Posted by Refael Angel
December 23, 2025
Summary
Enterprises no longer need to choose between SaaS convenience and control over secrets, certificates, and encryption keys. A zero-knowledge security architecture allows secrets management to operate via a cloud-based platform while ensuring only the organization retains access to sensitive credentials. Akeyless implements this model using Distributed Fragments Cryptography™, enabling regulated enterprises to adopt SaaS-based secrets management without relying on vendor trust.
SaaS vs. On-Prem
SaaS has reshaped enterprise IT by delivering speed, scale, and operational simplicity. In most areas of the stack, the model has proven itself.
Security has been different.
When it comes to protecting sensitive assets, many organizations still face a familiar trade-off. Cloud-hosted platforms offer ease of use and rapid adoption, but often require implicit trust in the provider. On-prem systems preserve direct control, but introduce complexity, cost, and ongoing maintenance.
A Structural, Not Cultural, Problem
This tension is not about risk tolerance or cloud skepticism. It is an architectural limitation. Most security systems were designed for either centralized control or provider-managed convenience, but not both at the same time. As a result, enterprises have been forced to choose between agility and assurance.
Why Secrets Change the SaaS Equation
As enterprises have moved more workloads to the cloud, the nature of what needs to be protected has shifted as well. Modern environments rely heavily on machine-to-machine access, APIs, and automated workflows, all of which depend on secrets, certificates, and encryption keys to function securely.
These assets sit beneath the surface of applications, but they define how systems authenticate, communicate, and establish trust. They control access to databases, services, and infrastructure, and they protect data as it moves and as it rests.
The Difference Between Data and Control
If an attacker gains access to business data, the impact is serious. If they gain access to secrets, the consequences are systemic. Credentials unlock systems, bypass controls, and undermine every dependent security mechanism.
This is why secrets management creates a higher bar for cloud adoption. The issue is not whether a provider is reputable or well secured. It is whether the architecture prevents anyone other than the organization itself from accessing sensitive credentials at all.
Why Regulated Industries Feel This First
In highly regulated industries, security decisions are rarely abstract. They are shaped by concrete requirements around ownership, auditability, and accountability.
Organizations in financial services, healthcare, government, and critical infrastructure operate under expectations that go beyond best practices. They must be able to demonstrate who controls sensitive credentials, where cryptographic material resides, and what technical safeguards prevent unauthorized access.
Trust Is Not an Acceptable Control
Even well-secured platforms can struggle to satisfy regulators and internal risk teams if the underlying architecture still allows a third party to hold or reconstruct sensitive material. As a result, many regulated enterprises have delayed implementing cloud-native secrets management in production environments. The concern is not cloud technology itself, but architectures that rely on trust where technical proof is required.
Traditional Approaches Fall Short
Most existing approaches to secrets management were not designed for today’s hybrid and cloud-first environments. They evolved to solve earlier problems, often optimizing for either control or convenience, but rarely both at the same time.
Self-Hosted Vaults and HSMs
On-premises vaults and hardware security modules offer strong isolation and direct ownership of keys and secrets. For regulated environments, this level of control has long been reassuring.
The trade-off is operational overhead. These systems require careful sizing, ongoing maintenance, patching, availability planning, and specialized expertise. Scaling them across regions or cloud environments introduces additional complexity, making them difficult to align with modern delivery models.
Cloud-Hosted Secrets Platforms
Cloud-based secrets services reduce operational burden and integrate easily with modern infrastructure. For many use cases, especially in cloud-native environments, they can be a natural fit.
However, many of these platforms are built around a provider-controlled model, where encryption keys are held, managed, or technically recoverable by the service operator. Even when access is tightly restricted, the architecture still depends on trust in the provider. For sensitive credentials, that trust requirement becomes a limiting factor.
Key Splitting and Escrow Models
Some solutions attempt to bridge the gap by splitting keys across systems or parties. While this can reduce risk, many implementations still recombine keys during cryptographic operations or rely on static fragments.
These approaches improve resilience, but they do not fully eliminate the possibility of exposure. The core issue remains unresolved: a complete key can exist, even briefly, within the system.
Across these models, the pattern is consistent. Enterprises are asked to choose between strong control and operational simplicity, rather than being able to achieve both through design.
What a Cloud-Delivered Security Architecture Needs
Making secrets management available as a service without compromising security requires more than incremental improvements to existing models. It demands a different architectural foundation, built around provable control rather than assumed trust.
At a conceptual level, a SaaS-based security architecture must provide:
- Cryptographic separation between provider and organization, ensuring the service operator cannot access or reconstruct secrets, certificates, or encryption keys.
- Distributed control with no single point of compromise, so sensitive material never exists in full within one system, environment, or provider.
- Zero-knowledge enforcement by design, where the provider operates the platform without visibility into the data it protects, independent of policies or permissions.
- Security guarantees that persist under failure conditions, including platform compromise, insider threat, or external pressure.
- Operational simplicity consistent with SaaS, supporting scale, automation, and modern infrastructure without reintroducing on-prem complexity.
Only when these requirements are met can secrets management operate safely in a SaaS environment without forcing enterprises to trade control for convenience.
Zero-Knowledge Encryption
The limitations of traditional approaches point to a broader issue. The problem is not that secrets management cannot be delivered through SaaS. It is that most architectures were never designed to separate how security is provided from who retains control.
A SaaS security model does not need to centralize sensitive material to be effective. It can centralize orchestration, automation, and availability while leaving cryptographic ownership distributed and outside the provider’s reach. Under a zero-knowledge architecture, the platform coordinates secure operations and enforces policy without ever possessing the secrets it protects. Control is enforced through cryptographic design instead of permissions, assurances, or contractual boundaries.
This shift reframes SaaS entirely. Rather than asking enterprises to trust a provider with their most sensitive assets, it allows them to retain direct control over secrets, certificates, and encryption keys.
Akeyless: Zero-Knowledge Architecture in Practice
Akeyless was designed to implement a zero-knowledge architecture for secrets management in real-world enterprise environments.
Distributed Control Without Centralized Keys
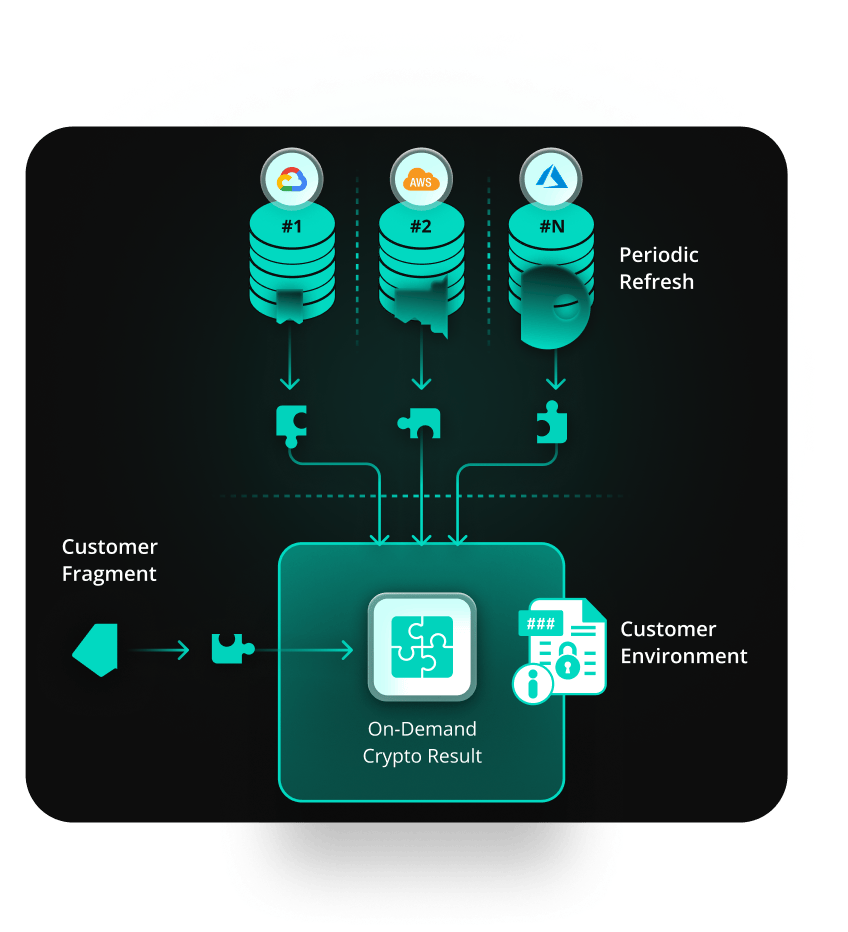
At the core of the platform is Distributed Fragments Cryptography™ (DFC™), a patented and NIST FIPS 140-2 validated approach that protects secrets, certificates, and encryption keys by fragmenting cryptographic material across multiple regions and cloud providers. No single system ever holds a complete key, and cryptographic operations such as encryption, decryption, and signing, occur without recombining fragments.
The fragments themselves are refreshed continuously, making it exceedingly difficult for attackers to exploit static vulnerabilities. This contrasts sharply with traditional key-split methods, which recombine keys for operations, creating windows of potential risk.
Secure by Design
To ensure cryptographic ownership remains with the organization, one fragment always stays within the organization’s environment, with only outbound connections to the Akeyless service. This means Akeyless can orchestrate secrets management as a SaaS platform without ever accessing the secrets it protects. Even in the event of a platform compromise, fragments remain incomplete and unusable.
The outcome is SaaS-level convenience with hardware-level security.
Why This Matters in Practice for Regulated Enterprises
For regulated organizations, architectural decisions directly affect what can be deployed in production, not just what looks good in an evaluation. A zero-knowledge approach changes what is possible with a SaaS-based secrets management solution.
- Enables SaaS adoption without sacrificing control: Sensitive secrets, certificates, and encryption keys remain under organizational ownership.
- Reduces operational overhead compared to self-managed systems: Teams avoid the cost and complexity of maintaining on-prem vaults and hardware while still meeting strict security requirements.
- Improves security posture through cryptographic enforcement: Distributed fragmentation and continuous refresh protect against evolving threats without creating windows where full keys can be exposed.
- Simplifies regulatory and risk reviews: When provider access is cryptographically impossible rather than procedurally restricted, security claims are easier to validate and defend.
- Scales cleanly across regions and environments: The architecture supports global deployment and growth without introducing new trust boundaries or operational bottlenecks.
For industries such as financial services, healthcare, and critical infrastructure, this shift from trust-based models to provable security allows organizations to modernize security architectures that were previously locked into on-prem constraints.
Secrets Management Without Compromise
For many enterprises, the challenge of secrets management has always been architectural. Traditional models forced a choice between control and convenience, keeping secrets, certificates, and encryption keys tied to on-prem systems even as everything else moved forward.
Akeyless removes that trade-off. Through its zero-knowledge architecture built on Distributed Fragments Cryptography, Akeyless enables organizations to modernize secrets management while retaining full control over their most sensitive assets, without introducing new trust or compliance risk.To learn more, read the solution brief or schedule a demo to see how Akeyless works in practice.




