
Security
The Secrets Behind Uber’s BreachJoin our CEO Oded Hareven and Admiral Michael S. Rogers of Team8 as they discuss the implications behind the recent Uber breach.

Security
The Secrets Behind Uber’s BreachJoin our CEO Oded Hareven and Admiral Michael S. Rogers of Team8 as they discuss the implications behind the recent Uber breach.

Technical Definitions
Anomaly Detection: Definition and Best PracticesAnomaly Detection: Definition, Techniques and Best Practices for Enhanced Security. Read more in out blog.

Product Updates
Akeyless and ServiceNow: Optimize IT WorkflowsThis blog explores the integration of Akeyless with ServiceNow, highlighting how it enhances security, centralizes management, and streamlines workflows for IT administrators managing access controls and secrets.

Technical Definitions
What is Risk Posture Management?What is Risk Posture Management? Managing risk posture is a critical aspect of maintaining security for any organization. Read more here.

Technical Definitions
What is Secrets Scanning? Your Guide to Protecting Sensitive DataWhat is Secrets Scanning? Read more about this security strategy aimed at locating obscured sensitive data such as passwords and API keys.

DevOps | InfoSec
Compare Akeyless vs AWS Secrets Manager in 2024This blog offers a detailed comparison between AWS Secrets Manager and Akeyless, highlighting their capabilities in secrets management for modern enterprises, focusing on security, scalability, and integration in a multi-cloud environment.

DevOps | InfoSec
Akeyless: The Leading HashiCorp Vault AlternativeIn this video blog, Sam Gabrail explains why Akeyless leads over HashiCorp Vault, with features like automated rotation and universal identity.

DevOps | InfoSec | Security
Mastering Secure Secrets: The Akeyless Guide to Automated Credential RotationIntroduction Maintaining data encryption and security is crucial for any organization. One effective strategy is the proper management of keys and credentials, particularly through automated credential rotation. This method ensures the ongoing security and integrity of sensitive information. Akeyless offers advanced capabilities in securing secrets and automating credential rotation. In this blog post, we will […]
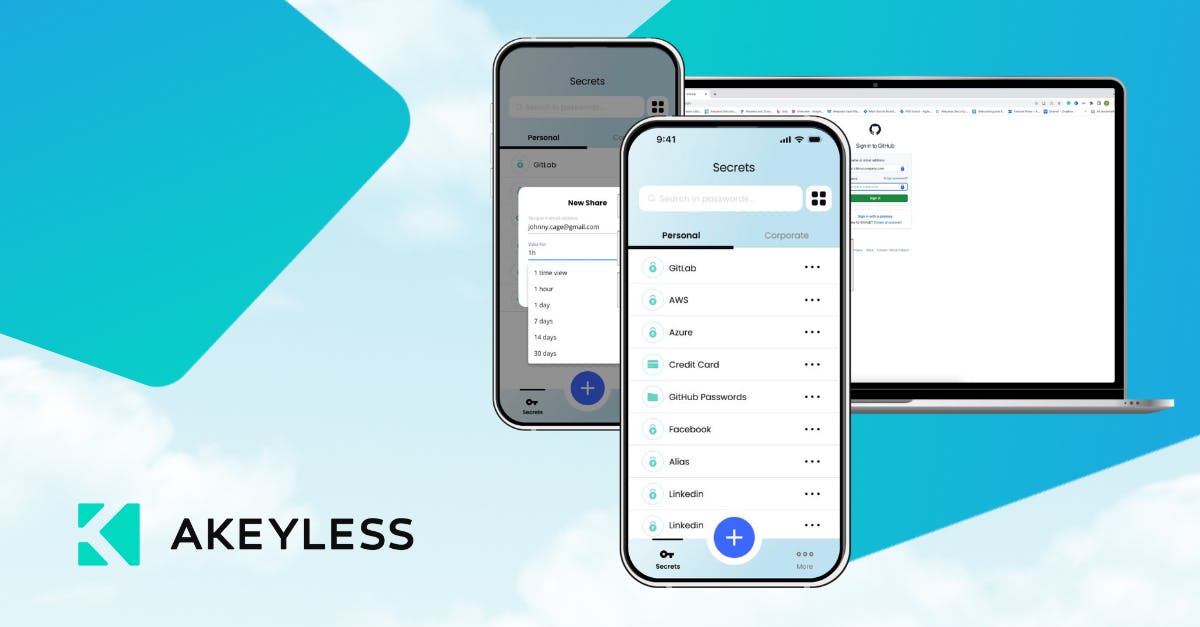
DevOps | InfoSec | Product Updates
An In-Depth Look at the Akeyless Password ManagerDiscover how Akeyless Password Manager enhances enterprise security with advanced encryption and comprehensive features, ensuring robust protection and streamlined password management for businesses.

News
Akeyless Security Simplifies Secrets Management for Microsoft Azure CustomersAkeyless Security, the leading Vaultless® SaaS secrets management solution, today announced that its platform is now available on the Microsoft Azure Marketplace. This development allows Azure customers to easily find, purchase, and deploy Akeyless platform directly through the marketplace, while also helping them meet their Microsoft Azure Consumption Commitments (MACC).

Key Management Interoperability Protocol (KMIP) serves as a cornerstone in the digital security domain, particularly in the management of encryption keys across diverse cryptographic systems. Read more.

A Key Management System (KMS) that supports multi-cloud is a critical solution for a unified approach to manage encryption keys across various cloud environments. But what does it entail, and why is it crucial for modern cloud defense strategies?