Secrets management is a critical process in the realm of IT security, focusing on securing and controlling credentials, such as passwords, API keys, tokens, and certificates, used by applications, services, and users. It ensures that sensitive information is stored, accessed, and centrally managed securely to prevent unauthorized access and potential security breaches.
Understanding Secrets Management
Secrets management involves securely storing and managing secrets such as certificates, SSH keys, API keys, credentials, tokens, passwords, and sensitive data. These secrets are crucial for authenticating users and machines, enabling access to applications and services, and managing workload identities. Workload identities, which represent non-human identities in automated environments, are essential for controlling access within cloud platforms and services.
Implementing secrets management is essential to address security management challenges in elastic and auto-scale environments. Effective secrets management eliminates the need for manual policy application and ensures secure authentication in real-time.
The protection of confidential data, including secrets and workload identities, is vital for digital authentication. It supports privileged users who need access to critical internal data and sensitive applications, ensuring the integrity and security of business operations.
The process to manage secrets is critical; it ensures the secure storage, access, and lifecycle management of sensitive information like passwords and tokens. Utilizing proven tools and methods, secrets management helps safeguard these digital assets, which are indispensable for activities such as user authentication and license management.

What are Secrets Management Best Practices for Enhanced Security?
Users need to use authentication methods to access sensitive information or company resources. Whenever these secrets or credentials are transmitted across the company, there is a risk of data leakage or lost passwords. Secret creation is a critical aspect of securely generating and managing these credentials. Because of this risk, there is a critical need for organizations to protect secrets. Privileged users must be carefully managed to ensure that only authorized personnel have access to sensitive information. Implementing a robust secrets management strategy is essential to securely manage and protect sensitive data. Managing secrets effectively is crucial to prevent unauthorized access to sensitive data.
Centralize Secrets Management
Consolidate all sensitive information within a centralized system. This strategy not only simplifies management but also minimizes the risk of data breaches, allowing your IT team to maintain better control and oversight.
Embrace Automated Tools
Transitioning from manual to automated secrets management significantly reduces the risk of human error. Begin with robust password management software to secure sensitive credentials efficiently. Use automation tools to find and centrally manage all types of credentials, such as passwords, API keys, and tokens, in a secrets vault. Additionally, eliminate hardcoded/embedded secrets from DevOps tool configurations, build scripts, code files, and applications using automation.
Implement Holistic Security Measures
For larger organizations, a comprehensive approach is vital. Opt for secrets management solutions that support a variety of credentials beyond typical user accounts, such as API keys and system tokens, to broaden your security framework.
Strengthen Password Policies
Employee passwords often represent the weakest link in security chains. Encourage the use of complex passwords and enforce regular updates, especially for accounts with access to critical data. Prohibit common and predictable passwords to fortify your defense.
Monitor Privileged Access
Integrate your secrets management tools with Privileged Access Management (PAM) systems. This allows for monitoring and managing high-risk user activities, enhancing security by restricting access to authorized personnel only.
Leverage Threat Analytics
Utilize the centralized nature of your secrets management solution to perform comprehensive risk assessments. Quick detection and mitigation of potential threats keep your systems secure and compliant.
By adhering to these secrets management best practices, businesses can safeguard their sensitive data against unauthorized access and potential cyber threats effectively. As organizations expand their operations into multi-cloud environments, managing secrets across platforms like AWS, Azure, and GCP introduces additional complexities that require specialized strategies.
What are Secrets Management Best Practices for Multicloud Environments?
When operating across multiple cloud platforms such as AWS, Azure, GCP, and other cloud providers, it’s crucial to implement robust secrets management best practices tailored for a multi-cloud strategy. Implementing a multi-cloud strategy involves coordinating security measures across different cloud environments to ensure consistency and control:
Centralized Secrets Management
Use a centralized secrets management solution that integrates seamlessly with AWS, Azure, GCP, and other cloud providers. This ensures consistent policy enforcement and simplifies governance across diverse environments. When each application, cloud provider, or organizational unit has its own security model, the organization loses visibility and control.
Uniform Security Policies
Standardize security policies, role definitions, access controls, and auditing procedures across all platforms to ensure uniform application of security practices.
Encryption and Tokenization
Secure sensitive data by encrypting it both at rest and in transit, and apply tokenization to replace sensitive information with non-sensitive equivalents.
Automate Secrets Rotation
Implement automation for rotating secrets and credentials to reduce the risk associated with stale or compromised keys, particularly important in dynamic cloud environments.
Implement Least Privilege Access
Enforce the principle of least privilege by ensuring that entities, including workload identities, have only the necessary permissions for their specific roles.
Comprehensive Audit Trails
Maintain detailed logs of all secrets access and usage across cloud platforms to aid in forensic analysis and compliance reporting.
Strict Access Controls
Enforce strict access controls to ensure that sensitive data such as passwords, keys, and tokens are stored securely and separated from code, with privilege-based sessions for all access attempts.
Use Multi-Factor Authentication (MFA)
Strengthen access controls with MFA to add an extra layer of security, making it more challenging for unauthorized users to gain access.
Regular Security Assessments
Continually assess the security posture of your multi-cloud environment to identify and remediate vulnerabilities, ensuring compliance with the latest security standards and regulations.
By incorporating these practices, organizations can effectively manage their secrets across multiple cloud platforms, enhancing their overall security posture and ensuring that their critical data remains protected against evolving cyber threats.
Secrets Management Best Practices: Essential Guide to Secrets Management
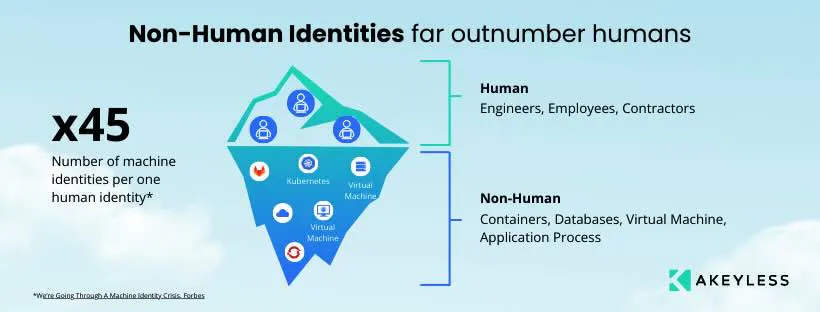
What Are the Types of Secrets?
The six most common secrets, including API keys
- Passwords – Credentials used by users or applications to securely access systems or information.
- API Keys – A unique identifier used to provide a secret token for authentication.
- SSH Keys – Access credentials that are used within the secure shell (SSH) protocol.
- Private Certificates – Self-hosted certificates used within an organization.
- Tokens – A value, such as a randomly generated number, assigned to sensitive data in order to hide its actual content.
- Encryption Keys – Strings of bits that are used by cryptographic algorithms to encrypt or decrypt data.
Securing secrets is essential to the overall security of any business. Consequently, IT groups often utilize secrets management tools in their DevOps environments to enhance this security.
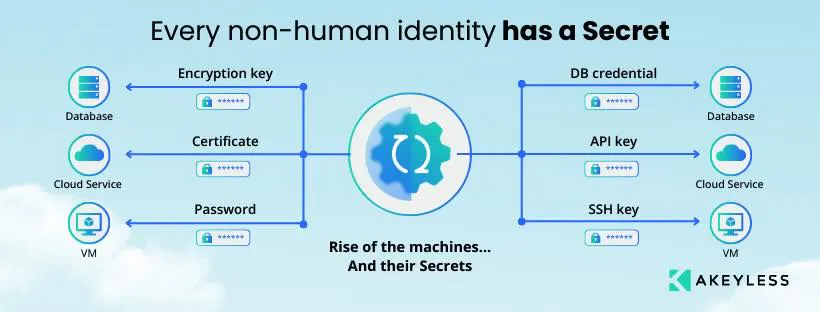
What Are the Challenges of Secrets Management?
DevSecOps and IT are complicated fields. The many types of secrets you have to manage make transmitting and storing them difficult, leading to potential security gaps. Keeping up a secure secrets store comes with many challenges.
Secret sprawl
With the proliferation of multi-cloud and microservices, organizations manage hundreds or even thousands of secrets for developer access. Sharing these secrets, leaving them in code, or simply keeping them unrevealed can expose your organization to a breach. Consequently, maintaining strict control and secure management practices is crucial to safeguard your data.
Fragmented control
In many companies, individual departments and teams handle their own secrets separately from others. The result is a decentralized platform for secrets management, which can lead to security gaps and challenges when it comes to auditing.
Remote access
With the increasing trend of remote work, employees need remote access authorization. How do you ensure secure secret transfer?
Manual Sharing and Failure to Rotate Sensitive Data
Automating the rotation of secrets and employing secret management tools can mitigate the risks associated with manual sharing and static passwords.
Hardcoded Secrets
Removing hardcoded credentials from scripts and configurations and replacing them with dynamic secret retrieval methods enhances security.
Lack of Awareness and Visibility
Implementing centralized secret management solutions provides the necessary visibility and control over secrets across the organization.
Cloud Computing Privileges
A comprehensive approach to secret management is necessary for managing cloud computing privileges, ensuring secure management of secrets for each virtual machine instance.
CI/CD Pipeline Integration
In DevOps environments, the integration of secret management practices into the CI/CD pipeline is crucial for securing automated processes and ensuring compliance.
What Are Secrets Management Tools?
Maintaining your own server architecture for secrets management can be costly and complex. Using dedicated systems with advanced security features to store secrets, such as AWS Secrets Manager, Google Secrets Manager, or Azure KeyVault, can significantly enhance security and efficiency. Instead, adopting a SaaS-based solution like Akeyless Secrets Management Vault can provide a more efficient and cost-effective alternative. These SaaS tools offer robust security and seamless integration, thereby facilitating easier and safer access to your digital secrets.
Specifically, Akeyless operates on a vaultless technology that distributes secrets across multiple secure locations rather than storing them in a single vault. This approach enhances security by reducing the risk of a single point of failure and making it more difficult for unauthorized users to access sensitive information in DevOps environments.

Secrets Management Tool Evaluation
This checklist serves as a starting point for evaluating secrets management tools. Additionally, each organization’s specific needs may require further considerations. Moreover, it’s beneficial to conduct a trial or pilot project with the shortlisted tools. This approach helps determine how well they integrate into your existing workflows and meet your security requirements.
1.Security Standards
- Uses strong encryption for storing secrets.
- Offers secure secret generation and automated secrets rotation capabilities.
- Provides detailed access controls and policies.
2. Integration with Existing Infrastructure
- Supports integration with your AWS, Azure and GCP
- Seamlessly integrates with your CI/CD pipelines and DevOps tools.
- Offers SDKs or APIs for custom integration needs.
3. Multi-Cloud and Hybrid Support
- Facilitates management of secrets across multiple cloud environments.
- Supports hybrid setups combining on-premises and cloud resources.
- Enables consistent secret management practices across all environments.
4. Ease of Use and Management
- Provides a user-friendly interface for managing secrets.
- Offers automated secret rotation and management.
- Includes comprehensive documentation and community support.
5. Compliance and Auditing
- Meets relevant compliance requirements for your industry (e.g., GDPR, HIPAA, SOC 2).
- Offers detailed audit logs for all secret access and changes.
- Allows for easy reporting and monitoring of secret usage.
6. Scalability and Performance
- Scales with your organization’s growth and secret management needs.
- Maintains high performance even as the number of secrets and access requests grow.
- Offers high availability and redundancy features.
7. Cost and Licensing
- Provides clear and predictable pricing models.
- Offers a cost-effective solution without compromising on features.
- Includes all required features in the base price without hidden costs.
8. Vendor Reputation and Support
- Has a strong reputation for reliability and customer satisfaction.
- Offers responsive and knowledgeable technical support.
- Provides ongoing updates and security patches.
Download our eBook for more information: Choosing the Best Secrets Management Tool for Your Enterprise eBook.

Akeyless isn’t just another name in the game; it’s pioneering a vaultless approach to keeping your digital secrets safe. Consequently, instead of storing all your sensitive info in one spot, Akeyless spreads it out. This method makes it tougher for unwanted guests to access your data. Essentially, it’s like having multiple safe boxes scattered around, each holding a piece of the puzzle. Therefore, for businesses navigating the cloud, Akeyless offers a seamless way to manage access keys, passwords, and certificates without worrying about security breaches.
A Closer Look at Akeyless Secrets Management
Tutorials to Manage Your Secrets
Jump into these easy to follow tutorials:
- Creating and Updating a Static Secret
- Sharing a Static Secret
- Akeyless Password Manager
- Creating and Configuring Targets
- Creating and Configuring Linked Targets
- Creating and Using Dynamic Secrets
- Creating and Using Rotated Secrets
- Universal Secrets Connector – Managing Secrets in AWS, GCP, K8s, and more












