
DevOps | InfoSec | Security
Akeyless Tutorial Series: Next-Level Skills for Secrets ManagementThis Akeyless SaaS Secrets Management Tutorial will have you operating at a whole new level of secrets mastery in no time.

DevOps | InfoSec | Security
Akeyless Tutorial Series: Next-Level Skills for Secrets ManagementThis Akeyless SaaS Secrets Management Tutorial will have you operating at a whole new level of secrets mastery in no time.

DevOps | InfoSec | News
Rotate or Breach: Security Insights from CloudflareRotate or Breach: Security Insights from Cloudflare highlighting the critical necessity of automating secrets rotation,
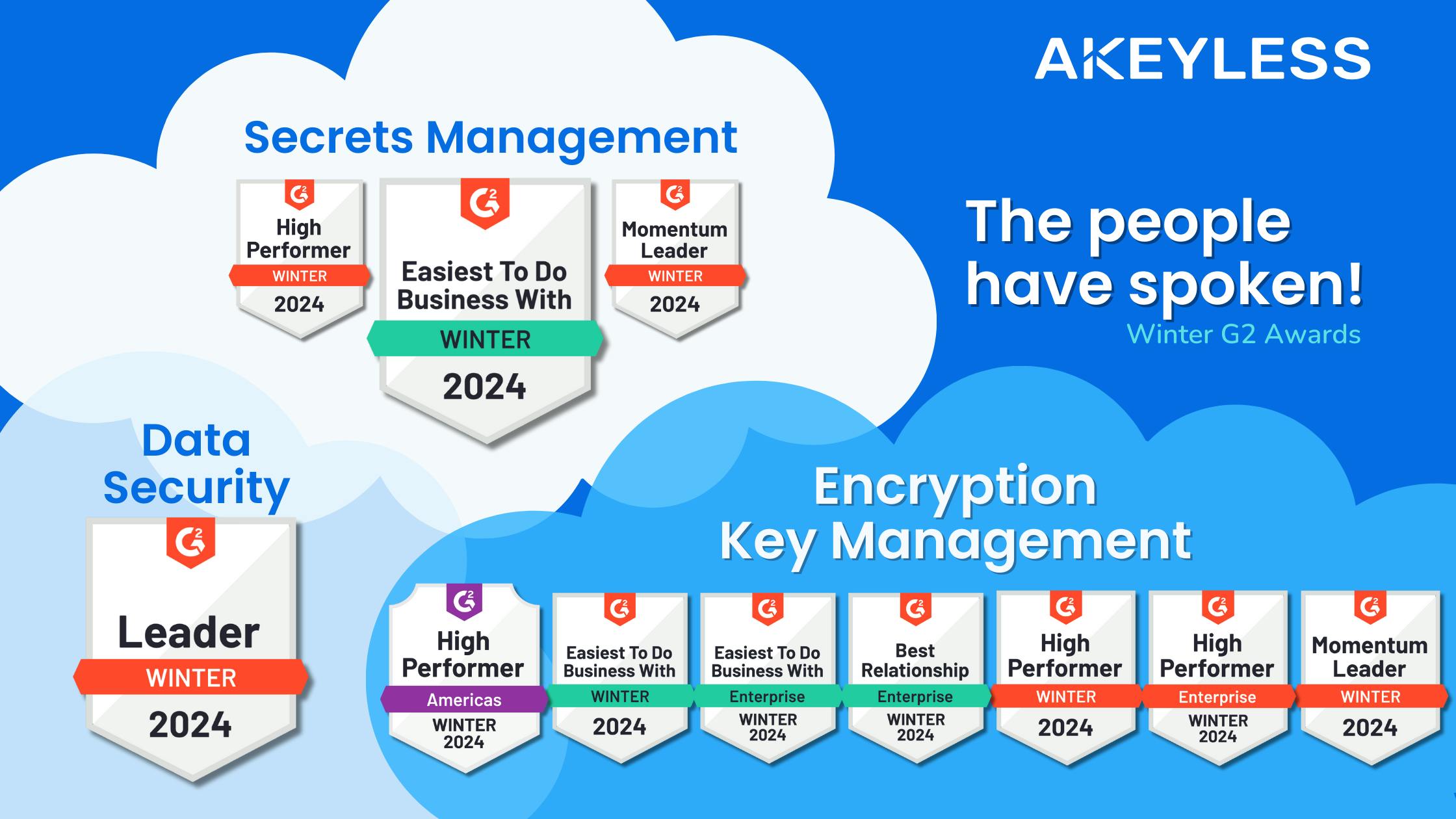
News
The People Have Spoken: Akeyless Celebrates Winter G2 AwardsThe People Have Spoken: Akeyless Celebrates Winter G2 Awards reflecting technological innovation and customer trust and satisfaction.

DevOps | InfoSec | Security
Akeyless SaaS Secrets Management 101: Video TutorialThis Akeyless SaaS Secrets Management 101 Tutorial will have you operating at a whole new level of secrets mastery in no time.
DevOps | Security
How to Solve the Secret Zero Problem with AkeylessLet's do a deep dive into the secret zero problem: what it is and how you can solve it with an innovative new approach.

DevOps | InfoSec
Access Control: Enhancing Compliance and Security for Secrets ManagementDelve into the intricacies of access control in this blog, covering its challenges, best practices, and strategies for enhancing organizational security and compliance

DevOps | InfoSec
How Akeyless Universal Secrets Connector is Revolutionizing Multi-Cloud EnvironmentsDiscover Akeyless USC, the unified solution for centralizing and securing secrets in today's multi-cloud environment, enhancing compliance and operational efficiency.

Product Updates
Elevating Access Management with Akeyless OIDCIn today’s digital world the ability to sign in quickly and safely across different platforms is essential. OpenID Connect (OIDC) has emerged as the preferred choice for streamlining the login process for both users and developers by allowing applications to confirm who users are based on checks done by a trusted service. OIDC also builds […]

News
Insider Insights: The 2024 State of Secrets Management Survey ReportThe 2024 State of Secrets Management report exposes the perils of Secrets Sprawl. Drawn from insights of 200 leading security professionals, it reveals how overlooked vulnerabilities can lead to major breaches, a crucial read for enterprises striving to safeguard their digital assets.

Product Updates
Akeyless Universal Secrets Connector: A Secrets Manager of ManagersDiscover the power of External Secrets Manager with Akeyless. Simplify secrets management across multiple platforms and clouds, centralize control, enhance visibility, and ensure compliance.

DevOps | InfoSec | Security
CISOs Under Fire: The New Legal Frontline in CybersecurityRecent actions by the U.S. Securities and Exchange Commission (SEC) represent a significant moment for CISOs everywhere. On October 30, 2023, the SEC announced it was bringing charges against Austin, Texas-based software company SolarWinds and its CISO, Timothy G. Brown.

InfoSec | Security
Protecting Sensitive Data with Secrets ManagementThis in-depth guide delves into the critical role of secrets management in protecting sensitive data. The post outlines essential principles for effective management and discusses tools and techniques to support these practices.