DevOps | Security
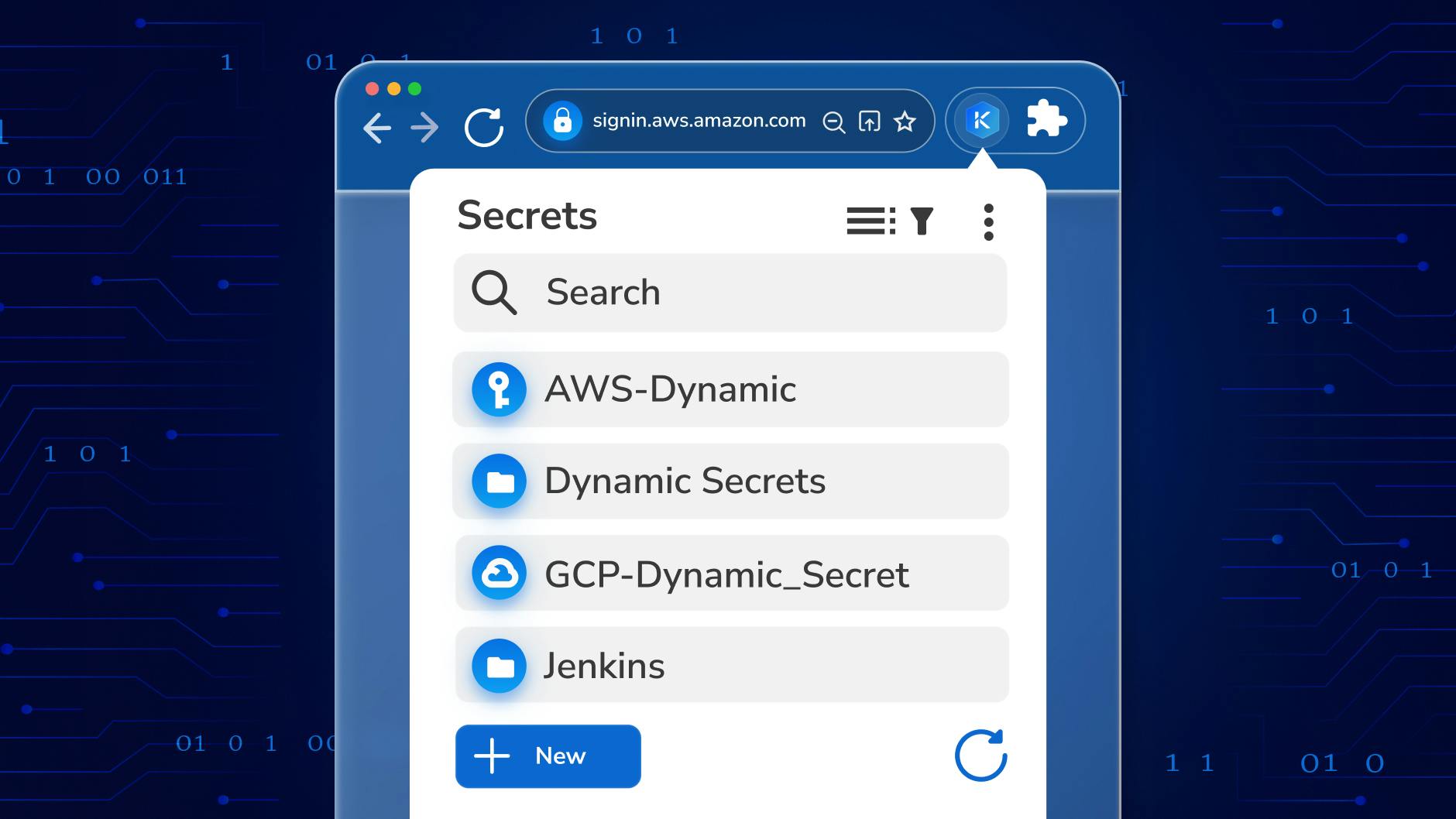
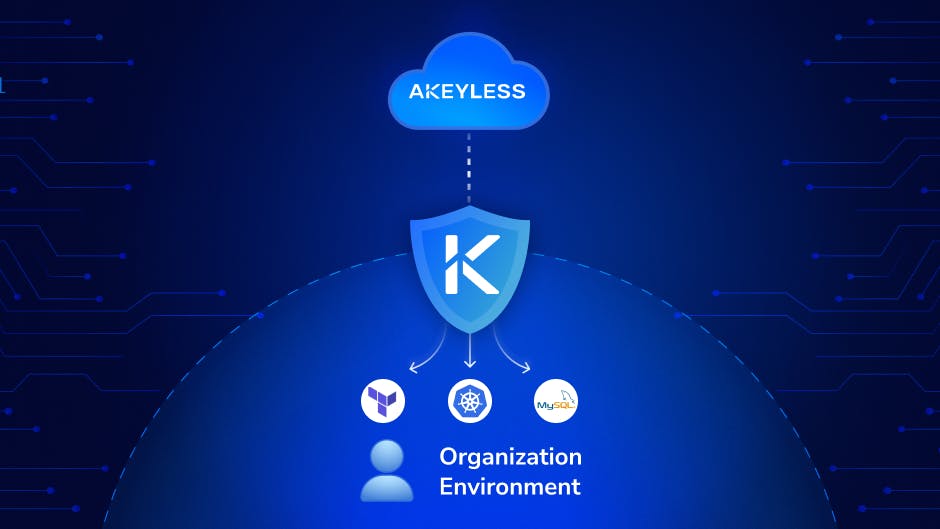
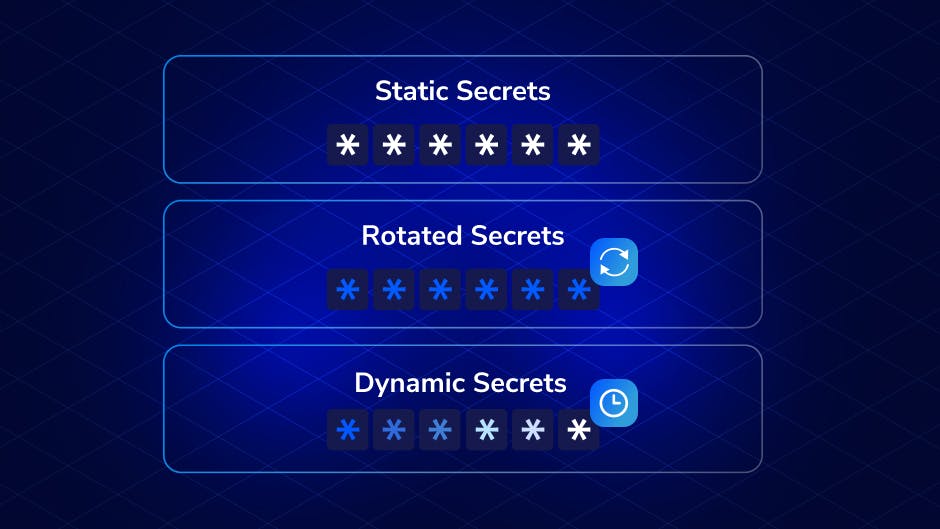
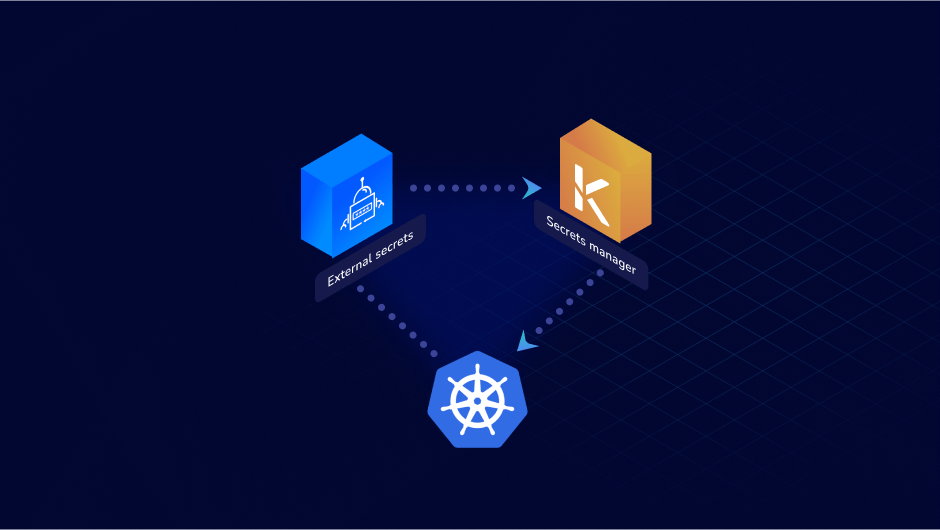
Secrets Management Debt: The Jenga Tower of SecuritySecrets management debt, the compounded burden of overlooked passwords, keys, credentials, and certifications, is like an unbalanced Jenga Tower threatening to collapse at any moment.