Posted by Dean Sher
December 4, 2025
In today’s fast-paced world of workflow automation, security can no longer be an afterthought, especially when building intelligent, AI-driven processes. That’s why we’re thrilled to announce that the Akeyless n8n Community Node is now complete, published to npm, and readily available through the n8n Community Nodes marketplace!
This integration brings the full power of Akeyless Identity Security Platform directly into your n8n workflows, enabling you to manage secrets securely, rotate credentials automatically, and, most excitingly, unlock secretless access for your AI Agents.
Why This Integration Changes Everything for n8n Users
n8n is the go-to open-source automation tool for thousands of teams building everything from simple data pipelines to sophisticated AI-powered workflows. But as these workflows grow more complex and incorporate AI Agents (like the built-in LangChain-powered AI Agent node), one critical challenge emerges: how do you securely handle API keys, database credentials, and LLM tokens without exposing them?
Hardcoding secrets? Risky.
Environment variables? Still leak-prone.
Manual rotation? A DevOps nightmare.
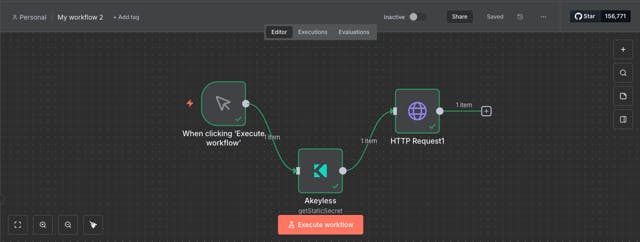
The new Akeyless n8n node solves this head-on by letting you:
- Retrieve static, dynamic, and rotated secrets on demand
- Create, update, and delete secrets directly from workflows
- Authenticate secretless using secure authentication methods
- Dynamically inject secrets into downstream nodes, without ever exposing them in plain text.
But the real game-changer? Secretless AI Agents.
Build Truly Secretless AI Agents in n8n with Akeyless
Akeyless pioneered SecretlessAI™, a breakthrough approach that eliminates embedded credentials entirely. Instead of storing API keys (for OpenAI, Gemini, Claude, or any other service), your AI Agents authenticate using trusted machine identities, such as cloud IAM roles, Kubernetes service accounts, or JWTs, and receive just-in-time, ephemeral secrets only when needed.
With the new Akeyless node in n8n:
- Your AI Agent workflows can fetch LLM credentials or database passwords at runtime via identity-based authentication
- No more static keys sitting in node configurations
- Full auditability, automatic rotation, and zero-knowledge encryption backed by Akeyless’ patented Distributed Fragments Cryptography™
- Ideally suited for autonomous agents that make decisions, call external APIs, and operate across hybrid environments
This means you can confidently scale AI-driven automation, whether it’s customer support bots, data enrichment pipelines, or multi-step reasoning agents, knowing your credentials are never at rest, never hardcoded, and never exposed.
Get Started in Minutes
The Akeyless node is now live and easier than ever to add:
- Akeyless Documentation: https://docs.akeyless.io/docs/n8n-nodes-akeyless#/
- npm Package: n8n-nodes-akeyless
- GitHub Repository: akeyless-community/N8N_PlugIn
- Install directly via n8n’s Community Nodes marketplace (cloud or self-hosted)
Whether you’re securing traditional workflows or pioneering the next generation of secretless AI Agents, Akeyless + n8n delivers enterprise-grade secrets management without the complexity.
Ready to eliminate secrets sprawl and supercharge your secure automations?
👉 Try the Akeyless n8n node today and experience secretless AI in action.
Start building secure workflows now | Schedule a demo




