Posted by Suresh Sathyamurthy
July 15, 2023
I think I am preaching to the choir when I say that cybersecurity threats are on the rise, and protecting sensitive data and credentials is probably among the top few priorities for enterprises. Our purpose of existence here at Akeyless is to provide you with a platform to help you easily manage your secrets — like passwords, certificates, keys and tokens — while enhancing your security posture and reducing costs.

Why Akeyless over other Vaults?
Our answer is that not all Secrets Management products are created equal. Let’s take the HashiCorp Vault for example. As it stands today, this is the largest legacy product that came into being over a decade ago. Over the course of the last decade, enterprises have become multi-cloud, adopted more cloud-native technologies and the legacy approach to Secrets Management became complex and expensive. HashiCorp Vault is an on-premise product, can be deployed in clouds but is not cloud native and is not SaaS. It can take months to install and deploy and often takes a full time engineer to maintain 24×7.
Even HashiCorp recognizes that SaaS is the wave of the future, and has added HCP Vault Secrets to its portfolio. The problem is that this solution is not enterprise-ready — it does not support rotation, dynamic Just-in-Time secrets, or any authentication methods beyond a simple username and password. Moreover, HCP Vault Secrets does not maintain “Zero Knowledge” for the vendor — HashiCorp has full access to the encryption and decryption of any customer secrets kept in HCP Vault Secrets.
What makes Akeyless SaaS Secrets Management Different
Akeyless Vault is a SaaS-based Secrets Management Platform. As a function of it being a SaaS and cloud-native product, it is easier to use, easier to deploy, and easier to manage. A SaaS platform takes care of all aspects of your infrastructure, maintenance and upgrades. To double click on this a bit more, you will not need to dedicate engineering resources to manage your Secrets Management infrastructure and to ensure high availability and data recovery for mission critical secrets.
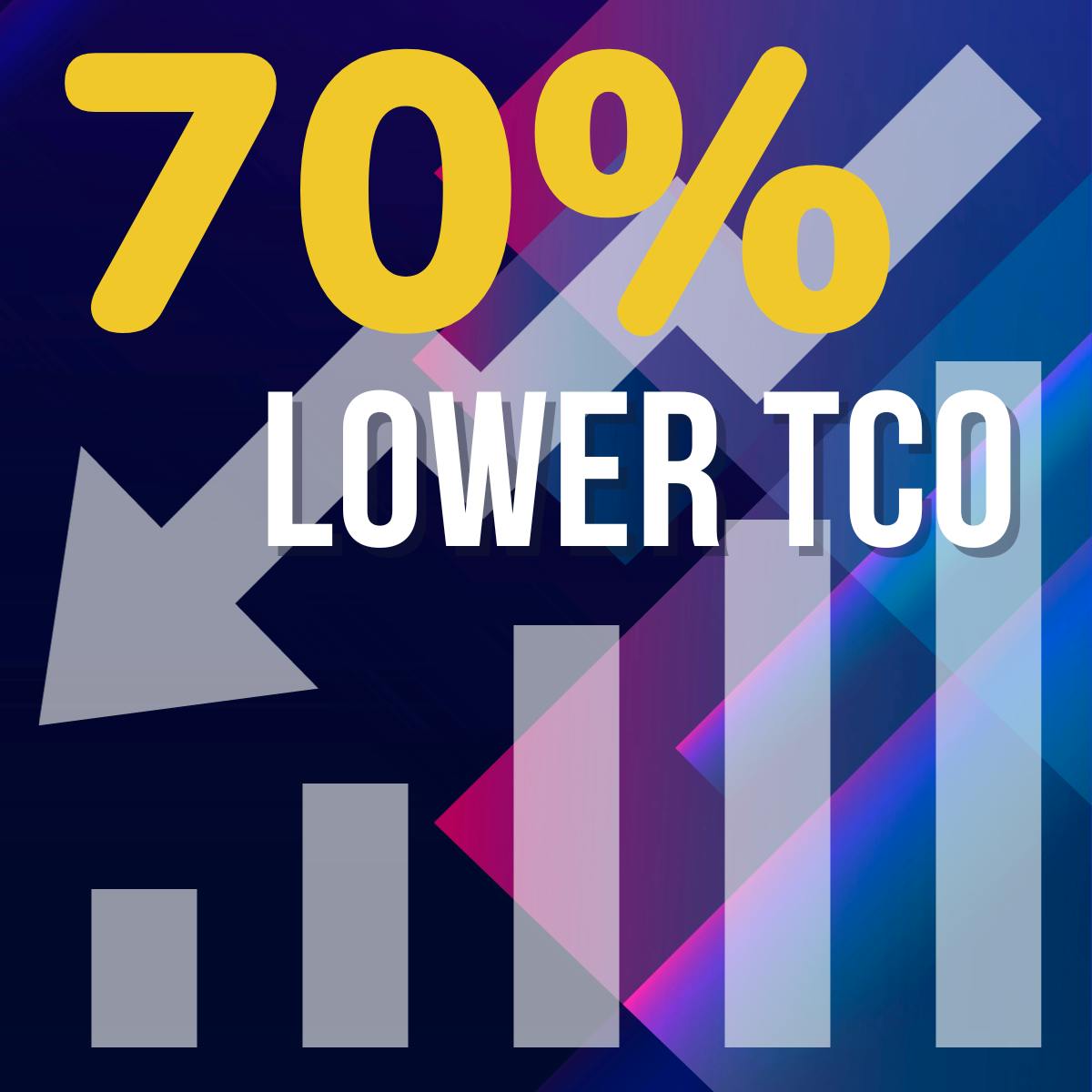
This also means that you reduce your total cost of ownership of a Secrets Management solution significantly. By significantly, we refer to customers who have reduced their TCO by up to 70%. And of course, there are many Fortune 100 companies who cannot be public references but have also offered to be internal references. If you want to hear about more examples of large enterprises across various verticals switching from HashiCorp Vault to Akeyless, all you need to do is ask.
Akeyless Integrates with Over 100 Tools and Plug-Ins for DevOps
You will also find that Akeyless is one of the world’s most DevOps friendly products. Check out our integrations here. We have been actively listening to our DevOps and DevSecOps communities to build integrations. Don’t forget to check out the last box, if you think we are missing anything, just let us know.
What do customers say about Akeyless Saas Secrets Management?
You will also see from our customer references and review sites like G2 that we bend over backwards with Akeyless deployment engineers and customer success teams to make sure you are elated with your choice of Secrets Management solution. Customer centricity is in our DNA.

So, what if you are a current HashiCorp Vault customer?
Easy. We work with a plug-in built for HashiCorp Vault, making migration seamless and with no heavy code refactoring.
What if you are using different vaults from different cloud service providers?
We know the majority of enterprises are not married to one cloud. But you are feeding secrets sprawl and complexity if you are using vaults from multiple cloud providers. You are better off with a multi-cloud SaaS Secrets Management solution like Akeyless. But that’s not all.
Akeyless is sort of like the one Ring that finds them all. The product is uniquely designed to be the “Secret Manager of all Managers”. With no migration or refactoring necessary, you can quickly mirror and manage secrets across popular secret managers like AWS, Azure, Kubernetes, and GCP.
Oh, wait a minute — I did start this blog by saying cyber security threats are on the rise, and we haven’t talked about security.
Refael Angel, our CTO, designed a proprietary encryption process that secures every secret stored in Akeyless. This technology is Distributed Fragments Cryptography, or DFC™, which makes it almost impossible for a hacker to access an entire encryption key at any given time and allows the organization to retain full ownership of their secrets by providing them with their own fragment of the encryption key. The organization’s fragment is stored safely within the walls of their environment, whether in the cloud or on-prem. Without it, no one can access and decrypt your sensitive data.
So let’s bring it home—how do you choose a Secrets Management Vault?
Four things to look for:
- It is easy to use, manage and maintain
- Reduces your TCO
- Enhances your security posture
- Is DevOps Friendly
This blog is just my attempt to consolidate how we can help in a few short paragraphs. If you want more details, you can find how we fare against HashiCorp Vault and all other vaults.
See how easy it is to migrate your Hashi secrets to Akeyless 👇
Please let us know if you would like to learn more. We would be happy to do a demo and answer any questions you may have.
P.S. We’re excited to share our latest report, “The 2024 State of Secrets Management.” Don’t miss this first-ever report with insights on Secrets Sprawl and managing secrets from over 200 cybersecurity experts world-wide. Enjoy!
Suresh Sathyamurthy
CMO, Akeyless Security





