Posted by Dean Sher
February 18, 2025
The strength of passwords used within an organization can no longer be an afterthought. The security posture of an organization, especially regarding password management, is a critical factor that directly impacts overall cybersecurity. Knowing your organization’s password security posture—often quantified as a password score—can help identify vulnerabilities, mitigate risks, and enhance your overall security framework. In this blog post, we will explain the importance of understanding your organization’s password security posture, the factors that contribute to password strength, and how to improve it.
The Significance of Password Security
Passwords are the frontline defense in protecting sensitive information and access to organizational resources. Weak or compromised passwords can lead to unauthorized access, data breaches, and significant financial and reputational damage. Thus, understanding the strength of passwords across the organization is paramount.
What is a Password Security Posture?
A password security posture is a comprehensive assessment of how effectively an organization manages its passwords. This includes evaluating password strength, update frequency, and potential exposure in data breaches. By employing a Password Strength Scoring System, organizations can score passwords based on various criteria, such as length, character variety, and update frequency.
Password Strength Scoring System
The Password Strength Scoring System evaluates user-generated passwords through a formula that assigns a score based on specific criteria:
- Minimum Length: Encouraging longer passwords, points are awarded for each character above the minimum set by the organization’s policy. This helps foster a culture of using strong, lengthy passwords.
- Character Diversity: Organizations score passwords based on the inclusion of different character types (uppercase, lowercase, numbers, special characters), rewarding diversity that enhances security.
- Periodic Rotation: Points are assigned based on how recently passwords have been updated, with more recent updates receiving higher scores. Regularly changing passwords reduces the likelihood of long-term exploitation if a password is compromised.
The Benefits of Knowing Your Password Score
- Identifying Weaknesses: By evaluating the password score, organizations can pinpoint weak passwords that do not meet minimum strength requirements. This helps to focus remediation efforts where they are most needed.
- Risk Mitigation: Understanding the average password score across the organization can help in assessing potential risks. Weak passwords or those that have not been updated regularly may indicate vulnerability to attacks.
- Compliance and Governance: Many regulatory frameworks require organizations to adhere to certain security standards, including password management. Regular assessments, such as those conducted via Pentest as a Service, can help ensure compliance with these regulations.
- User Education: Sharing insights from password scoring can help educate users about creating stronger passwords. Recommendations based on scoring can guide them in developing better habits, such as using longer passwords or incorporating diverse character types.
- Proactive Security Measures: Regularly monitoring the password security posture allows organizations to be proactive rather than reactive. They can implement stronger policies, provide user training, and establish a routine for password updates.
Improving Your Password Security Posture
To bolster your organization’s password security posture, consider the following strategies:
- Implement a Strong Password Policy: Define clear guidelines for password creation, including minimum length and required character types.
- Utilize a Password Management Tool: Consider deploying tools that help users generate and store strong passwords, minimizing the chances of weak passwords being created.
- Conduct Regular Assessments: Implement a system for regularly evaluating password strength and update frequency, allowing for continuous monitoring and improvement.
- Encourage Multi-Factor Authentication (MFA): MFA adds an additional layer of security beyond passwords, making it harder for unauthorized users to gain access.
- Provide User Training: Educate employees about the importance of password security and how to create and maintain strong passwords.
Solving Password Security Challenges with Akeyless
Akeyless takes a comprehensive approach to addressing password security by combining automated scoring systems, real-time data checks, and robust integrations to ensure an enhanced security posture.
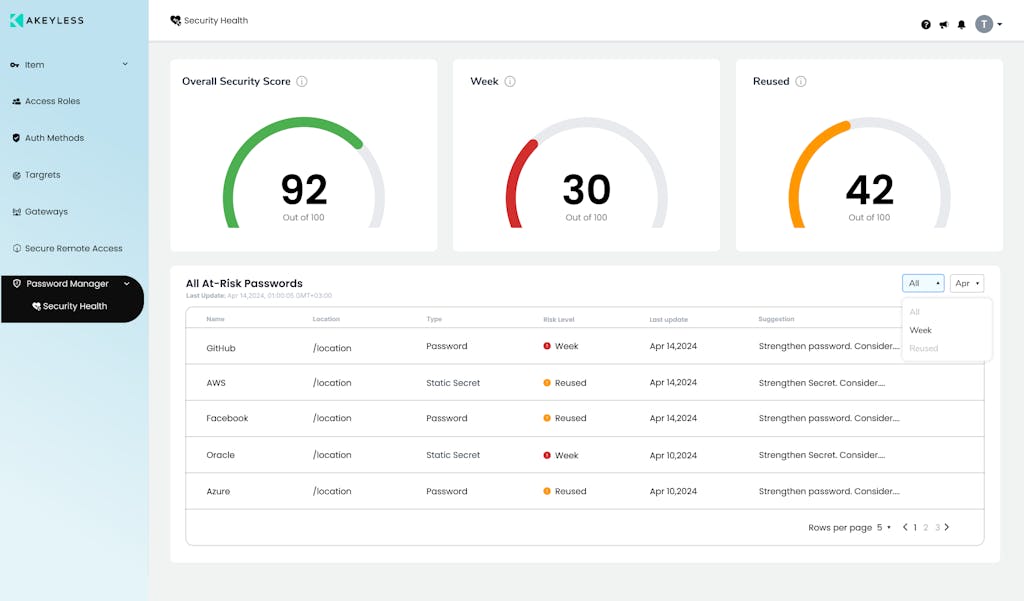
Password Security Health Assessment
Password Security Health integrates with the Have I Been Pwned (HIBP) API. This ensures real-time detection of compromised credentials and allows organizations to assess the frequency of passwords found in breaches.
Data Storage and Reporting
Akeyless allows password health evaluation results with a schema designed to track:
- BreachStatus: Indicates if a password or secret is found in breaches.
- BreachCount: The number of times a password appears in breach databases.
This data provides valuable insights into organizational trends and enables the generation of user and admin reports for actionable security improvements.
Password Strength Scoring System
Akeyless Password Strength Scoring System evaluates passwords using a dynamic scoring model:
- Length and Character Variety: Points are awarded for exceeding minimum length and incorporating diverse character types (uppercase, lowercase, numbers, symbols).
- Periodic Updates: Scoring considers the frequency of password updates to ensure compliance with best practices.
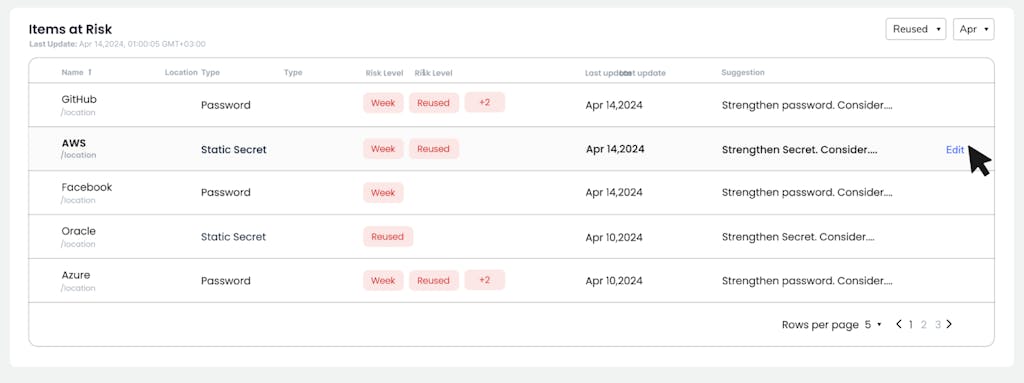
Actionable Feedback
As part of password scoring, Akeyless provides actionable suggestions to users for improving password strength.
Conclusion
Understanding and managing your organization’s password security posture is vital in today’s digital landscape. By implementing a robust Password Strength Scoring System and actively working to improve password security practices, organizations can significantly reduce their risk of cyberattacks. A strong password policy not only protects sensitive data but also fosters a culture of security awareness among employees. Regular evaluations and improvements to your password management strategy can lead to a more secure and resilient organization. Remember, a secure password is the first step towards safeguarding your digital assets.
Protect your passwords with enterprise-level security. Learn more here.




