Posted by Sam Gabrail
May 6, 2025
Keeping secrets safe is one of the biggest challenges for any company today. By “secrets,” we mean things like passwords, API keys, certificates, and other sensitive information. Protecting these is super important because losing them or having them leaked can cause big security issues, data breaches, and serious business disruptions.
Today, we’re taking a closer look at two popular secrets management tools for managing secrets—HashiCorp Vault and the Akeyless Platform. Specifically, we’ll see why many companies are moving from Vault to Akeyless to save money and make life easier for their teams. The Akeyless Platform is known for its advantages in operational cost reduction and maintenance-free management, making it a compelling choice for businesses looking to enhance secure access and data protection. Let’s dive right in!
Video
Introduction to Secrets Management
Secrets management is a critical discipline of cybersecurity that involves securely storing, managing, and accessing sensitive data such as API keys, encryption keys, and database credentials. As organizations increasingly rely on cloud providers and external services, the need for robust secrets management solutions has become more pressing. Effective secrets management helps protect sensitive data from unauthorized access, ensuring that only authorized users and systems can retrieve and use these secrets.
HashiCorp Vault and Akeyless are two prominent solutions in the realm of secrets management. Both offer tools to help organizations safeguard their sensitive data, but they differ significantly in terms of cost, ease of use, and scalability. In this article, we will explore why many organizations are choosing Akeyless over HashiCorp Vault to meet their secrets management needs.
Why Secrets Management Matters
Secrets management means securely storing and managing sensitive information that your applications, services, and teams need. Good secrets management helps you:
- Keep passwords and keys secure.
- Avoid expensive data breaches.
- Prevent unexpected downtime.
- Meet security regulations.
Without proper management, your company could face severe consequences—data leaks, operational halts, compliance penalties, and damage to your brand’s reputation. That’s why choosing the right solution is crucial for keeping your company safe and running smoothly.
Challenges with HashiCorp Vault
HashiCorp Vault is popular, but it comes with some big challenges, including the high cost of scaling and managing the platform.
High Licensing Fees and Hardware Costs
Vault often comes with expensive licensing costs and demands significant hardware investments, especially as you scale up. Each region where your teams operate typically needs its own fully set-up Vault cluster, meaning the cost multiplies fast as your company grows.
Complex Setup and Management
Vault is powerful but complicated. Setting it up correctly takes specialized knowledge and a lot of time. It requires continuous management and regular maintenance, which means ongoing costs for hiring experts or dedicating internal staff to manage it.
Multi-Region Deployment Requirements
If your company has teams and apps all over the globe, Vault becomes even more challenging. Each geographic region usually needs its own Vault setup to keep things running quickly and reliably. This multiplies both hardware expenses and operational complexity significantly.
Not All Secrets Replicated
Vault only replicates static secrets automatically across active clusters. This means your team might face issues accessing necessary dynamic secrets and tokens quickly when operating internationally, slowing your operations and increasing frustration.
Introducing Akeyless
So, how does Akeyless solve these challenges?
Cloud-Native and Easy Deployment
Akeyless is designed as a true SaaS secrets management solution. Being cloud-native, it’s ready-to-go right from the start. You don’t need to set up any complex hardware or maintain heavy infrastructure yourself. The SaaS convenience simplifies deployment and reduces ongoing maintenance. Deployment is simple and quick, and there’s basically zero ongoing maintenance. This saves both time and money.
Cost-Effective Pricing Model
Instead of big upfront investments, Akeyless offers a simple pay-as-you-go pricing model. This approach provides significant value by ensuring cost-efficiency and operational efficiencies. You only pay for what you use, which makes scaling predictable and affordable. As your company grows, your secrets management costs stay under control—no surprises.
Easy Scalability and Flexibility
Akeyless uses stateless gateways placed at the edge of your private network. These gateways connect securely to the SaaS backend via simple outbound communication, meaning no complicated network configurations. This clever design lets your company grow across many regions without adding clusters and additional costs.
Architecture Comparison: Vault vs. Akeyless
Let’s take a closer look at the architectures of HashiCorp Vault and Akeyless to understand why their differences matter so much.
HashiCorp Vault’s Architecture
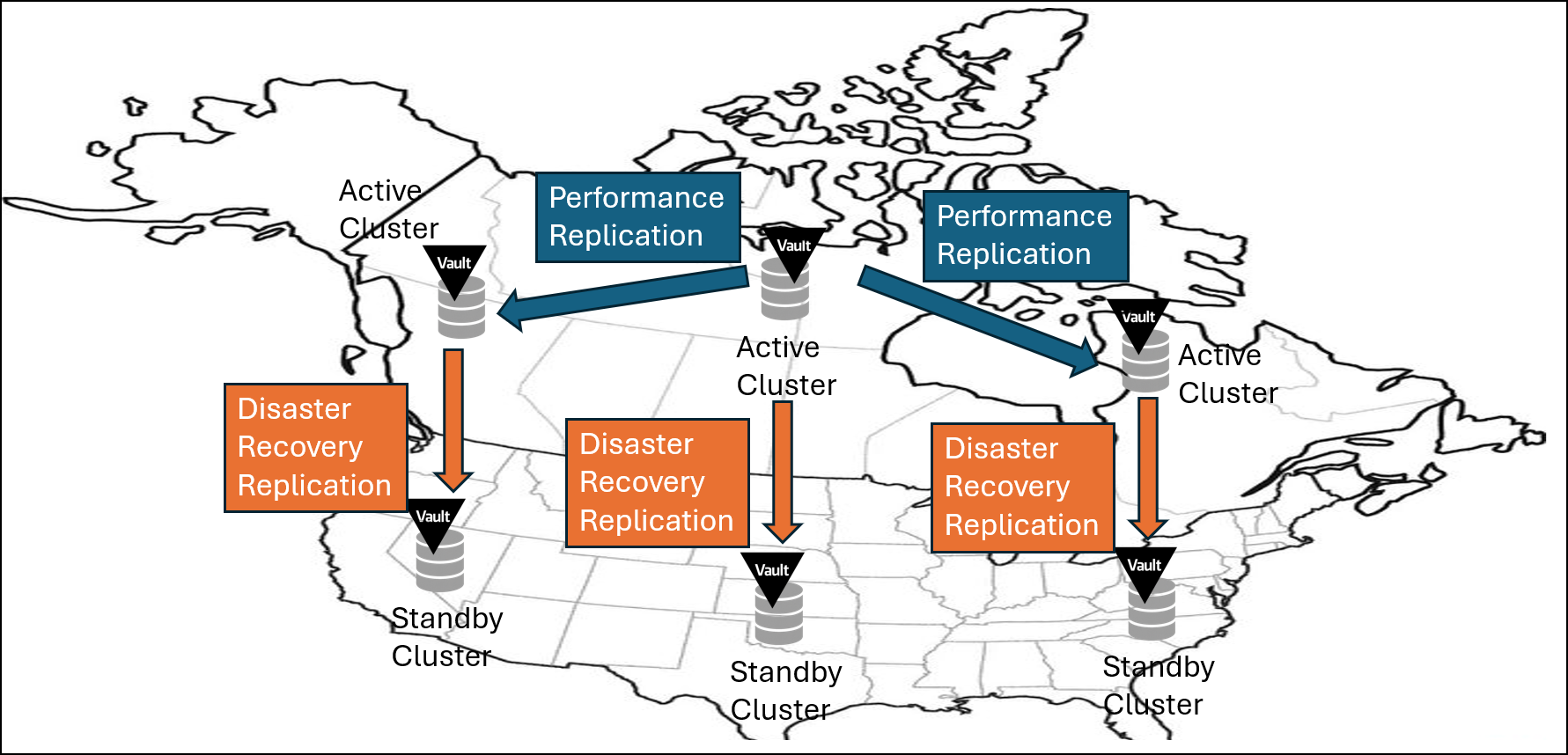
Vault’s architecture, shown in the image above, requires multiple fully operational clusters, each deployed separately in every region where your business operates. Each of these clusters includes both active and standby clusters.
Vault uses two types of replication between these clusters:
- Performance Replication (PR): This type of replication allows multiple active clusters to communicate and replicate data with each other for higher performance and availability. You would have one primary active cluster for all write operations. The other secondary active clusters are used for read operations. Any write operations are forwarded to the primary cluster. This architecture is suitable for active-active applications.
- Disaster Recovery (DR) Replication: Each active cluster maintains its own dedicated standby cluster either in-region or out-of-region to quickly recover in case of failure. The recovery process is manual in nature and human intervention is necessary. This is by design since it’s difficult to determine if a cluster is truly down or a network blip occurred. Once your engineers determine that the cluster is truly down, they need to run a promotion procedure to promote the DR cluster to become operational. This architecture is suitable for active-standby applications.
When you have applications spread out in different geographical regions, you need a Vault cluster in each region to minimize application latency. This in turn increases both your initial setup costs and ongoing expenses. It also adds complexity as you need to know how your application operates and whether you can use performance or disaster recovery replication or both. As a result, your teams and applications might face delays or complications accessing secrets consistently if you don’t pay close attention to your design.
Items that Get Replicated in case of PR or DR
Below is a table showing what gets replicated in case of using PR or DR
| Capability | PR | DR |
|---|---|---|
| General Configuration like policies and authentication methods | Yes | Yes |
| Secrets Configuration | Yes | Yes |
| Static Secrets | Yes | Yes |
| Dynamic Secrets | No | Yes |
| Token Replication | No | Yes |
| Secondary Clusters Handle Requests | Yes | No |
Akeyless’s Architecture: A Smart, Vaultless Approach
Akeyless takes a completely different path with its innovative “vaultless architecture.” Instead of the heavy clusters needed by traditional secrets management tools, Akeyless combines the benefits of SaaS technology with unique security features to solve common problems found in both SaaS solutions and traditional vault-based architectures.
Understanding the Vaultless Architecture
The main part of Akeyless architecture is its centralized SaaS backend. This backend is hosted securely in the cloud and is responsible for securely storing and managing all your organization’s secrets. But unlike other SaaS solutions, Akeyless never initiates inbound communication into your network. Instead, it uses special gateways that communicate outbound from your internal network, ensuring your infrastructure stays safe and secure.
The immediate concern that came into my mind when I looked into Akeyless was that it’s a SaaS offering and Akeyless could potentially have access to my secrets. Then I learned how Akeyless uses Distributed Fragments Cryptography (DFC) as part of their enterprise grade security. With zero knowledge encryption you have complete control over your secrets; even Akeyless does not have access to them.
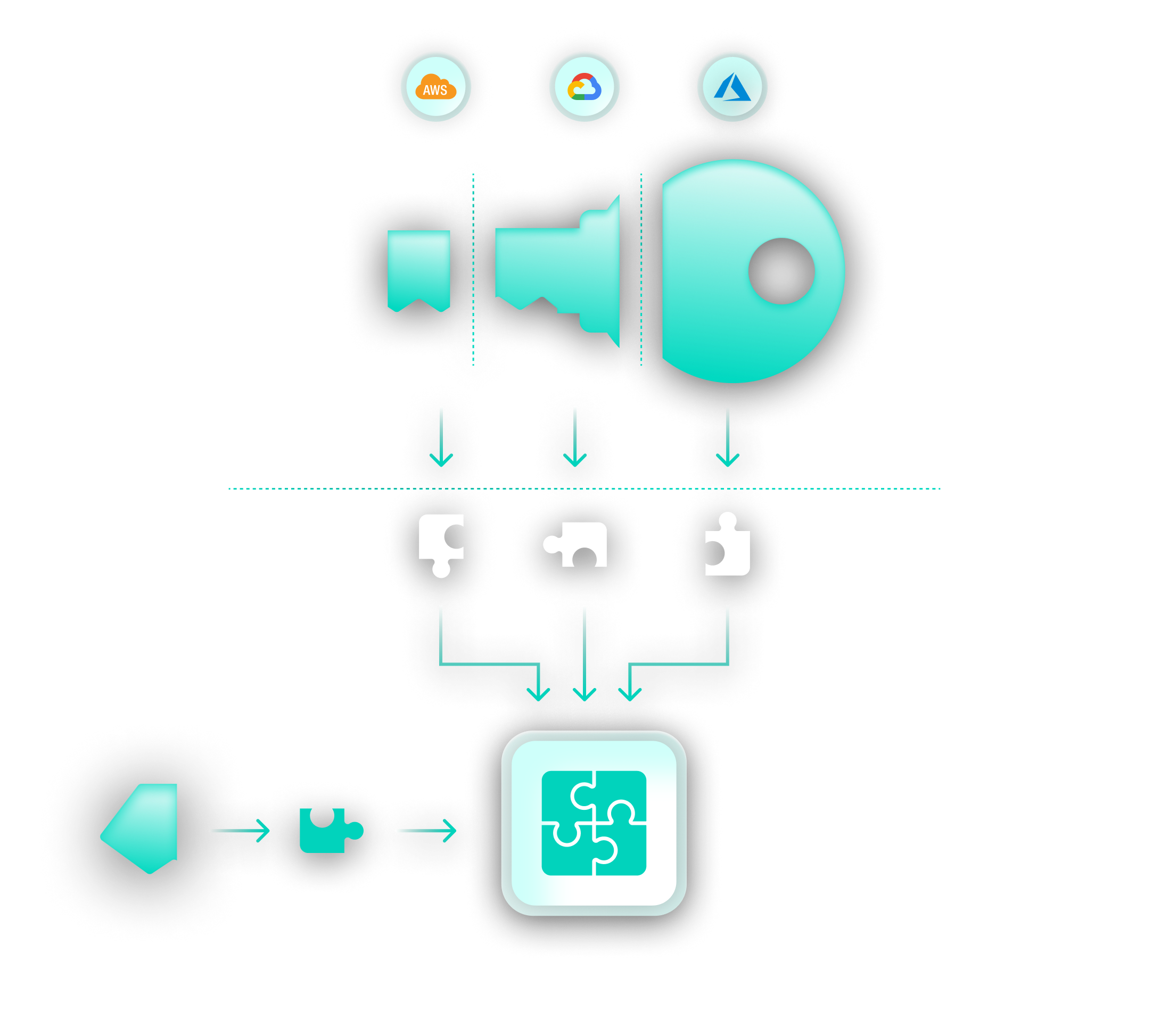
In Akeyless’ own words from the above link:
Since Akeyless DFC enables Akeyless to perform cryptographic operations WITHOUT EVER COMBINING the encryption key, one of the key fragments can actually be on the customer’s environment, where Akeyless has no access. This means that Akeyless, as a service provider, won’t be able to decrypt any data that is encrypted by our customers (who hold one of the key fragments). The reason is simple: we don’t have access to your fragment.
Therefore, in order to enable Zero-Knowledge Encryption, all you need is your own Customer Fragment.
Akeyless Gateways: Lightweight and Stateless
Instead of managing full-scale vault clusters, Akeyless deploys lightweight, stateless gateways within your organization’s environment. These gateways run as simple, efficient services and can be set up using a single Docker command, making deployment quick and straightforward. They require minimal ongoing management, which significantly reduces operational costs and complexity.
Key benefits of these gateways include:
- Outbound-Only Communication:
Gateways never allow inbound traffic from the SaaS platform. All connections are initiated from within your internal environment, reducing your risk of external breaches through the SaaS provider. - Stateless Operation:
Being stateless, these gateways don’t store sensitive data or state locally. This makes them secure, easy to scale, and straightforward to maintain. - High Availability and Performance:
The gateways include caching mechanisms. If your network temporarily loses its connection to the SaaS backend, the gateway can continue providing secrets from the cached information, ensuring your critical applications remain operational.
Architecture in Action (Illustrated)
To visualize how this works, let’s refer to the provided architecture diagram:
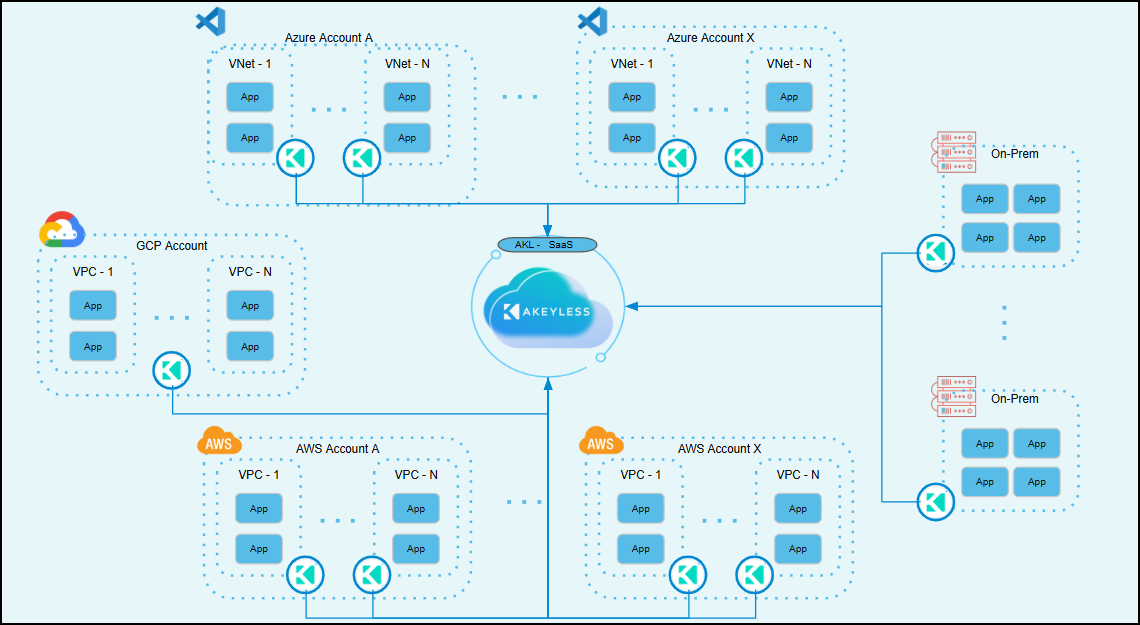
This diagram clearly shows Akeyless managing secrets seamlessly across multi cloud environments (AWS, Azure, GCP), regions, and even traditional on-premises infrastructure. Each of these environments hosts their lightweight gateways that securely connect to the central SaaS backend.
Here’s how it flows:
- Multi-Cloud & Hybrid Support:
Gateways can be easily deployed in each cloud account, region, or on-prem location, providing consistent and secure secrets management across your entire infrastructure. - Secure Communication:
All communications from these gateways to the SaaS backend occur securely and outbound-only. The SaaS never initiates a connection into your network, greatly reducing your security exposure. - Unified Secrets Management:
Regardless of the platform (cloud or on-prem), your secrets are centrally managed. This centralized control greatly simplifies operations and ensures consistency across your entire IT landscape.
Why Does This Architecture Matter?
This modern, SaaS-based architecture significantly reduces your cost and complexity, especially compared to traditional vault setups. By removing the need for complex replication strategies, expensive infrastructure in every region, and specialized management expertise, your organization saves significantly on hardware, licensing, and maintenance costs.
Moreover, the design inherently enhances security and compliance by limiting your exposure to threats and vulnerabilities common in other secrets management solutions.
Cimpress Case Study: How Akeyless Delivered Big Savings
Let’s take a real-world example to see exactly how this works. Cimpress, a large global company with over 12,000 employees and revenues above $2 billion, faced challenges managing secrets effectively with Vault.
Cimpress had a large central security team, with about 30 experts managing secrets globally. But they found Vault costly and hard to scale efficiently across their operations. They decided to switch from Vault to Akeyless, and the results were impressive.
Benefits Realized by Cimpress with Akeyless
70% Cost Reduction
Switching to Akeyless, Cimpress immediately saw huge cost savings. Lower licensing fees, reduced hardware costs, and virtually no maintenance meant they saved an impressive 70% on their overall secrets management expenses.
270% Higher Adoption
Because Akeyless was easy to use and quick to integrate, teams across Cimpress adopted it eagerly. In fact, adoption rates jumped by an incredible 270%! Employees and engineers appreciated the intuitive interface and the simplicity of onboarding.
Reliable & Scalable Performance
Akeyless delivered reliable performance everywhere Cimpress operated, without needing separate clusters. Their teams around the world could access the secrets they needed instantly, boosting productivity and reducing operational headaches.
(You can explore more details in the full Cimpress case study here.)
Highlights From the Demo
Let’s quickly walk through what it looks like in action:
Dashboard Tour
The Akeyless dashboard is designed to be user-friendly. You get a clear view of your secrets and management tools immediately upon login. Navigation is straightforward, letting you find and manage secrets quickly. This is another aspect I like about Akeyless, their UI is much more mature than Vault’s.
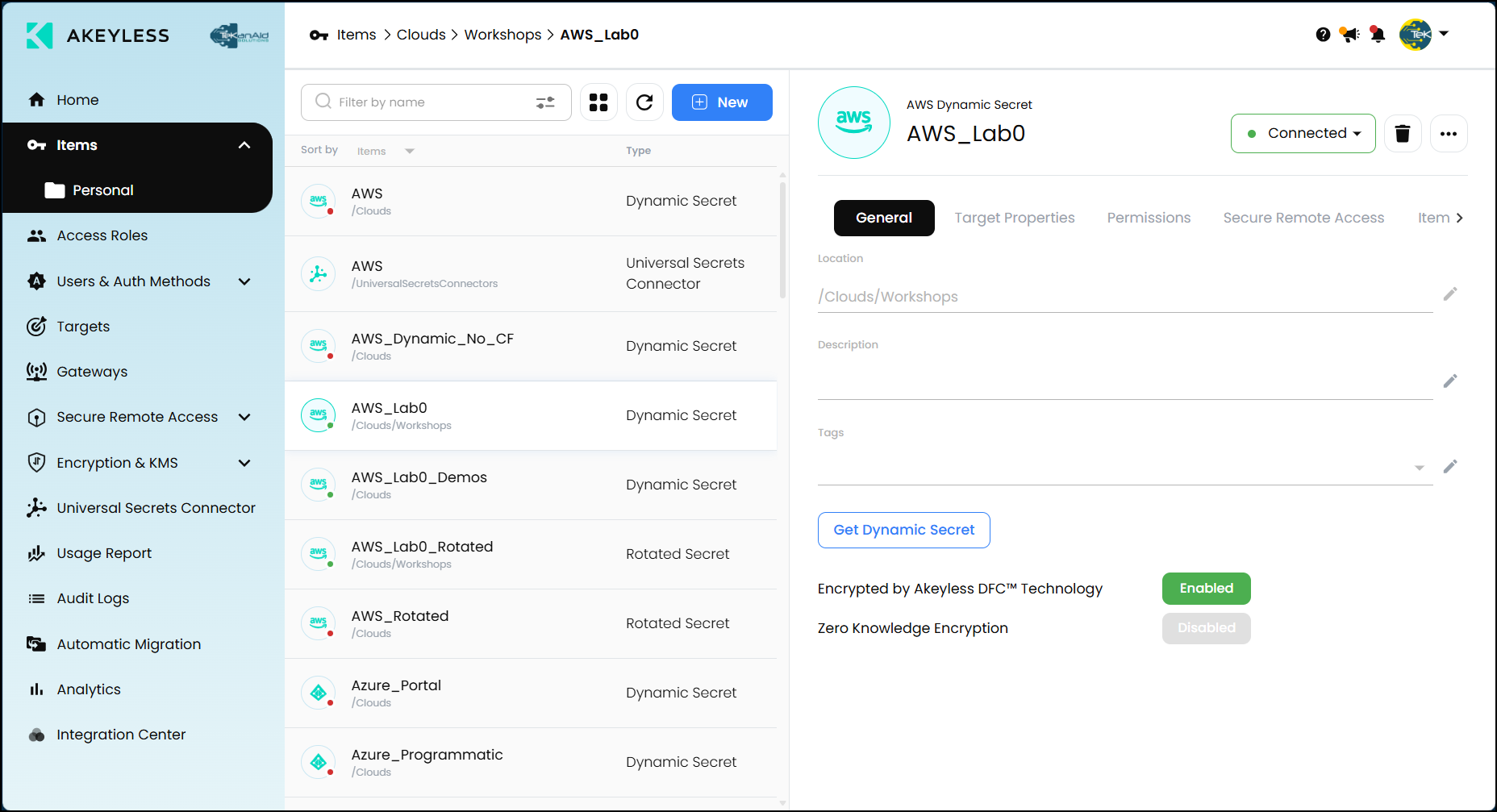
Secrets Management Example
Creating and accessing secrets is simple. You can store a secret securely via the dashboard or through easy-to-use CLI commands. Retrieving secrets is just as fast, making Akeyless practical for daily use.
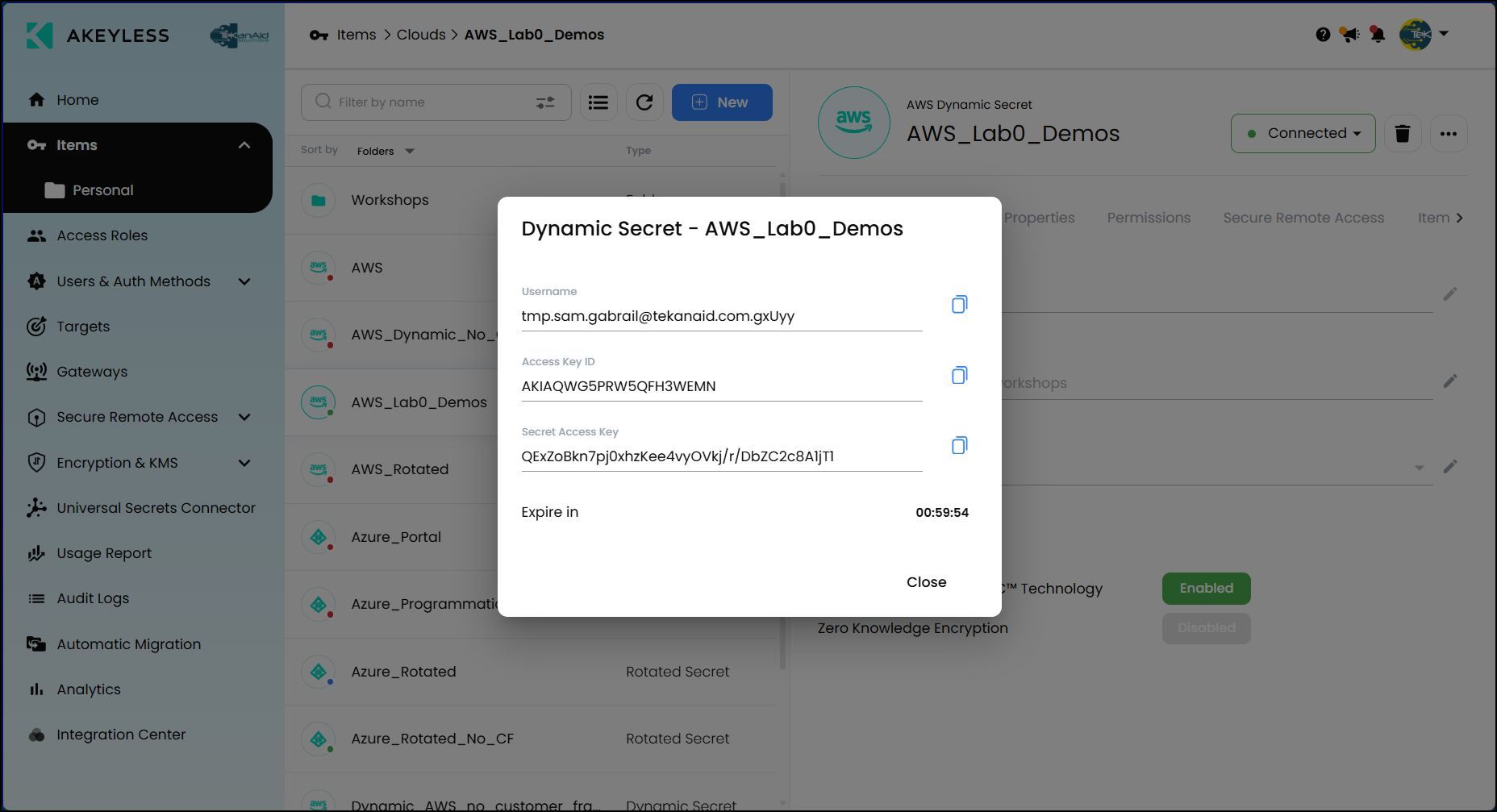
Let’s look at a real example of managing dynamic secrets. In this demo, I’ve created an AWS dynamic secret. Dynamic secrets are temporary credentials that Akeyless generates for you automatically. Here’s an example of what these credentials look like:
- Username: Generated automatically
- Access Key ID and Secret Access Key: Securely generated by Akeyless in AWS
- Expiry Time: Automatically set to expire in one hour
This approach means your secrets are short-lived, significantly reducing the risk of credential leaks or misuse.
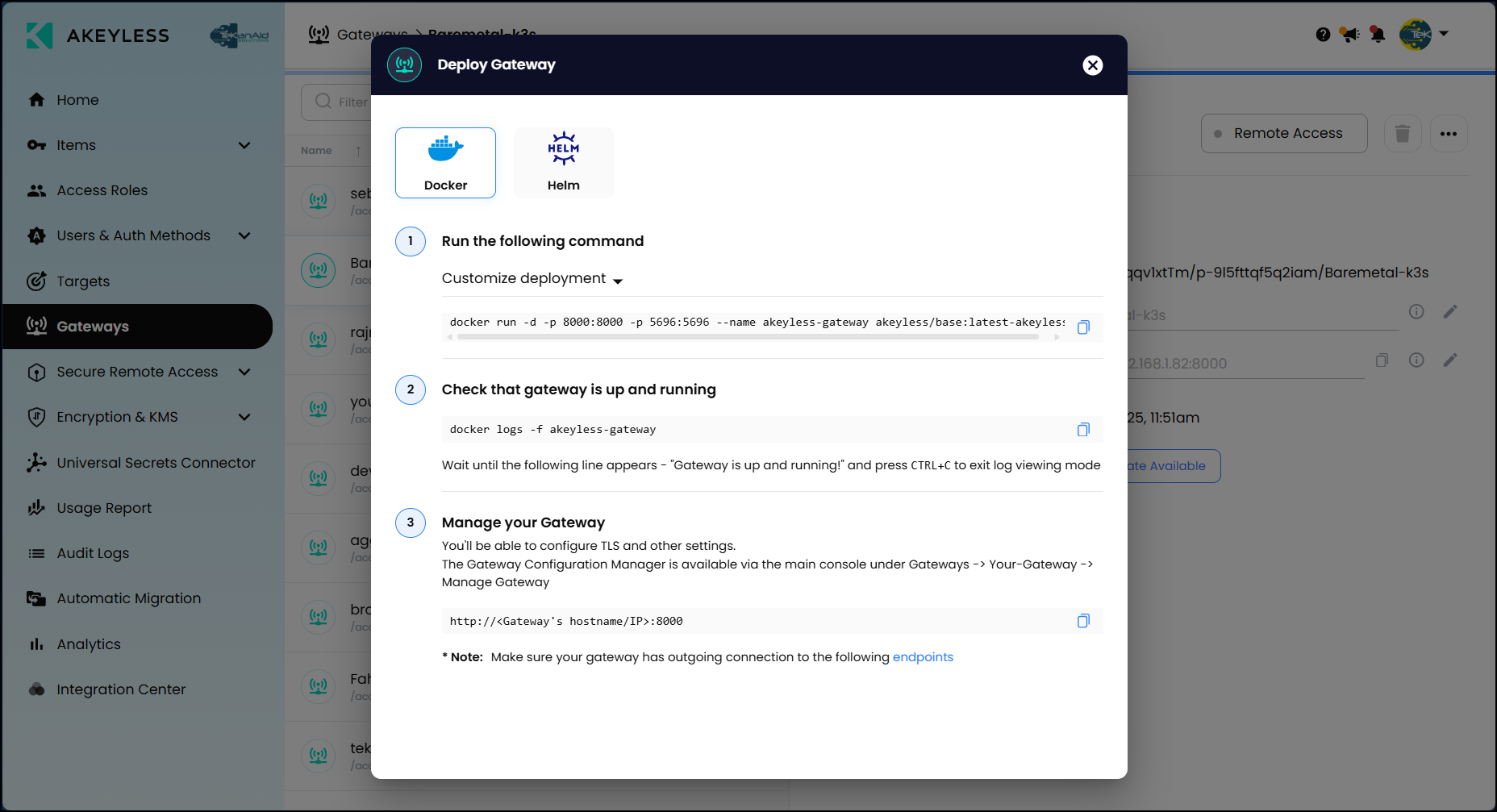
Gateway in Action
Now, let’s see the Gateway setup in action. Deploying an Akeyless Gateway is straightforward—you simply run a Docker or Helm command provided by Akeyless. Once up, the Gateway automatically connects to the Akeyless SaaS backend. Here’s how easy it is:
- Run the Docker command provided by Akeyless.
- Check the gateway logs with a single command to confirm it’s running.
- Use the Gateway to securely handle your dynamic secrets.
This means your team won’t need complex setup procedures. The Gateway seamlessly manages dynamic secrets, automating frequent rotations to enhance your security posture without extra effort from your side.
Vault vs. Akeyless – Quick Recap
Below is a table with a quick recap of what we talked about in this article. If you want to dig deeper into the comparison and see more of Akeyless features, check out this blog post Akeyless: The Leading HashiCorp Vault Alternative.
| Feature | Vault | Akeyless |
|---|---|---|
| Cost | High (hardware + licensing) | Low (pay-as-you-go, stateless gateways) |
| Complexity | Complex deployment and management | Simple, cloud-native setup |
| Deployment | Full clusters needed in each geographic region | Edge gateways with central SaaS backend |
Final Thoughts: Why Akeyless is a Smarter Choice
Choosing the right secrets manager means selecting one that saves money, simplifies your life, and scales smoothly with your business. Akeyless clearly offers advantages over Vault:
- Dramatic cost savings.
- Easier setup and management.
- Seamless scalability across regions.
- Better adoption across teams due to its user-friendly approach.
Next Steps: Get Started with Akeyless
Ready to see Akeyless in action for yourself? Check out a demo or contact their sales team to discuss your needs in detail. Find out firsthand how Akeyless can simplify secrets management at scale for your company, saving both time and money along the way.
Make managing secrets less of a headache and more of a competitive advantage with Akeyless today!




