Posted by Anne-Marie Avalon
February 27, 2024
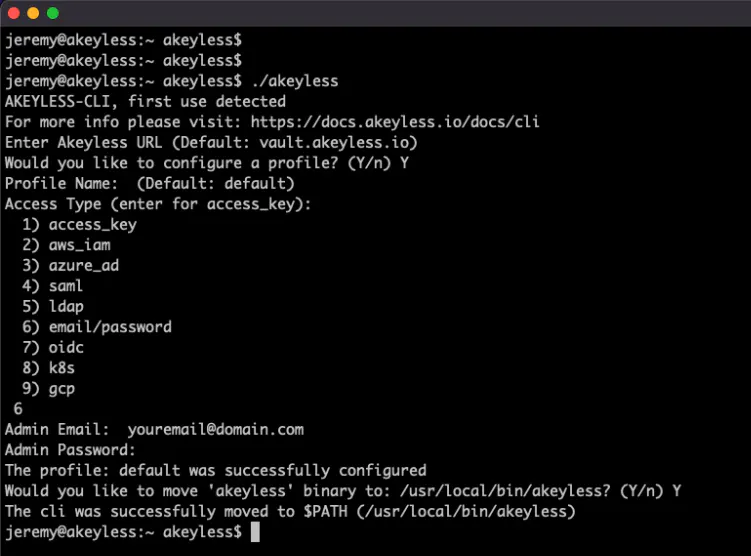
In this tutorial series, we’re going to help you elevate your secrets management. Join Jeremy Hess, our expert Head of Customer Education at Akeyless, to gain hands-on expertise and unlock additional functionality within your implementation of the Akeyless Platform.
These tutorials will elevate your operational skills to a new level in no time. Explore how to integrate and optimize functionality with Kubernetes, configure keyless SSH certificates, utilize a tokenizer, and integrate with KMS, enabling BYOK.
Let’s dive in!
Kubernetes Authentication
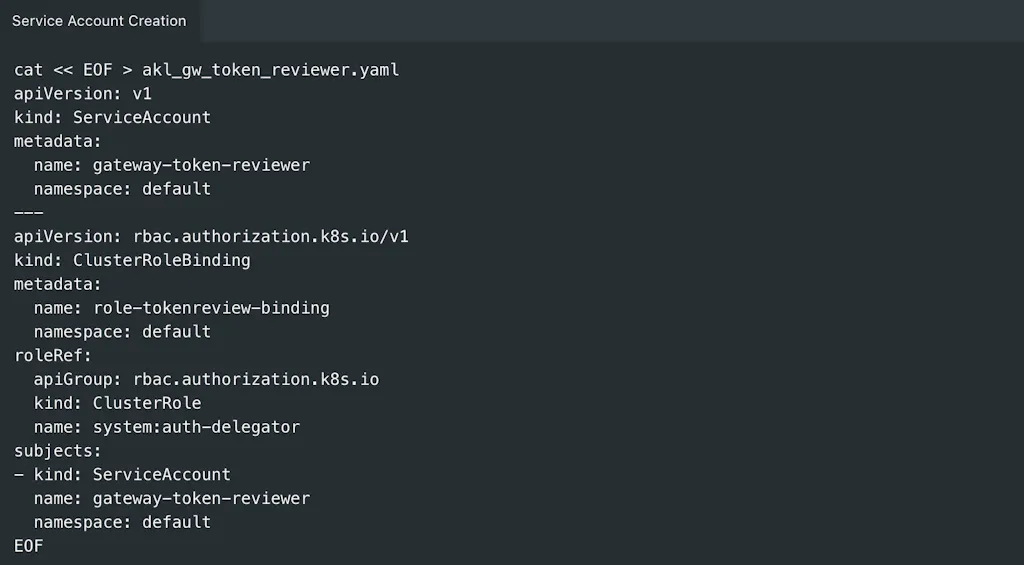
In our first lesson, Jeremy leads the journey into managing Kubernetes (aka K8s) secrets by showing how to authenticate a pod to Akeyless without ever sharing any private information with your SaaS. This functionality is crucial for Kubernetes authentication because it’s native, easier to work with for Kubernetes workloads, and enables more specific policies, segregation, and permissions for namespaces and pods, which are unavailable in native Kubernetes. Additionally, Kubernetes does not encrypt secrets by default—they’re stored Base64 encoded.
This tutorial outlines the prerequisites, including network access to the Kubernetes cluster and creating service accounts. It then guides you through actions such as creating a service account, extracting bearer tokens, obtaining Kubernetes Cluster CA certificates, and configuring the Kubernetes Authentication Method and Authentication Configuration in Akeyless via the CLI. The tutorial concludes by demonstrating how to authenticate from a service account within the Kubernetes cluster, ensuring correct configuration.
Ditch the Keys, Configure SSH with Certificates
Are you scaling your cloud infrastructure? Having issues keeping track of all those keys? Issuing, revoking, and managing keys can quickly become a burden. With Akeyless, you can eliminate this hassle and reduce the risk of misplaced or unaccounted-for keys. In lesson 2, learn the importance and practical implementation of SSH Certificates within the Akeyless platform, targeting administrators seeking enhanced security and streamlined management of server access in rapidly scaling cloud infrastructures.
This tutorial outlines prerequisites, including having a public-private SSH key pair within Akeyless via the CLI. Further instructions involve configuring the server to accept SSH certificates, generating a Certificate Authority (CA), and an SSH Certificate Issuer, and issuing user-specific SSH certificates. These certificates grant access to servers without requiring keys, ensuring secure and simplified SSH access management across your cloud environments.
More on Kubernetes – Let’s Inject Some Secrets
We’ve already touched on the advantages of using Akeyless for Kubernetes authentication—but there’s more. Since Kubernetes stores secrets unencrypted by default, anyone with access to your cluster can also access your secrets. With secrets sprawled through scripts, in repos, and buried in config files, they can cause operational bottlenecks. For a more microservices-based architecture, it’s better to manage your secrets externally. How about using Akeyless’ Kubernetes plugin?
In lesson 3, dive into the process of injecting secrets into Kubernetes. The prerequisites include having a K8s cluster and Helm installed, along with creating or using static/dynamic secrets in Akeyless. It guides you through creating a Kubernetes authentication method, associating it with a role, and configuring the Akeyless Kubernetes plugin using Helm charts.
The deployment and validation of Akeyless secrets injection into Kubernetes are demonstrated, detailing secrets injection through an init container and a sidecar container. This shows how secrets are injected into the pod’s filesystem at runtime. This comprehensive tutorial provides step-by-step instructions for deploying and leveraging Akeyless within Kubernetes for secure secrets management.
Sync Secrets to Kubernetes with External Secrets Operator
External Secrets Operator (ESO) is indeed a smooth operator. Many organizations have already put in a lot of effort to work with Kubernetes Secrets for their current environment and don’t want to change their workflows. With ESO and Akeyless, you can enhance your security for storing and managing the full lifecycle of your secrets with strong encryption.
The video explores the installation of ESO using Helm, creating a SecretStore resource to authenticate with Akeyless, and offers two methods for establishing the SecretStore. Additionally, it details the creation of an external secret to fetch secrets from Akeyless and store them securely within the cluster.
Tokenization-as-a-Service
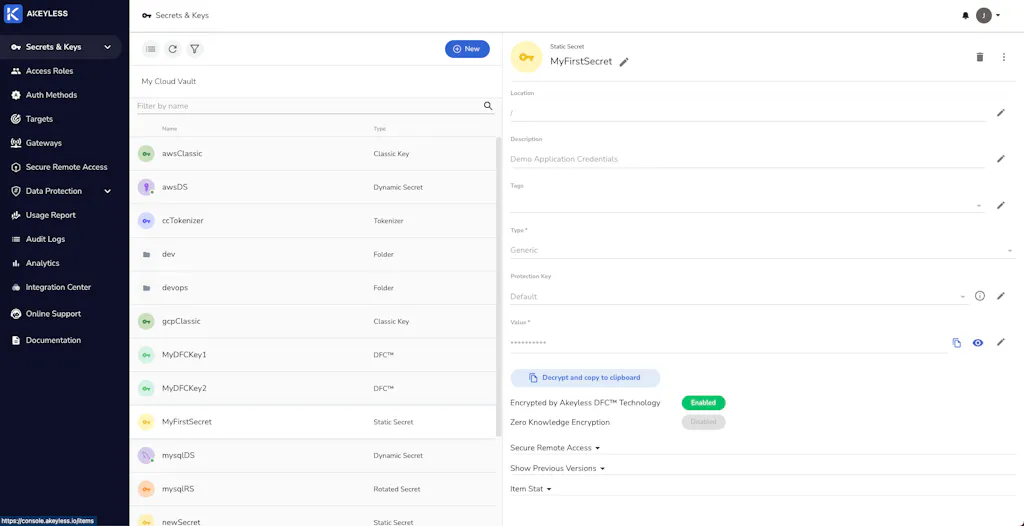
Tokenization is the process of encrypting sensitive data, like social security numbers, credit card numbers, phone numbers, etc. Akeyless offers tokenization-as-a-service and supports vaultless tokenization, meaning that a tokenized secret is not stored in Akeyless at any time during or after the tokenization process.
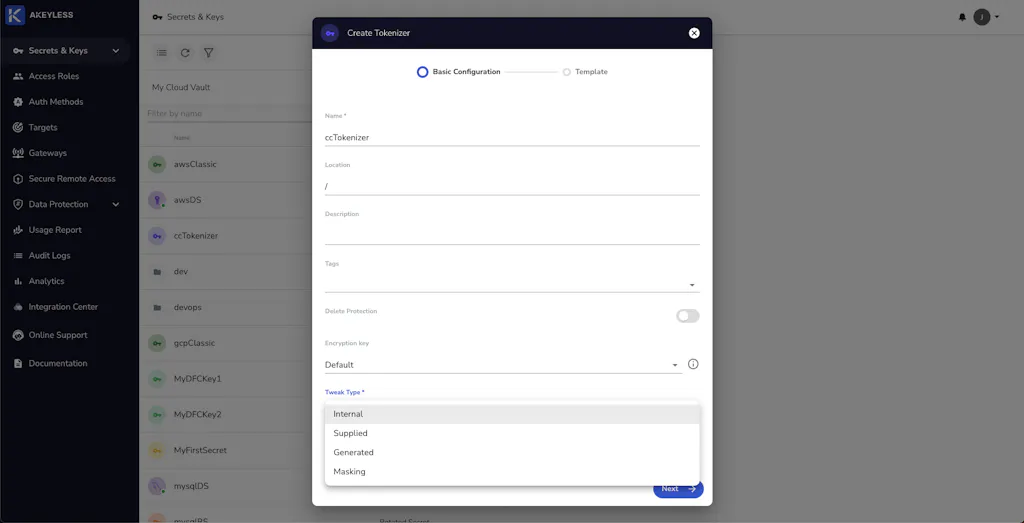
Learn how to create tokenizers using the Akeyless web-based console, detailing the required parameters and options for different tokenization methods. It further guides users on how to tokenize and detokenize data using the Akeyless CLI.
No matter what kind of data you need to secure, Akeyless tokenization enables you to encrypt it in a way that preserves the data format and its uniqueness.
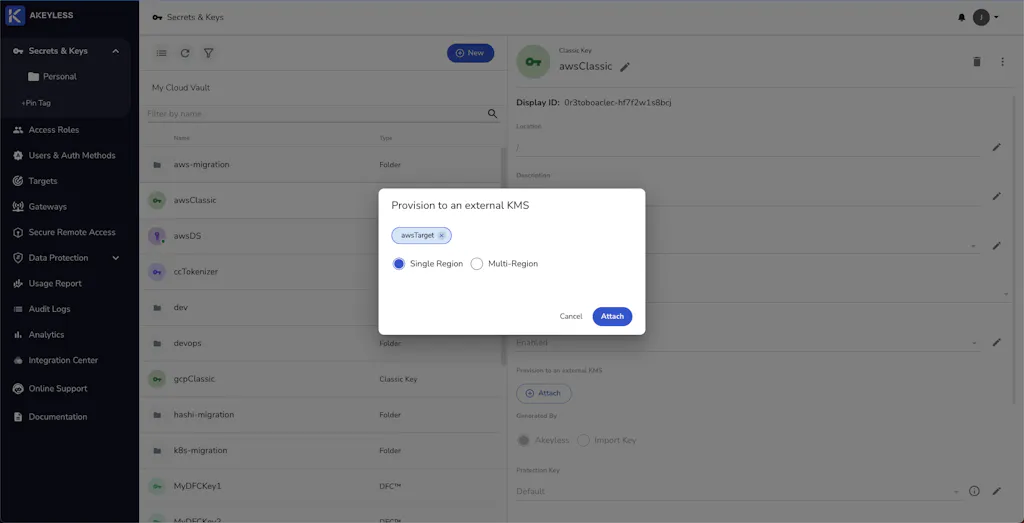
Multi-cloud KMS With Classic Keys and BYOK
That title is a mouthful—let’s break it down. Multi-cloud implies you are using services across two or more cloud providers, like AWS and GCP. KMS is your traditional Key Management System, i.e., the platform you use to create and manage your cryptographic keys. Classic keys are encryption keys managed within the Akeyless KMS, which can be shared with your cloud KMS or used as an encryption key to protect your secrets, enabling BYOK (Bring Your Own Key).
This video shows you how to securely transfer key material to the respective cloud KMS according to their import specifications. Then, see how to identify and manage key versions within each cloud provider’s KMS.
Akeyless KMS manages the entire key lifecycle, including secure generation, storage, access control, and logging of key usage. The integration with cloud providers like AWS and Google Cloud Platform (GCP) is demonstrated through step-by-step instructions for creating Classic Keys, associating them with cloud targets, and rotating keys both via the Akeyless UI and CLI tools.
For a deeper dive into Akeyless and its innovative approach to Vaultless® Secrets Management, schedule a demo today!




