Posted by Anne-Marie Avalon
January 23, 2024
Hit the ground running with this kick-starter Akeyless SaaS Secrets Management 101: Video Tutorial. Join Jeremy Hess, our expert Head of Customer Education at Akeyless, and gain hands-on expertise unlocking the full potential of Akeyless Vaultless® SaaS Secrets Management.
This tutorial series will have you operating at a whole new level of secrets mastery in no time. You’ll set up your FREE account, get familiar with the web front-end and CLI, create and share your first secret, then create and rotate some encryption keys with ease.
The second half of this series is all about authentication, a trifecta for your most common needs: RBAC, API Keys, and integrating with a trusted identity provider. What’s more, these video tutorials tightly align with the treasure trove that is the Akeyless documentation library.
Let’s go!
Lesson #1: Start Up Guide to Akeyless SaaS Secrets Managment
This first video introduces you to the revolutionary Akeyless Vaultless® SaaS Secrets Management. Learn the tremendous value that it brings as the all-in-one platform for secrets management. Akeyless enables key functionality for you to store, protect, rotate, and dynamically create all your credentials, including your keys, tokens, certificates, and more. This functionality benefits your human and machine access needs, whether through interaction with the web-based UI, the CLI, APIs, or SDKs.
Jeremy introduces you to all the key functionality of Akeyless Secrets Management and then shows you how to set up your free account. Just like that, you’ll be using the intuitive web-based UI of this SaaS platform and take the management out of secrets management. You’ll also learn how to establish an account for your organization.
Lesson #2: Install and Configure the Akeyless CLI
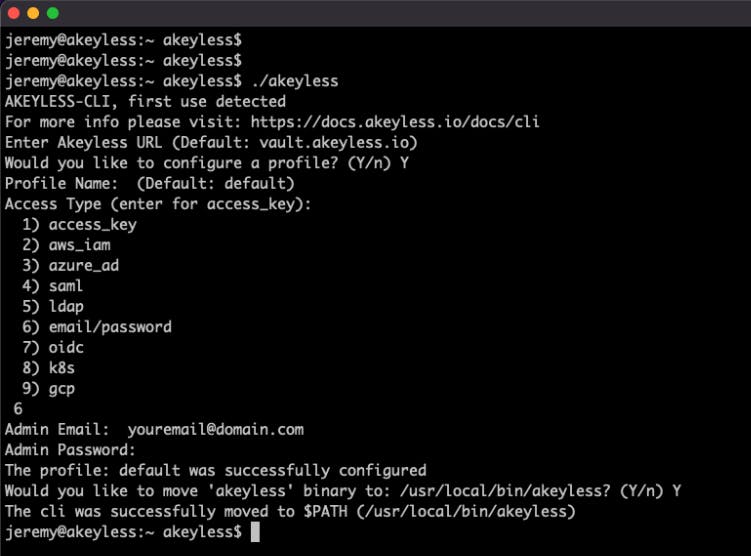
Now, let’s get our hands dirty and install and configure the Akeyless Command Line Interface (CLI). This tutorial shows you one of the most important ways that you and your DevOps/software engineers will interact with Akeyless. The CLI is purpose-built to serve their needs and to support your custom automation scripts.
Remember that treasure trove we were talking about? You’ll see how easy it is to use the Akeyless documentation library, as Jeremy walks you step by step through installing the CLI on a Linux platform. Then, he teaches you about profiles, setting one up, and validating that your account is working.
Lessons #3 and #4: Create and Share a Static Secret
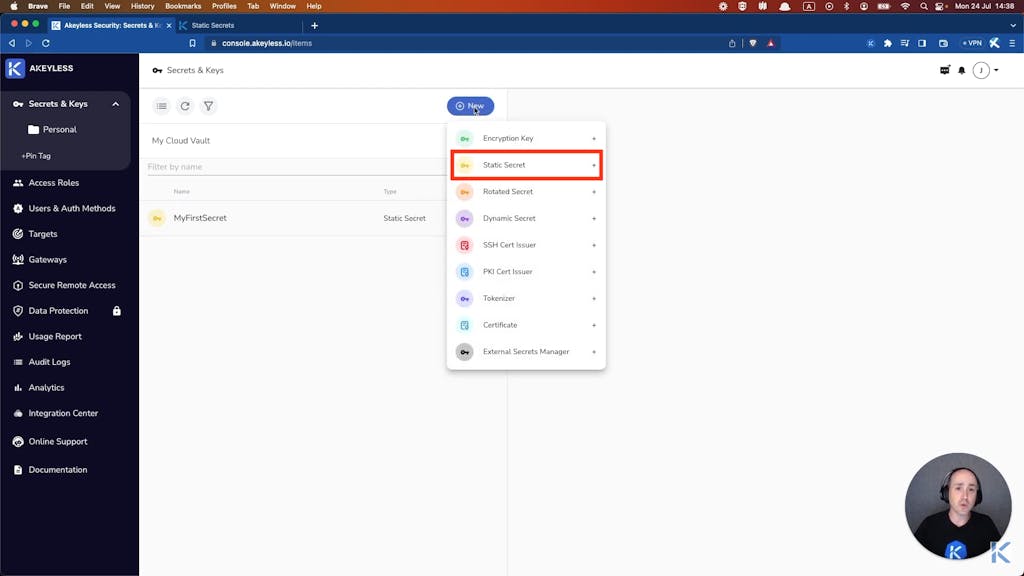
In this section we cover two important videos. The first one dives into the simplicity of creating a static secret in the Akeyless Vaultless®™ Platform. Since static secrets are, well, static (i.e., they don’t get changed very often), you need to make sure they are secured well (really really well). These are things like database credentials, API tokens and keys, encryption keys, service accounts, and the list goes on. There is likely a tremendous sprawl of static secrets throughout your environment, right?
Through this tutorial, you’ll navigate the web-based console, create a static secret, explore basic configuration settings, and learn how to update secret values. You’ll see firsthand why the intuitive interface makes it so simple to manage version control of secrets (e.g., review versions and roll back previous secrets). Then, of course, you’ll see how to do the same thing via the Akeyless CLI.
The next tutorial provides you with a simulation of a common scenario where we have one developer who wants to share their secret with another developer. This is where it gets interesting! Jeremy shows you how easy it is to share a static secret, with a time-based access rule and shareable link.
Lesson #5: Create and Rotate Encryption Keys

In this tutorial, Jeremy discusses, at a high level, cryptographic Key Types and some basic nuances between symmetric and asymmetric keys.
Then get an introduction to the groundbreaking Distributed Fragments Cryptography (DFC™) technology that makes vaultless a reality for Akeyless Vaultless® SaaS Secrets Management. You’ll learn how this technology creates keys in pieces and never combines them (hence, “fragments”). Your key never exists as a whole, so it can’t be used without your authorization. The fragment of the key that you keep (your own Customer Fragment) makes Akeyless a Zero-Knowledge encryption platform. Not the government, your CSP, nor your cyber adversaries can decrypt your data without all three fragments.
Finally, learn the step-by-step procedure for creating a DFC™ encryption key using both the web-based console and the Akeyless CLI.
Lesson #6: Authentication Methods and API Key Authentication

This video brings us into the home stretch, where you’ll learn about the Akeyless Vaultless® Platform authentication methods and API Key Authentication. You’ll receive a clear explanation of authentication methods for both workloads and humans. You’ll see how Akeyless provides you controlled and traceable access to all your secrets, and for methods, like with APIs, you can set it up, so they are managed with no human intervention required.
Then, Jeremy will run you through the process of selecting an authentication method, configuring an API key, and exporting everything you need (i.e., Access ID and Key). And, of course, you’ll learn how to do all of this in the web-based console and via the Akeyless CLI.
Lesson #7: Role-based Access Control with API Key Authentication

At the heart of least privilege stands Role-based Access Controls (RBAC). In this tutorial, Jeremy unfolds RBAC with API Key Authentication and he breaks down the delineation between authentication methods and access roles.
You’ll see how to use the web-based console and CLI for establishing roles and associating a permissions profile to the roles. Then, you’ll see how to use the specific authentication method established with the Access ID and Access Key in a demonstration, highlighting how the permissions are applied, giving the role a limited view (constrained to the associated permissions) within the console.
Lesson #8: AWS IAM Authentication and Access
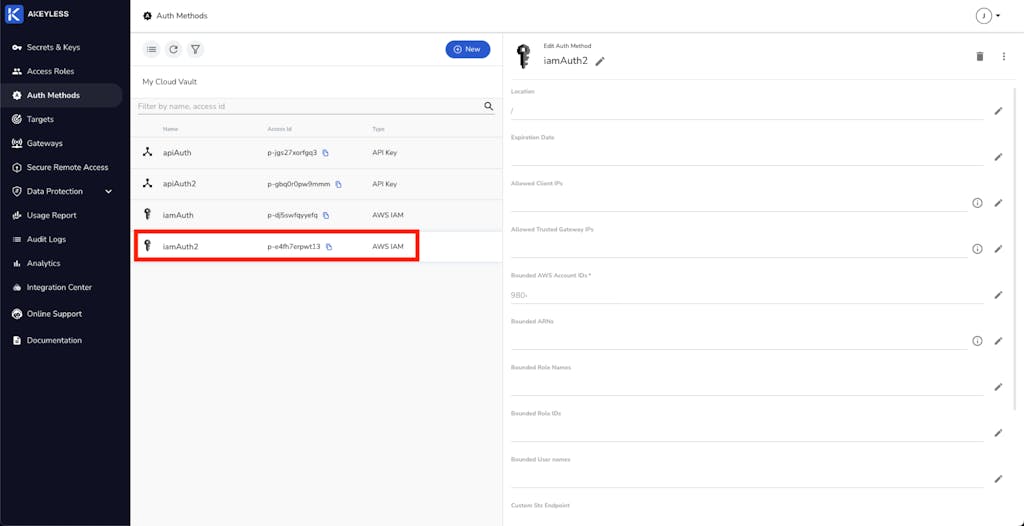
Pivoting from the previous lessons (where you learned how to configure authentication methods and access roles for human interaction), in this lesson Jeremy explains how to set up machine-to-machine authentication. You’ll learn how to integrate with a trusted identity provider—in this case, the AWS native Identity and Access Management service.
This demo touches on the high-level workflow of authentication using AWS IAM integrated with the Akeyless Vaultless® Platform. Then, it walks you through the step-by-step process for setting up the AWS IAM authentication method and configuring access roles. The demo covers the procedures for both the Akeyless web-based console and the CLI.
Excellent! You’ve already pulled ahead of the pack—now, let’s be sure to stay legs ahead of the threat. As we know, they don’t rest. You can wear them down by taking the next steps to evolve your secrets management strategy.
For a deeper dive into Akeyless and its innovative approach to Vaultless® Secrets Management, schedule a demo today!




