Akeyless Workload Identity Federation:
SSO for Machines
Authenticate & Authorize Machine Identities Across Clouds Without Secrets
The Challenge: Identity Silos and Secret Sprawl
As cloud-native architectures grow in complexity, organizations face a persistent challenge: managing machine identities across hybrid and multi-cloud environments without creating a fragmented security posture. Traditional approaches rely on static secrets, environment-specific integrations, and duplicated configurations, leading to credential sprawl, inconsistent policy enforcement, and increased risk of breach.

The Solution: Federated Identity, Secretless Authentication
Akeyless Workload Identity Federation offers a unified and secure approach to managing machine identities: across cloud, on-premises, and containerized environments. By leveraging identity federation protocols and native integrations with cloud IAMs (like AWS IAM, Azure Entra ID, and GCP Workload Identity Federation), Akeyless authenticates workloads based on their native cloud identities, without ever storing or transmitting static secrets.
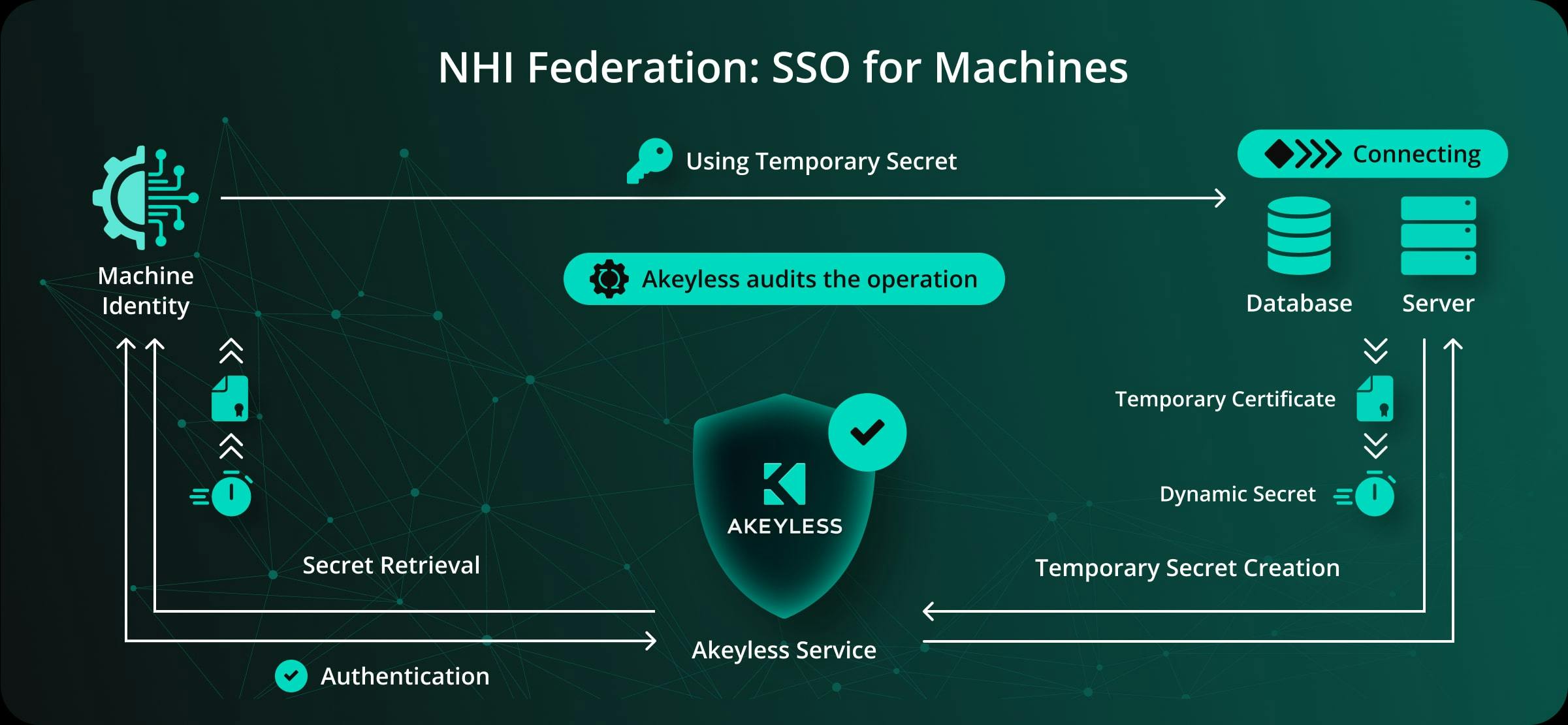
Core Capabilities
Unified NHI Management Across Clouds
Manage and authenticate workloads from AWS, Azure, GCP, and on-prem through a centralized platform.
Secretless Authentication
Secretless architecture eliminates stored credentials, replacing them with ephemeral tokens.
Zero Trust,
Just-in-Time Access
Ensure every machine-to-machine interaction is authenticated and authorized with dynamic, time-limited access.
SPIFFE & SPIRE Integration
Akeyless supports open standards for workload identity (SPIFFE/SPIRE), streamlining identity issuance and trust management.
Cross-Cloud Interoperability
Centralized policy enforcement across all environments guarantees uniform security practices, no matter where workloads run.
Benefits

Dramatically Reduce Risk
By eliminating static secrets, Akeyless minimizes the attack surface, eliminating one of the most common breach vectors.

Streamlined Compliance
Enforce security policies consistently and retain full audit trails across environments to meet regulatory requirements with ease.

Operational Efficiency at Scale
Save engineering time with native support for cloud IAM, Kubernetes, and on-prem environments. Simplify onboarding and scaling workloads.

Built for Hybrid and Multi-Cloud Environments
Akeyless doesn’t require a single cloud vendor. Whether you run in AWS, Azure, GCP—or across them all—Akeyless brings consistent identity and access control.

Why Akeyless

Truly Secretless by Design
Unlike legacy solutions, Akeyless ensures that everything is ephemeral, just-in-time, and zero-knowledge.

Single Unified Platform
No more piecemeal integrations. Akeyless brings together identity federation, secrets management, and access control under one platform.

Cloud-Native and Standards-Aligned
Natively integrated with cloud IAM and SPIFFE/SPIRE frameworks to make identity work with your infrastructure—not around it.
Ready to Eliminate Machine Credentials for Good?
See Akeyless Workload Identity Federation in action and explore how you can go truly secretless.