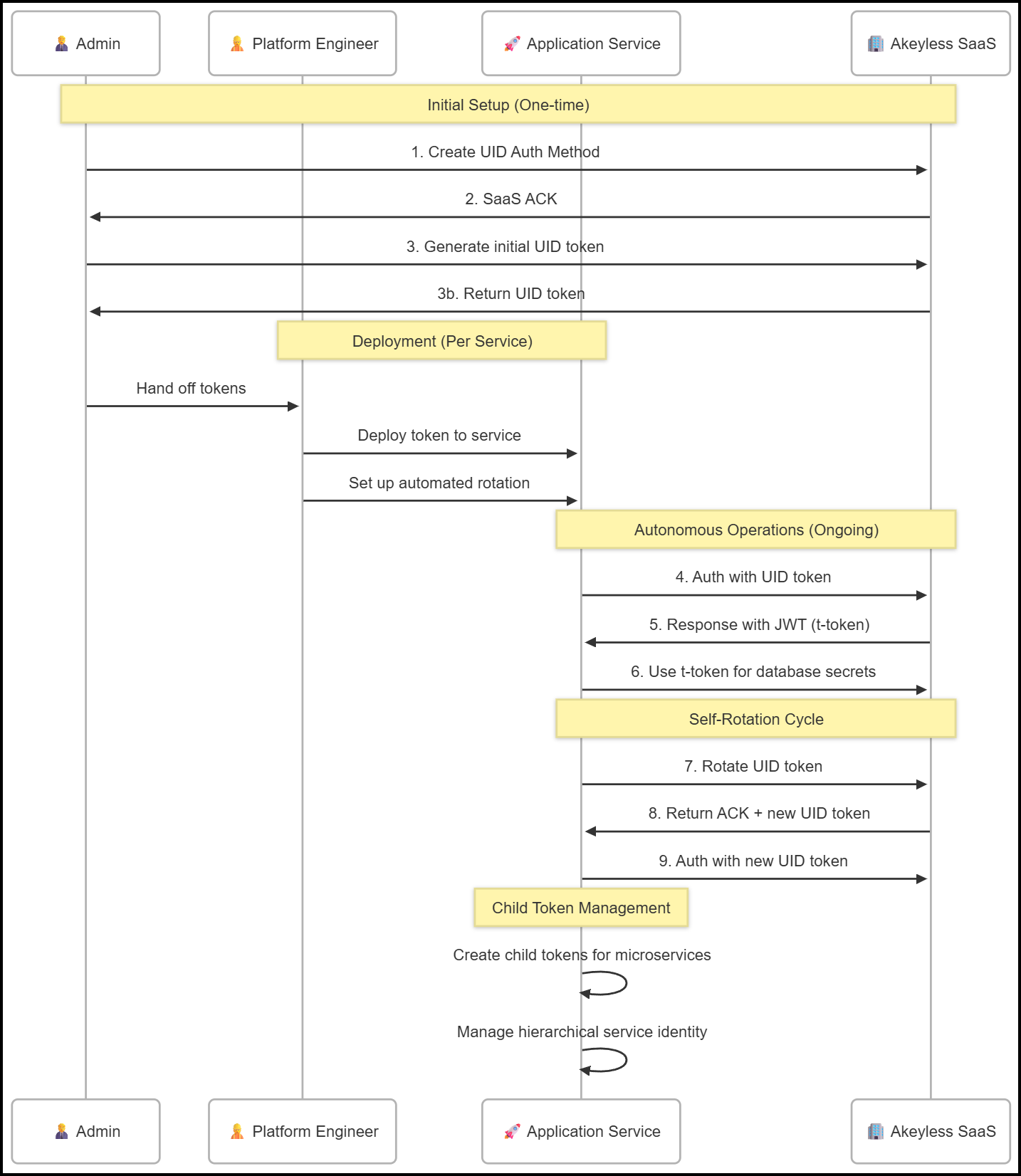
Our demo demonstrates the complete workflow through three distinct personas, each with specific responsibilities and access patterns in the Universal Identity ecosystem. There are multiple demo options that will walk you through the different steps.
Interactive Demo Summary
Getting Started: Simply run ./start.sh and choose your learning path:
Current 7 Menu Options:
- Admin Setup: Initial environment and token generation
- Platform Engineer Deployment: Deploy tokens to application services
- Application Service Operations: Autonomous operations with rotation
- Hierarchical Token Management: Parent-child token relationships
- Python Integration: Real-world secretless authentication
- Show Workflow Status: Monitor current workflow state
- Exit: Complete demo session
Scenario 1: Admin Setup (Option 1)
The Challenge: How does an admin establish the Universal Identity infrastructure for non-human authentication?
Interactive Demo Path: Choose Option 1: Admin Setup from ./start.sh menu
What You’ll Experience – Runs: ./scripts/admin-setup.sh
This option covers the first steps in our three-persona workflow diagram above.
- UID Authentication Method Creation:
akeyless auth-method create universal-identity --name "/demo/uid-non-human-auth" --ttl 60 --jwt-ttl 720- Creates dynamic non-human identity infrastructure
- No shared secrets required for this process, only the admin’s log in credentials into Akeyless
- Solves the secret zero problem at the organizational level
- Initial Token Generation:
akeyless uid-generate-token --auth-method-name "/demo/uid-non-human-auth"- Generates initial token for application service
- One-time provisioning activity
- Admin maintains policy control
- Token Provisioning:
- Creates ./tokens/client-tokens file for Platform Engineer
- Secure handoff of initial credentials
Demo Outcome: Admin infrastructure ready for Platform Engineer deployment.
Scenario 2: Platform Engineer Deployment (Option 2)
The Challenge: How does a Platform Engineer deploy admin-generated tokens to application services?
Interactive Demo Path: Choose Option 2: Platform Engineer Deployment from ./start.sh menu
What You’ll Experience – Runs: ./scripts/platform-deploy.sh
This option covers the platform engineering steps in our three-persona workflow diagram above.
- Service Deployment:
- Deploys admin-generated tokens to application services
- Creates ./tokens/application-service-token for autonomous operations
- Sets up automated rotation infrastructure with application-service-rotate.sh
- Configures cron job template for hourly rotation
Demo Outcome: Application service is provisioned and ready for autonomous operations.
Scenario 3: Application Service Operations (Option 3)
The Challenge: How does an application service operate autonomously with self-rotating credentials?
Interactive Demo Path: Choose Option 3: Application Service Operations from ./start.sh menu
What You’ll Experience – Runs: ./scenarios/client-workflow.sh (includes automatic token rotation)
This option covers steps 4-9 in our three-persona workflow diagram above.
- UID → T-Token Exchange:
akeyless auth --access-id "$ACCESS_ID" --access-type universal_identity --uid_token "$UID_TOKEN"- Exchanges long-lived identity (UID) for short-lived session (T-token)
- Best practice: separation of identity vs. operations
- No static credentials stored anywhere
- Database Secret Retrieval:
akeyless get-secret-value --name "/demo/database-config" --token "$T_TOKEN"- Uses T-token for actual database secret access
- Retrieves real database configuration JSON
- Demonstrates end-to-end secretless application authentication
- Self-Rotation Process:
akeyless uid-rotate-token --uid-token "$UID_TOKEN"- Zero human intervention required
- Old token immediately invalidated
- New token issued with reset TTL
- Automatic update of stored credentials in token file
- Validation of New Token:
- Authenticate with new token successfully
- Demonstrate old token is rejected
- Show seamless operation continuity
Demo Outcome: Complete application service autonomous workflow with built-in token rotation.
Scenario 4: Hierarchical Token Management (Option 4)
The Challenge: How do you organize non-human identity access across microservices with proper security controls?
Interactive Demo Path: Choose Option 4: Hierarchical Token Management from ./start.sh menu
What You’ll Experience – Runs: ./scenarios/child-tokens.sh
- Parent-Child Token Creation for Microservices:
# Create microservice-specific child tokensakeyless uid-create-child-token --uid-token "$PARENT_TOKEN" --child-ttl 30 # Database serviceakeyless uid-create-child-token --uid-token "$PARENT_TOKEN" --child-ttl 60 # API gateway- Different TTLs for different microservice risk levels
- Service isolation through token hierarchy
- Microservice architecture reflected in access
- Token Tree Visualization:
akeyless uid-list-children --uid-token "$PARENT_TOKEN"- See complete microservice token family tree
- Understand inheritance and relationships
- View individual TTLs and expiration times
- Granular Revocation for Microservices:
# Revoke individual microserviceakeyless uid-revoke-token --revoke-token "$DATABASE_SERVICE_TOKEN" --revoke-type revokeSelf --auth-method-name "$AUTH_METHOD"- Targeted revocation vs. cascading revocation
- Emergency response capabilities for microservices
- Precise access controls
Demo Outcome: Hierarchical microservice organization with granular control capabilities.
Scenario 5: Python Integration Example (Option 5)
The Challenge: How does Universal Identity integrate into real-world applications and programming languages?
Interactive Demo Path: Choose Option 5: Python Integration Example from ./start.sh menu
What You’ll Experience – Runs: python3 ./examples/machine-auth.py
- Secretless Python Application Service:
# Load UID token from secure storage (no hardcoded credentials)client = AkeylessClient( auth_method=access_id, token_file="./tokens/application-service-token" )# Automatic UID → T-token exchangesecret = client.get_secret("/demo/database-config") - Database Service Integration:
# Retrieve database credentials using secretless authenticationdb_config = client.get_secret("/demo/database-config")config = json.loads(db_config)# Use credentials for actual database connectiondb_service = DatabaseService(client)db_service.connect_to_database() - Automatic Token Management:
# Token rotation handled transparentlyif client.rotate_uid_token():
print("✅ UID token rotated successfully (secretless self-rotation)")# Child token creation for microservice isolationchild_token = client.create_child_token(ttl_minutes=30)
Demo Outcome: Real-world integration patterns that developers can immediately implement in their applications.
Status Monitoring (Option 6)
Interactive Demo Path: Choose Option 6: Show Workflow Status from ./start.sh menu
What You’ll Experience:
- Real-time status of workflow completion
- Prerequisites validation
- Dependency checking
- Current token file status
Demo Outcome: Clear visibility into workflow progress and component readiness.
Conclusion
While cloud-native platforms like AWS, GCP, Azure, and Kubernetes have solved non-human identity with built-in solutions (IAM roles, managed identities, service accounts), 70% of enterprise workloads still run in environments that lack these capabilities: VMware VMs, physical servers, on-premises systems, and legacy infrastructure.
Universal Identity provides the elegant solution for this critical gap, bringing secretless architecture to any environment through automatic token rotation that solves the fundamental secret zero problem.
Since the secret zero problem cannot be eliminated entirely (you fundamentally need that first credential), Universal Identity takes a different approach: it minimizes secret zero to a single, self-managing credential that automatically rotates every 60 minutes. This transforms the secret zero challenge from “how do we securely distribute static credentials” to “how do we provide one initial token that manages itself forever.”
The result: applications in non-cloud environments gain the same secretless capabilities as cloud-native applications, without requiring platform-specific identity services.
Ready to Transform Your Non-Human Identity Management?
Experience firsthand how Akeyless Universal Identity simplifies non-human identity management, even in challenging, non-cloud-native environments. Check out a demo or contact their sales team to discuss your needs in detail.
Transform your secret zero challenges into a robust, secure, and fully automated identity solution today with Akeyless!
Frequently Asked Questions
What is a non-human identity?
A non-human identity is a digital identity assigned to machines, applications, services, or automated systems that need to authenticate and access resources without direct human intervention. Unlike human identities, these identities are used by automated processes such as CI/CD pipelines, microservices, containers, virtual machines, and robotic process automation systems to perform tasks and access sensitive data.
What is the difference between human identity and non-human identity?
Human identities are tied to actual people and typically use interactive authentication methods like passwords, multi-factor authentication, and single sign-on. Non-human identities belong to digital systems and automated processes that operate without direct human oversight. Key differences include:
- Human identities: Interactive authentication, MFA, password resets, user sessions
- Non-human identities: Programmatic authentication, API keys, certificates, service accounts, continuous operation
What are non-human entities?
Non-human entities include any digital systems or automated processes that require authentication, such as:
- Microservices and containerized applications
- CI/CD pipelines and build systems
- Cloud services and serverless functions
- Virtual machines and physical servers
- IoT devices and edge computing systems
- Robotic process automation (RPA) bots
- Service accounts and system processes
What is secretless authentication?
Secretless authentication is a security approach that eliminates static, long-lived credentials in favor of dynamic, automatically-rotating tokens. Instead of hardcoding API keys or passwords, secretless systems use short-lived tokens that are automatically generated, rotated, and revoked.
Universal Identity implements secretless authentication through UID tokens that rotate every 60 minutes, eliminating security vulnerabilities associated with static credentials.
What is non-human identity security?
Non-human identity security refers to the specialized security policies, access controls, and management practices needed to protect machine identities and automated processes. This includes implementing least privilege access, proper lifecycle management, automated rotation, hierarchical access management, and monitoring to prevent unauthorized access and data breaches.
Unlike traditional security focused on human users, non-human identity security addresses unique security challenges of 24/7 automated systems.
What is machine identity management?
Machine identity management is the practice of managing digital identities for machines, devices, and automated processes. This involves creating, provisioning, rotating, and revoking credentials for non-human entities.
Universal Identity provides advanced machine identity management through hierarchical token structures, automatic rotation, and role based access control that ensures only authorized individuals and systems can gain access to critical resources.
What is the difference between non-human identity and machine identity?
The terms non-human identity and machine identity are often used interchangeably, but there are subtle distinctions:
- Machine identity: Typically refers to physical devices, servers, and infrastructure components
- Non-human identity: Broader term encompassing machines, applications, service accounts, automated processes, and any digital entity that operates without human interaction
Both require similar security controls and access management approaches, including dynamic authentication, proper lifecycle management, and robust security measures to prevent cyber threats.




